by Stephanie Dunn
October 10, 2016
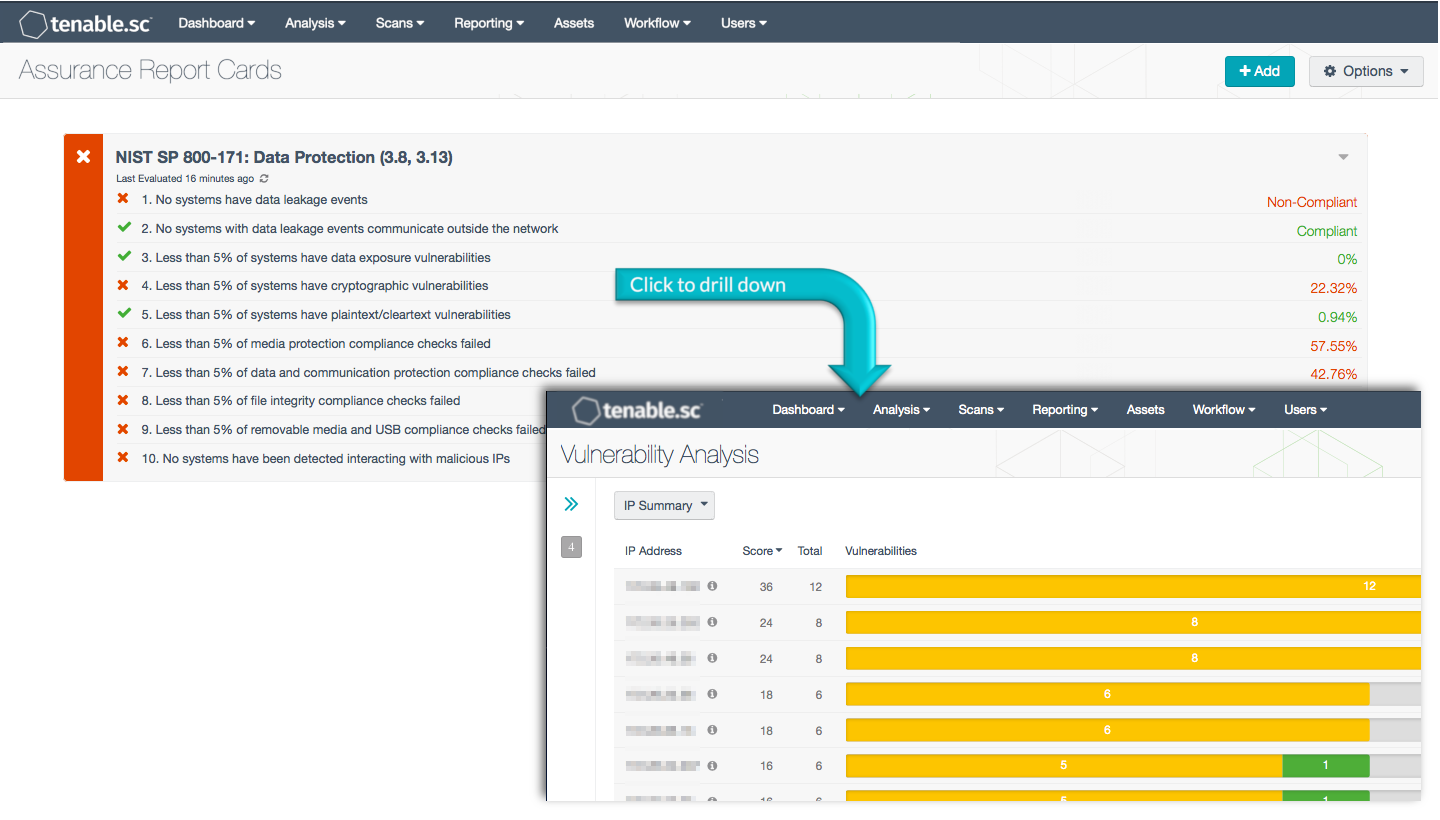
Protecting information system media containing Controlled Unclassified Information (CUI), and monitoring for the use of portable storage devices and removable media is essential to protecting the integrity of information systems. Monitoring organizational communications at external boundaries, as well as key internal boundaries is essential to detect attacks, and potential indicators of attacks. Removable media is commonly used to transfer electronic media from one computer to another. Users who place restricted information on removable media may inadvertently place organizations at risk for data theft or data loss. Access to CUI should be protected and limited to authorized users.
The federal government relies heavily on external service providers and contractors to assist in carrying out a wide range of federal missions. Sensitive but unclassified federal information is routinely processed by, stored on, or transmitted through nonfederal information systems. Failing to properly protect this CUI could impact the ability of the federal government to successfully carry out required missions and functions.
The National Institute of Standards and Technology (NIST) created Special Publication 800-171 "Protecting Controlled Unclassified Information in Nonfederal Information Systems and Organizations" to provide recommended requirements for protecting the confidentiality of CUI. Federal agencies should use these requirements when establishing contracts and agreements with nonfederal entities that process, store, or transmit CUI.
