by Megan Daudelin
March 3, 2016
DROWN (Decrypting RSA with Obsolete and Weakened eNcryption) (CVE-2016-0800) is a vulnerability that affects services that rely on SSL and TLS. The attack exploits a flaw in SSLv2 that allows the attacker to decrypt communications that use SSL or TLS. DROWN is a cross-protocol attack that can decrypt passively collected TLS sessions from up-to-date clients. Unlike other SSL vulnerabilities, DROWN only requires that SSLv2 be enabled on the attacked system and not that SSLv2 be used for communications.
Servers are vulnerable to DROWN if they allow SSLv2 connections, which can be enabled due to misconfiguration or overlooked default settings. Servers can also be vulnerable if they use a private key that is used by any other server that has SSLv2 enabled. Since certificates are commonly reused, a single system with SSLv2 enabled can expose other servers to the same risk. DROWN vulnerability can only be remediated on servers with SSLv2 enabled; client software and browsers cannot be hardened against DROWN. SecurityCenter provides an accurate understanding of the organization’s exposure to DROWN attacks by integrating with Nessus, the Passive Vulnerability Scanner (PVS), and the Log Correlation Engine (LCE).
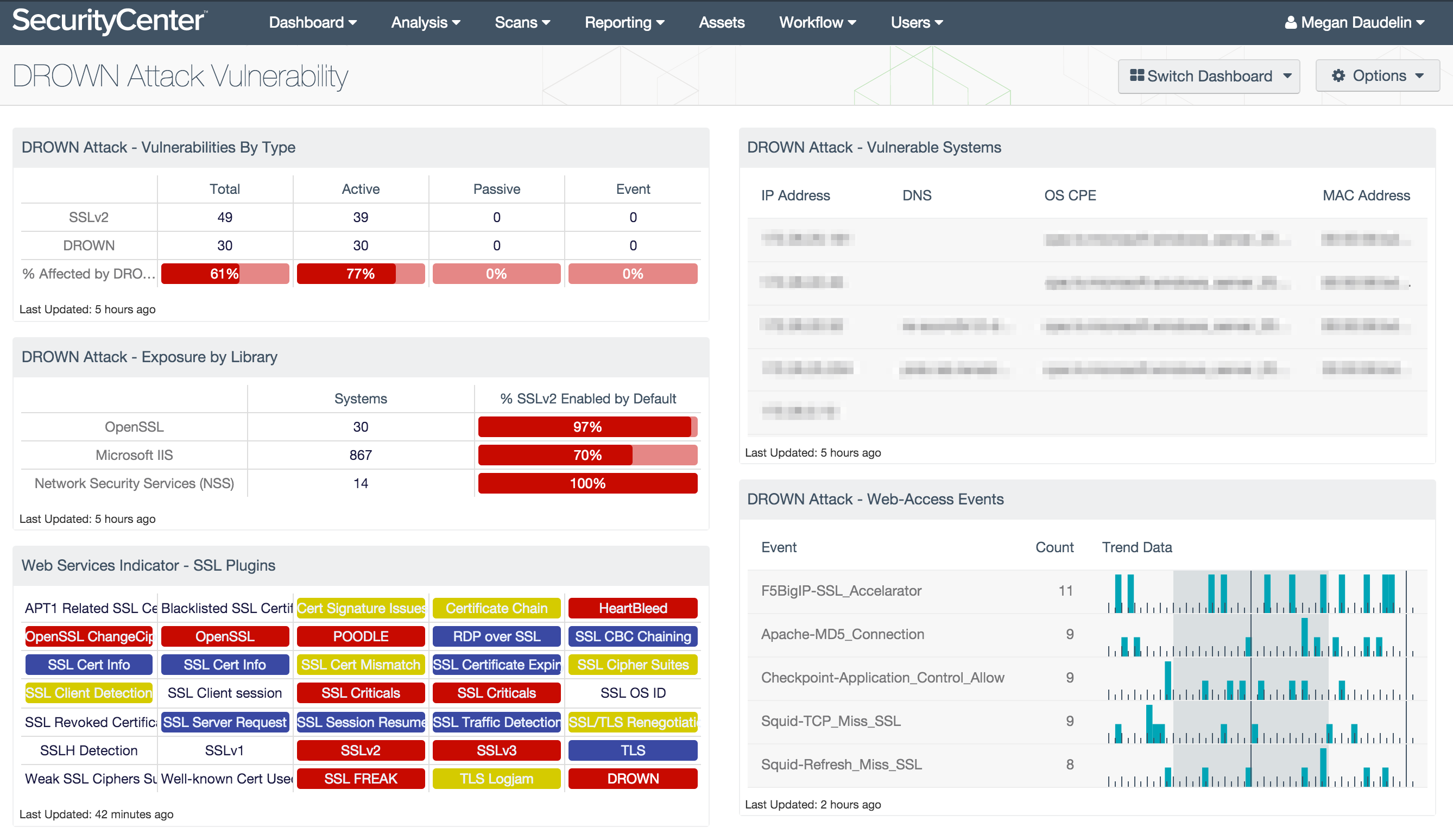
The DROWN Attack Vulnerability dashboard assists security teams with identifying systems on the network that are vulnerable to DROWN attacks. Data is filtered to identify systems with SSLv2 enabled using specific plugins, vulnerability text, and CVE IDs. Components monitor the presence of SSLv2 and web service libraries that have SSLv2 enabled by default. Additionally, filters for DROWN-specific plugins are used to provide information about hosts with confirmed DROWN vulnerabilities.
This dashboard and its components are available in the SecurityCenter Feed, a comprehensive collection of dashboards, reports, Assurance Report Cards, and assets. This dashboard can be easily located in the SecurityCenter Feed under the category Security Industry Trends. The dashboard requirements are:
- SecurityCenter 4.8.2
- Nessus 6.5.4
- LCE 4.6.0
- PVS 4.4.0
SecurityCenter Continuous View (CV) provides continuous network monitoring, vulnerability identification, risk reduction, and compliance monitoring. Nessus is continuously updated with information about advanced threats and zero-day vulnerabilities, and new types of regulatory compliance configuration audits. The Passive Vulnerability Scanner (PVS) performs deep packet inspection to enable discovery and assessment of operating systems, network devices, hypervisors, databases, tablets, phones, web servers, cloud applications, and critical infrastructure. The Log Correlation Engine (LCE) performs deep log analysis and correlation to continuously discover and track systems, applications, cloud infrastructure, trust relationships, and vulnerabilities. By integrating with Nessus, PVS, and LCE, SecurityCenter CV’s continuous network monitoring is able to detect events and vulnerabilities across the enterprise.
The following components are included in this dashboard:
- DROWN Attack - Vulnerabilities by Type: The Vulnerabilities by Type matrix displays the counts of SSLv2 and DROWN vulnerabilities detected by plugin type.
- DROWN Attack - Exposure by Library: The Exposure by Library matrix displays information about systems with specific web service libraries that can increase exposure to DROWN attacks.
- Web Services Indicator - SSL Plugins: All the plugins that refer to SSL or certificates have been grouped into these indicators.
- DROWN Attack - Vulnerable Systems: The Vulnerable Systems table presents a list of hosts that are vulnerable to a DROWN attack.
- DROWN Attack - Web-Access Events: The Web-Access Events table lists normalized events related to web access using SSL and TLS.