Cybersecurity for State and Local Governments
Take Control of Your Attack Surface
State, local and education (SLED) organizations need robust, secure and scalable security.
With Tenable, SLED agencies can implement statewide exposure management across their attack surfaces to reduce risk and ensure complete network visibility.
Learn MoreRequest a DemoProtecting SLED Agencies
Discover Your Exposures
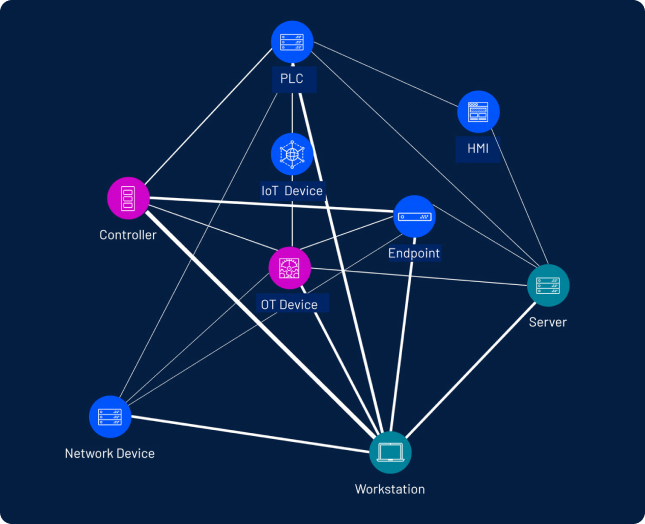
Discovery is key. Find all assets and vulnerabilities across your network — from IT to OT, cloud to containers, web apps to Active Directory (AD). Continuous monitoring ensures your team captures all assets and vulnerabilities. View and manage all your findings from a single, unified platform.
Read the eBook: Protecting State and Local Governments from the Cyber Threats of Tomorrow
Learn More: Tenable One
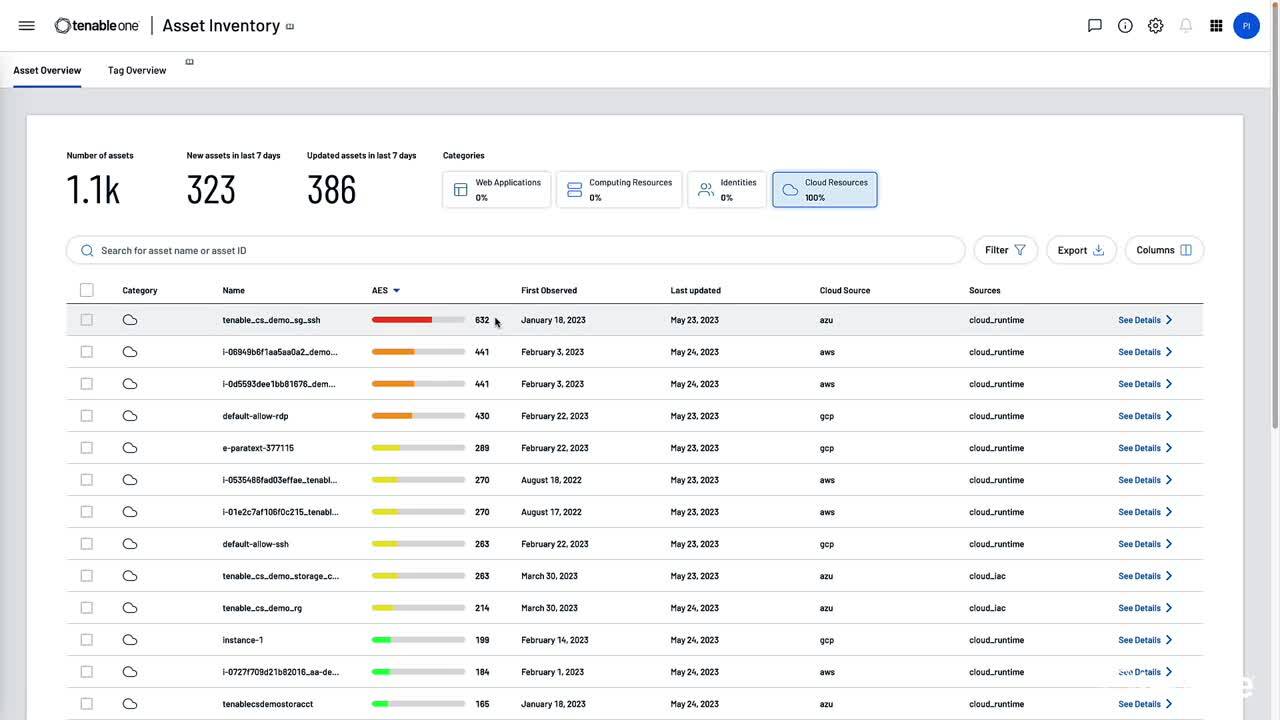
Simplify the Complexities of Hybrid Cloud Security. This 1:15 video demonstrates how Tenable One identifies and closes security gaps across hybrid environments.
