by Ron Gula
May 17, 2016
Monitoring and logging the volume of log data from network traffic on a daily basis can be overwhelming for any organization to effectively manage. A centralized repository to collect and manage logs can provide organizations with accurate, real-time information needed to address and remediate issues before critical systems are affected. Information presented within this dashboard provides a real-time view of new hosts, connections, and network traffic across the enterprise.
With the amount of devices, servers, and workstations on a network today, logging and analyzing every log in real time is nearly impossible. Without knowing what to log, where to store the logs, and how long logs need to be to retained, organizations may miss indications of potentially unauthorized activity. Unfortunately, many organizations rarely look at event logs until a major security incident occurs. Logs can provide valuable information from sources such as network traffic generated from critical network devices such as routers, switches, and firewalls. Forwarding logs to a centralized log repository will improve visibility, and can provide the critical information needed to detect potential data breaches, attacks, and malicious hosts that may be on the network. Additionally, this information can assist security teams in proactively addressing any misconfigured devices and/or weak security policies currently in place. Many regulatory and compliance frameworks such as the National Institute of Standards and Technology (NIST) Special Publication 800-92 and the Center for Internet Security (CIS) Critical Security Controls (CSC) Control 6, address log management and the need to establish policies and procedures to retain and secure logs.
This dashboard provides a comprehensive look at network traffic. When the Tenable Passive Vulnerability Scanner (PVS) is configured to send syslog messages to the Tenable Log Correlation Engine (LCE), LCE normalizes the logs and creates a series of events using the prefix "PVS". Examples of network traffic that PVS analyzes may consist of new host activity, data transfers, and other types of passively discovered events. LCE provides organizations with the ability to collect all logs, user events, and network traffic. Analysts can use this information to detect file upload/downloads, social network, remote access, and many other user-based events. Examples of hosts that may have been compromised include information such as large data transfers, botnet activity, and related intrusion activity. Several components provide the latest information happening on the network such as new network connections, newly opened ports, and encrypted network sessions. Having an effective log management strategy is a critical component of any security program. Using this dashboard, organizations will be able to monitor network activity for any unauthorized activity, and have the information needed to mitigate future attacks.
This dashboard is available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The dashboard can be easily located in the SecurityCenter Feed under the category Monitoring. The dashboard requirements are:
- SecurityCenter 5.3.1
- PVS 5.0.0
- LCE 4.8.0
Tenable SecurityCenter Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. The Tenable Log Correlation Engine (LCE) correlates real-time events, such as port scanning, and then performs analysis to discover vulnerabilities and indicators of compromise (IOC). The Tenable Passive Vulnerability Scanner (PVS) is able to collect network metadata through passive monitoring, finding inappropriate activity, identifying assets and vulnerabilities from network traffic, and detecting hard to profile assets including Virtual, BYOD, and SCADA. SecurityCenter CV allows for the most comprehensive and integrated view of network health.
