by Ron Gula
August 28, 2015
When deploying Cisco devices on a network, one of the most important issues that an analyst can overlook is applying proper security controls before the device is deployed into production. Hardening network devices can be a time-consuming process that involves patching, modifying configurations, and testing the effectiveness of security controls. Attackers continually seek out new exploits and weaknesses in network devices to gain unauthorized entry into a network. Once a network had been breached, an attacker has access to execute malicious code, steal confidential data, and alter user accounts. Any network entry points that are misconfigured or lack proper security controls undermine the security of an organization’s entire network.
The CIS Cisco Auditing dashboard is designed to assist the analyst in measuring the Center for Internet Security (CIS) benchmark compliance of Cisco routers and firewalls. This allows issues to be analyzed quickly by leveraging an agent-less audit. Tenable has many CIS-certified benchmark audits for Cisco devices that can be downloaded from Tenable’s Customer Support Portal. In addition, this dashboard also provides vital information that will enhance visibility, increase security awareness, and aid in strengthening an organization’s security posture.
Several components within this dashboard leverage the CISCO plugin family of vulnerability checks, which provides a comprehensive overview of Cisco-related vulnerabilities. The first column presents a matrix of vulnerabilities by severity found to exist in Cisco devices. In addition, a table that shows vulnerability checks that detect outdated software and security vulnerabilities is also included. Other components included within this dashboard present a percentage of overall compliance checks completed, along with a table of common security setting vulnerabilities that have been detected on Cisco devices.
All vulnerabilities should be reviewed to determine the impact and risk to an organization. Network devices that have critical, high, and medium severity vulnerabilities should be considered high-risk priorities for an organization to address and remediate.
The dashboard and its components are available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, assurance report cards and assets. The dashboard can be easily located in the Tenable.sc Feed under the category Compliance & Configuration Assessments.
The dashboard requirements are:
- Tenable.sc 4.8.2
- Nessus 8.5.1
- Compliance Data
Tenable.sc Continuous View (CV) identifies the biggest risks across the entire enterprise, and Tenable’s products allow for the most comprehensive and integrated view of network health. Nessus and Tenable.sc are continuously updated with information about advanced threats and zero-day vulnerabilities, as well as new types of regulatory compliance configuration audits, allowing organizations to maintain a secure network.
The dashboard contains the following components:
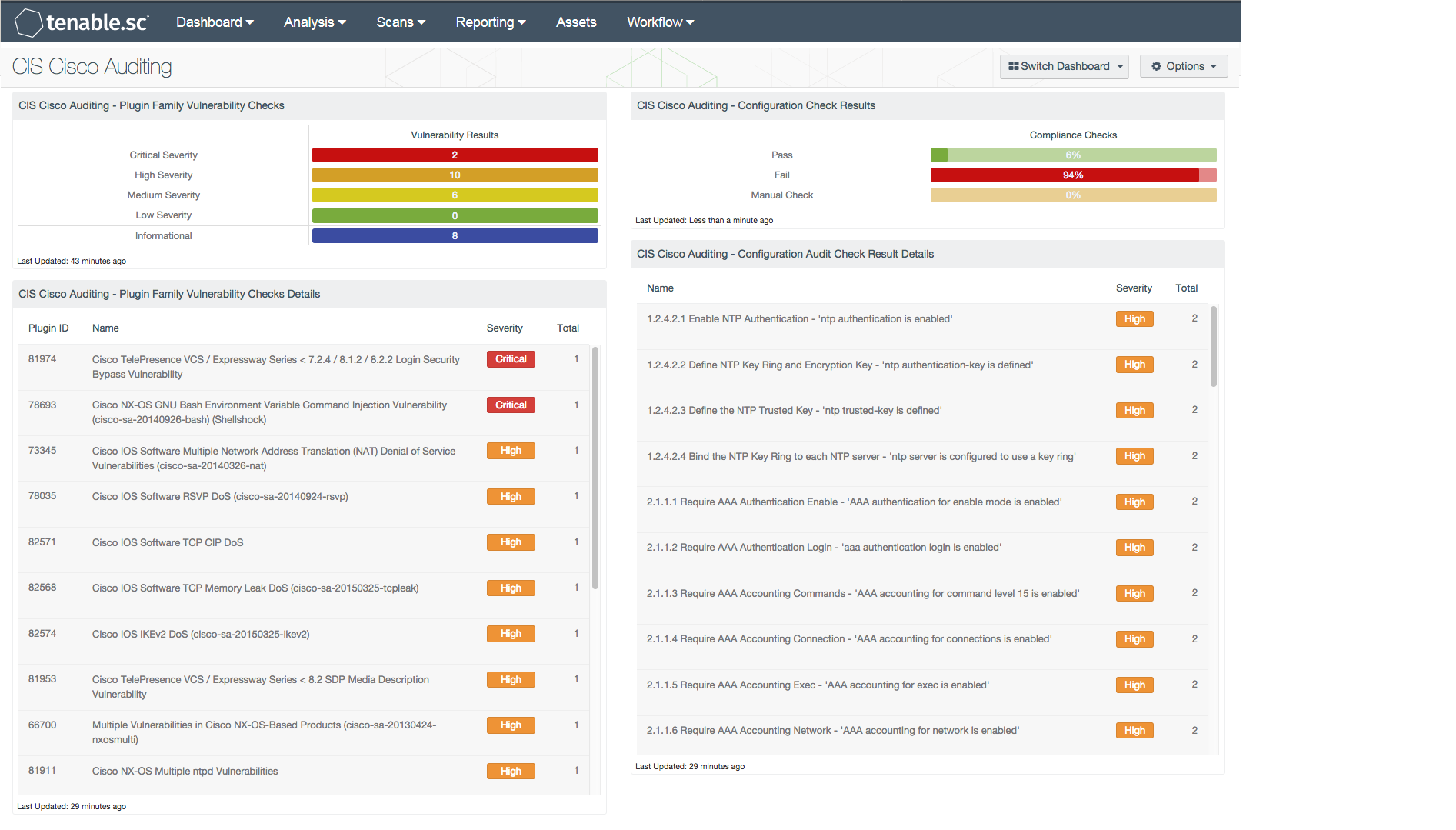