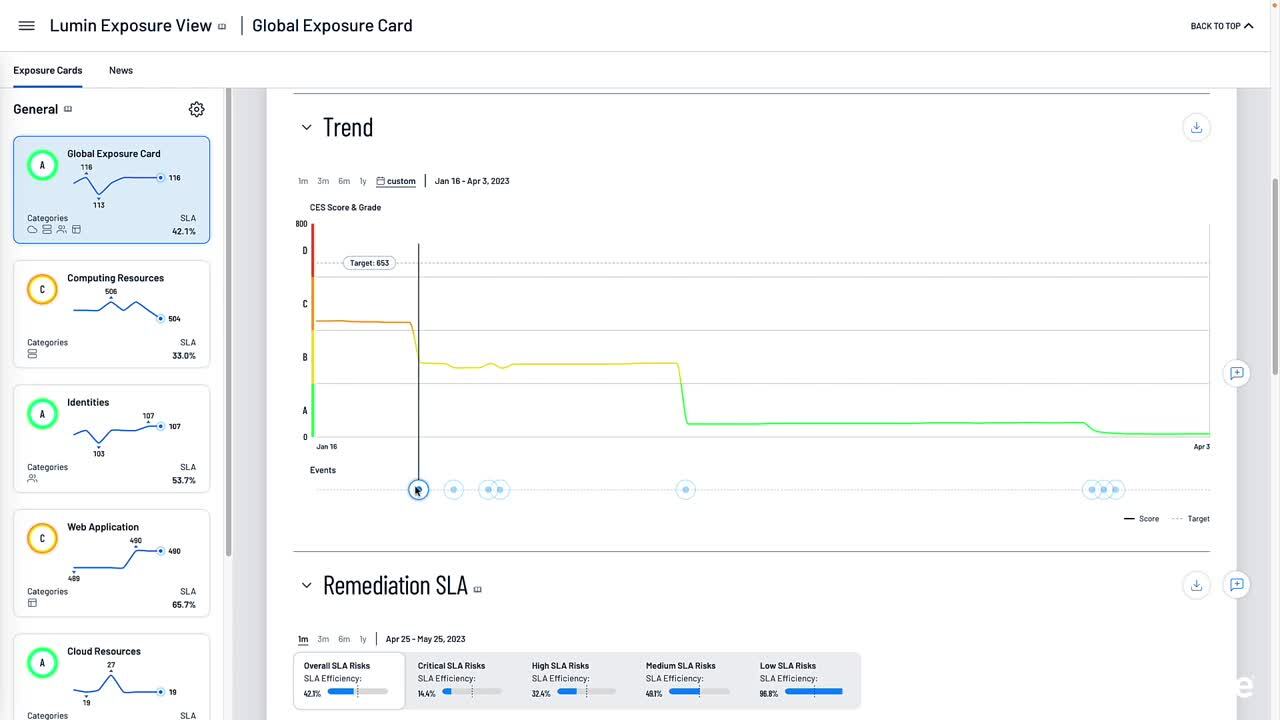
Tenable One Exposure View. Watch this 1:10 video to learn how Tenable One reduces risk across your hybrid environments with end-to-end hybrid attack surface protection.
Stay Ahead of Your Adversaries
Attack path visualizations and prioritization capabilities provide a pre-emptively focused response to remove paths attackers may take.
Learn More: Attack Path Analysis
Safeguard OT Networks and Cyber-Physical Systems
You can’t defend what you can’t see. If your OT assets are separate from your IT security, it can create blind spots. Supporting state and federal mandates for safeguarding critical infrastructure, Tenable OT Security offers comprehensive protection of OT environments to maximize the safety and reliability of SLED operational technology environments.