The following components are included in this dashboard:
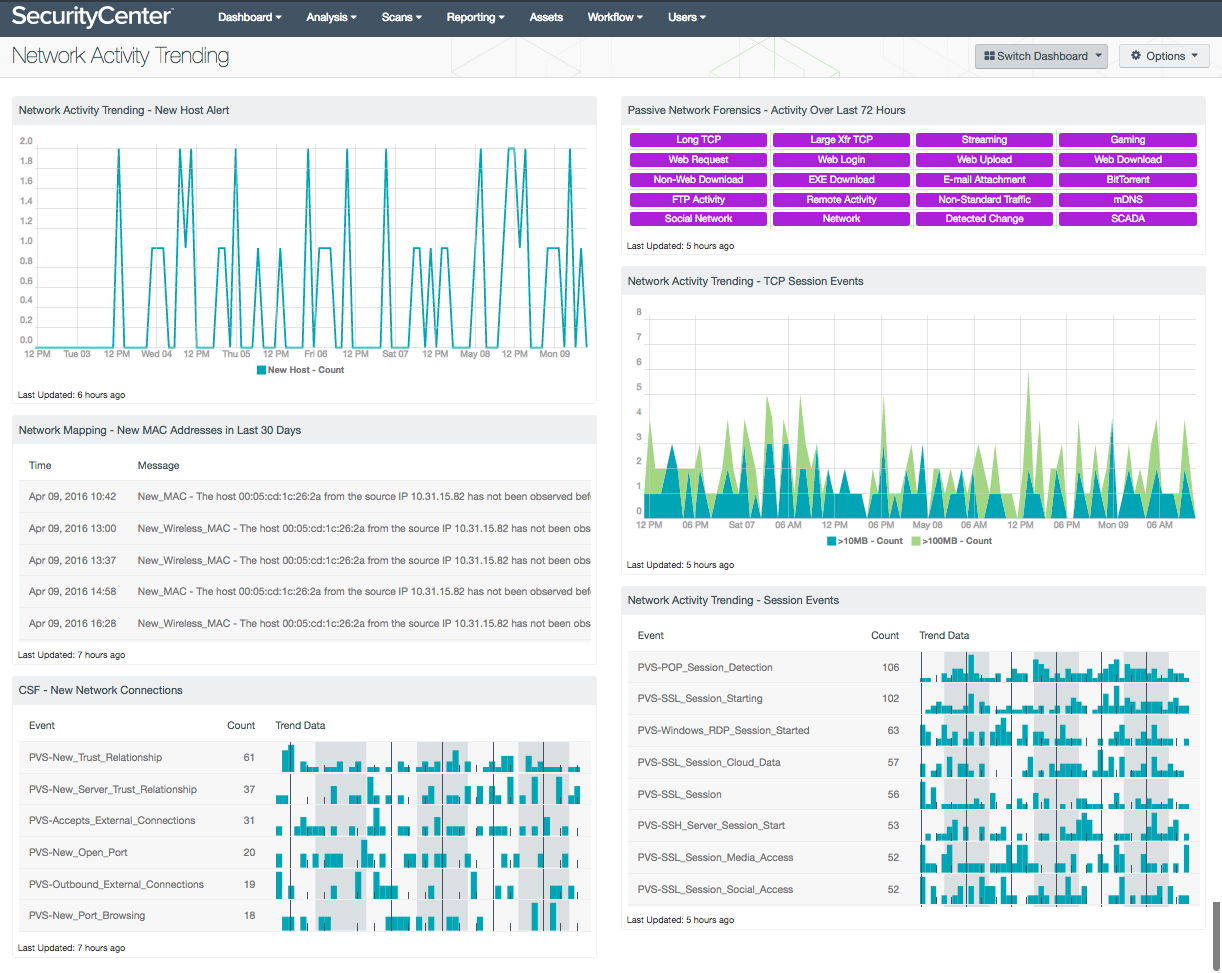
- Network Activity Trending - New Host Alert: This chart presents a trend of newly detected hosts within the last seven days. Using this component, analysts can quickly investigate new hosts to determine whether the host is authorized. Note that this component relies on PVS detections being forwarded to LCE.
- Network Mapping - New MAC Addresses in Last 30 Days: This table lists all the new MAC addresses that have never been observed before on the network, and that were first observed in the last 30 days. Tenable's LCE sets the New_MAC event when a new, never-before-seen MAC address is observed on the network. This table reports those New_MAC events, displaying the time observed and the raw syslog text, which contains the new MAC address and its associated IP address. Discovering new hosts on the network can assist an organization in maintaining an accurate inventory and detecting rogue devices.
- CSF - New Network Connections: This table presents a list of new network connections discovered by PVS and logged by LCE. Events displayed within this table present information on new trust relationships, internet connections, newly opened ports, and external connections. The analyst can drill down and select the syslog events to obtain additional information on a detected event. Uncovering new network connections can assist with detecting rogue and unauthorized connections on a network.
- Passive Network Forensics - Activity Over Last 72 Hours: This matrix presents indicators of network activity that has occurred in the last 72 hours, including long TCP sessions (more than 47 hours), TCP sessions with large data transfers (1GB or more), streaming traffic (such as Netflix or XM Radio), gaming traffic (such as logins to gaming networks), web activity (requests, logins, uploads, and downloads), non-web downloads, EXE downloads, e-mail attachment detections, BitTorrent activity, FTP activity, remote activity (SSH, VNC, or RDP), non-standard traffic (such as non-HTTP traffic on port 80), mDNS traffic, and SCADA traffic. Indicators are also presented for activity that falls under the event types of social network activity, general network activity, and detected changes.
- Network Activity Trending - TCP Session Events: This chart presents an overview of detected TCP session events that have transferred at least 10MB or more. The Passive Vulnerability Scanner (PVS) has the ability to observe active TCP sessions on the network. Information presented within this dashboard includes files and other data being transferred across the network over the course of minutes, hours, and days. Analysts can modify this component to add TCP session events ranging from 1MB to over 1GB in size, and can be modified per organizational requirements. In addition, the Tenable Network Monitor and Tenable NetFlow Monitor also have normalized events that can be added to this component to observe additional TCP session data transfers.
- Network Activity Trending - Session Events: The Session Events table presents a list of network sessions logged by PVS and forwarded to LCE. The Passive Vulnerability Scanner (PVS) has the ability to detect network session traffic in real time from protocols and services such as SSH, RDP, FTP, and VoIP. Session events presented within this component may also include cloud, social networking, web conferencing, and encrypted sessions. This information can provide analysts with a forensic trail that can be used to detect unauthorized or malicious activity on the network.