- CIS Cisco Auditing - Plugin Family Vulnerability Checks - This matrix presents vulnerability results for the CISCO plugin family sorted by severity. The results will provide targeted information on outdated software and relevant security patches that need to be applied to a Cisco device. Any network device with critical, high, or medium severity levels vulnerabilities should be the first priority of an analyst to review and mitigate, as this provides attackers a way to comprise an organization’s network.
- CIS Cisco Auditing - Plugin Family Vulnerability Checks Details - This table presents the top 100 critical, high, and medium severity vulnerabilities detected from the CISCO plugin family. The table is sorted so that the highest severity level is at the top, which aids in prioritizing mitigation efforts. Any outdated software and security vulnerabilities will be presented within this table along with the corresponding plugin ID, plugin name, description of the vulnerability, severity level, and possible solutions to mitigate the vulnerability. Each vulnerability check includes detailed information on the respective vulnerability that the analyst can immediately drill down into. This table provides targeted information the analyst needs to mitigate existing vulnerabilities, and assist in preventing unauthorized access to an organization’s network.
- CIS Cisco Auditing - Configuration Check Results - This matrix provides information on CIS-based Cisco compliance checks. Each check cross-references with the auditFile|cisco keyword search, and the plugin text search for “cissecurity.org”. The checks are presented as “Pass” for informational, “Fail” for high, and “Manual Check” for medium severity levels. The ratio of the percentage of overall checks completed against the checks that are marked with the respective severity level are displayed within this matrix. An analyst can click on the appropriate matrix cell to obtain additional information on specific vulnerabilities. Compliance checks with a medium severity levels require a manual review to determine whether the check has passed or failed.
- CIS Cisco Auditing - Configuration Audit Check Result Details - This component presents the top 100 Cisco compliance vulnerabilities detected on Cisco devices. The table is sorted so that the highest number of vulnerable hosts are listed at the top. Nessus audit capabilities are leveraged by this table in performing a cross-reference check with the auditFile|cisco keyword search, and the plugin text search for “cissecurity.org”. Examples include, but are not limited to, modifying firewall ACLs, logging access attempts, and identifying services that should be disabled. Any high severity level vulnerabilities displayed have failed that associated compliance check. Any medium severity level vulnerabilities require a manual check by the analyst to determine the risk to an organization. The analyst can click on the Browse Component Data to obtain additional information about the respective compliance check. This table presents targeted information the analyst needs to mitigate existing compliance misconfigurations and assist in preventing unauthorized access to an organization’s network.