This Assurance Report Card (ARC) aligns with the Media Protection (section 3.8) and System and Communications Protection (section 3.13) families of security requirements in NIST SP 800-171. These families are closely related and requirements focus on the monitoring, control, and protection of organizational communications at the external and key internal boundaries. Examples of key internal boundaries include information system media containing CUI, such as removable devices. Using this ARC, an organization will be better able to identify the use of removable media on information system components, and identify cryptographic mechanisms used to protect the confidentiality of CUI. Organizations will also be able to monitor and protect communications (i.e., information transmitted or received by organizational information systems) at the external and key internal boundaries of the information systems, and take appropriate actions in response.
More details on each of the policy statements included in the ARC are given below. Clicking on a policy statement will bring up the analysis screen to display more details related to that policy statement. The ARC policy statement parameters are guides that can be customized as necessary to meet organizational requirements.
This ARC is available in the Tenable.sc Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. The ARC can be easily located in the Tenable.sc Feed under the category Compliance. The ARC requirements are:
- Tenable.sc 5.4.0
- Nessus 8.4.0
- LCE 6.0.0
- NNM 5.9.0
- Compliance data
Tenable's Tenable.sc Continuous View (CV) is the market-defining continuous network monitoring solution, and can assist an organization in detecting unauthorized and unintended information transfer via shared system resources. Tenable.sc CV is continuously updated with information about advanced threats, zero-day vulnerabilities, and new regulatory compliance data. Active scanning periodically examines systems to find vulnerabilities, and can also make use of audit files to assess compliance. Passive listening provides real-time monitoring to collect information about systems and vulnerabilities. Host data and data from other security devices is analyzed to monitor policy and configuration settings activity. Tenable.sc CV provides an organization with the most comprehensive view of the network and the intelligence needed to secure systems and safeguard sensitive information.
ARC Policy Statements
No systems have data leakage events: This policy statement displays the percentage of total systems where data leakage has been detected. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Any type of data leakage, either intentional or unintentional, can result in the exposure of confidential or private information. This policy statement will help to measure the effectiveness of security controls in place on the network. Systems with detected data leakage should be investigated immediately to minimize potential security risks.
No systems with data leakage events communicate outside the network: This policy statement displays the percentage of systems with reported data leakage events that communicate outside the network. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Data leakage events from systems that are communicating outside the network could be indicative of an intrusion or other malicious activity. Such systems should be investigated immediately to ensure that outside communication is not used for exfiltrating sensitive data from the network.
Less than 5% of systems have data exposure vulnerabilities: This policy statement displays the percentage of total systems that have data exposure vulnerabilities. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Systems with data exposure vulnerabilities are especially susceptible to attacks that could lead to data leakage. Remediation efforts should be targeted to identified systems with data exposure vulnerabilities to ensure that they are not exploited.
Less than 5% of systems have cryptographic vulnerabilities: This policy statement displays the percentage of total systems that have cryptographic vulnerabilities. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Cryptographic vulnerabilities can cause systems to be at risk of exposing information due to improper encryption. Systems could transmit unencrypted data via typically secure protocols without the user’s knowledge. Systems with cryptographic vulnerabilities should be prevented from transmitting data until the vulnerabilities can be remediated.
Less than 5% of systems have plaintext/cleartext vulnerabilities: This policy statement displays the percentage of total systems that have plaintext or cleartext vulnerabilities. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Plaintext password disclosures and cleartext authentication vulnerabilities could allow inadvertent exposure of credentials. These plaintext and clear text vulnerabilities should be addressed before exposed credentials fall into the wrong hands, potentially leading to significant data breaches.
Less than 5% of media protection compliance checks failed: This policy statement displays the percentage of data compliance checks that failed. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Data protection settings may include encryption and access control requirements, among other things. Compliance is measured against policy checks that reference standards such as the Cybersecurity Framework, NIST 800-53, the CIS Critical Security Controls, and the PCI Data Security Standard.
Less than 5% of data and communication protection compliance checks failed: This policy statement displays the percentage of data and communication compliance checks that failed. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Data and communication settings may include disabling IPv6 and enabling secure session settings, among other things to secure communications. Compliance is measured against those policy checks that reference standards such as the Cybersecurity Framework, NIST 800-53, the CIS Critical Security Controls, ISO/IEC 27001, and the PCI Data Security Standard.
Less than 5% of file integrity compliance checks failed: This policy statement displays the percentage of file integrity compliance checks that failed. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. File integrity settings may include proper setup of a file integrity tool and baseline, among other things to ensure file integrity.
Less than 5% of removable media and USB compliance checks failed: This policy statement displays the percentage of removable media and USB compliance checks that failed. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Removable media and USB settings may include requirements to turn off Autoplay and disable USB, among other things to secure USB devices. To protect against data loss or system compromise, removable media compliance issues should be addressed.
No systems have been detected interacting with malicious IPs: This policy statement displays the percentage of total systems that have been detected interacting with known malicious IP addresses. If the policy statement requirement is met, the result is displayed in green; otherwise, the result is displayed in red. Tenable.sc receives a daily and updated list of IP addresses and domains that are participating in known botnets. Using this information, systems on the network that interact with known malicious IP addresses can be detected. Any systems interacting with known malicious IP addresses should be investigated immediately by the organization to minimize security risks.