Download the White Paper: 5 OT Security Use Cases for the DoD
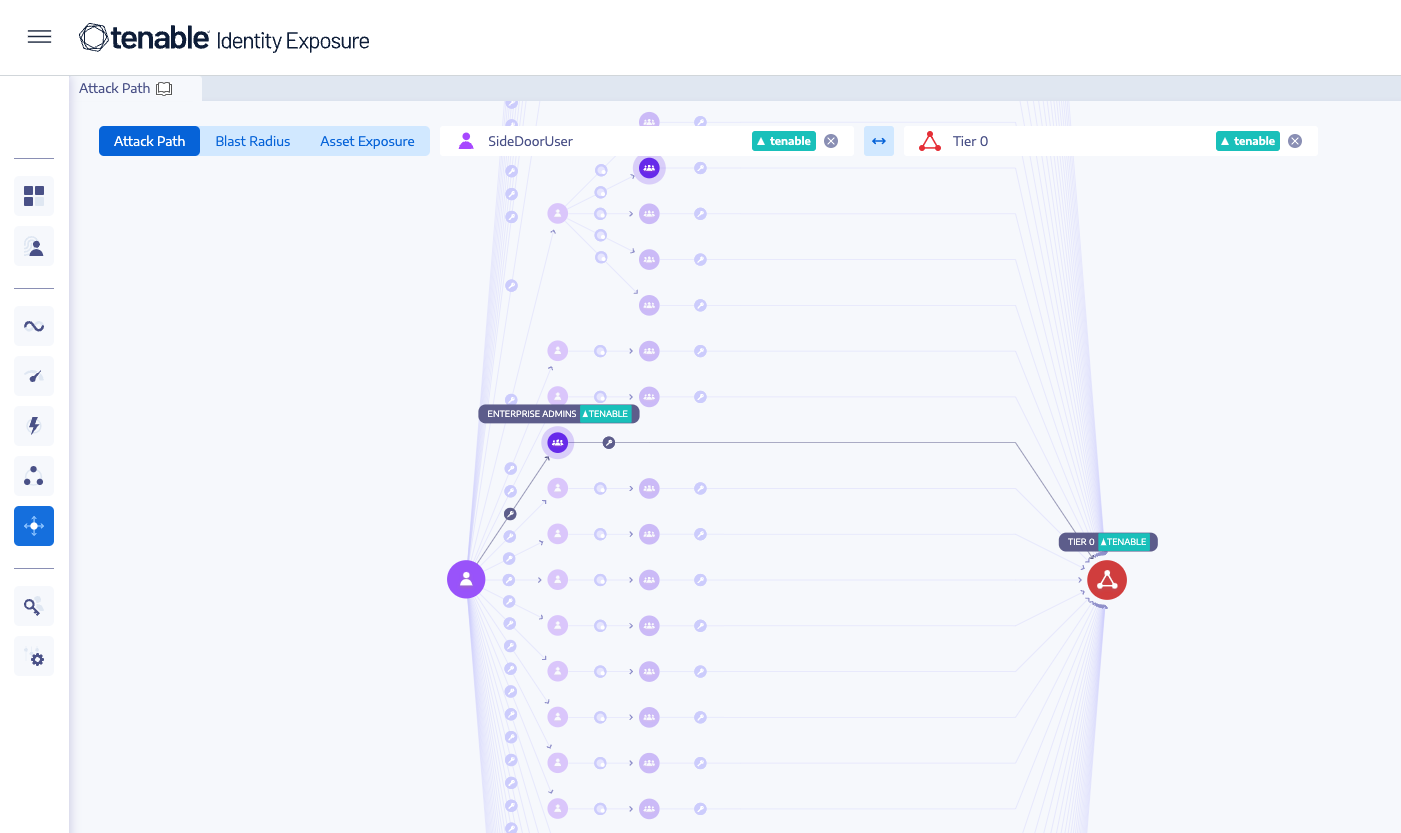
Stop Ransomware With Identity Security Driven by Zero Trust
Active Directory (AD) is the master key to your agency’s system and network privileges, making it a prime target for attackers and a key pathway for ransomware attacks. Tenable Identity Exposure protects this critical attack vector with comprehensive AD protection to stop lateral movement, privilege escalation and proactively identify and prevent attacks.
Download the White Paper: Government Attacks: Proactively Secure Your Infrastructure
Watch the Webinar: Strengthen the Effectiveness of Your Identity Security Program with Zero Trust Maturity
Whole-of-State
Cybersecurity with Tenable
Adopting a whole-of-state approach helps solve resource and budget constraints at the local level while establishing a unified, collaborative cyber defense across the state and its various departments and agencies. Learn how Tenable supports whole-of-state security.
Read the Solution Brief: Meeting SLCGP Requirements
Read the Blog: Protecting Local Government Agencies
57% of cybersecurity leaders plan to offer or consume whole-of-state cybersecurity services in the coming year.
Source: NuHarbor Security (2023). 2023 SLED Cybersecurity Survey
State and Local Cybersecurity Grant Program
Funding is available through the State and Local Cybersecurity Grant Program (SLCGP) to help SLEDs tackle new and evolving cyber threats, and implement a whole of state approach.
The program helps states, local governments, rural areas and territories address cybersecurity risks and threats to their information systems. Tenable solutions enable SLEDs to meet year 2 program objectives around continuous testing, evaluation and assessments of networks, and help agencies check the box on all 16 required elements of the SLCGP Cybersecurity Plan.
Learn More: State and Local Cybersecurity Grant Prgram (SLCGP)
Read the Blog: How to Meet SLCGP Objectives
Read the Solution Brief: SLCGP + Tenable



FedRAMP and StateRAMP Authorized
Tenable Vulnerability Management's FedRAMP & StateRAMP authorizations ensure it meets the high security standards of federal, state, and local governments, giving agencies security and compliance assurance and saving time, costs and resources on the adoption and evaluation of our solutions.