Bring Unknown Assets and Shadow IT into the Light
“Know yourself” is millennia-old advice, yet today’s IT environments almost always violate this principle. With the widespread popularity of mobile devices, cloud services, and virtualized infrastructures, it’s now incredibly easy for employees and others to introduce new devices or applications to the IT environment without the knowledge or consent of IT. Traditional security tools don’t provide visibility into these areas, so these unknown devices, applications, and services expose organizations to risk and probable attacks.
Bringing unknown and shadow assets into the light is a necessary part of a robust and effective security program
Today at the RSA Conference in San Francisco, Tenable announced how our technology helps organizations bring unknown assets and shadow IT into the light with our SecurityCenter Continuous View™ (CV) solution. In this article, I’ll describe some of its unique capabilities that enable complete visibility into your environment.
You need to see IT to secure IT
Peter Drucker famously said, “What gets measured, gets managed.” Similar thinking for IT security is that “You need to see it to secure it.”
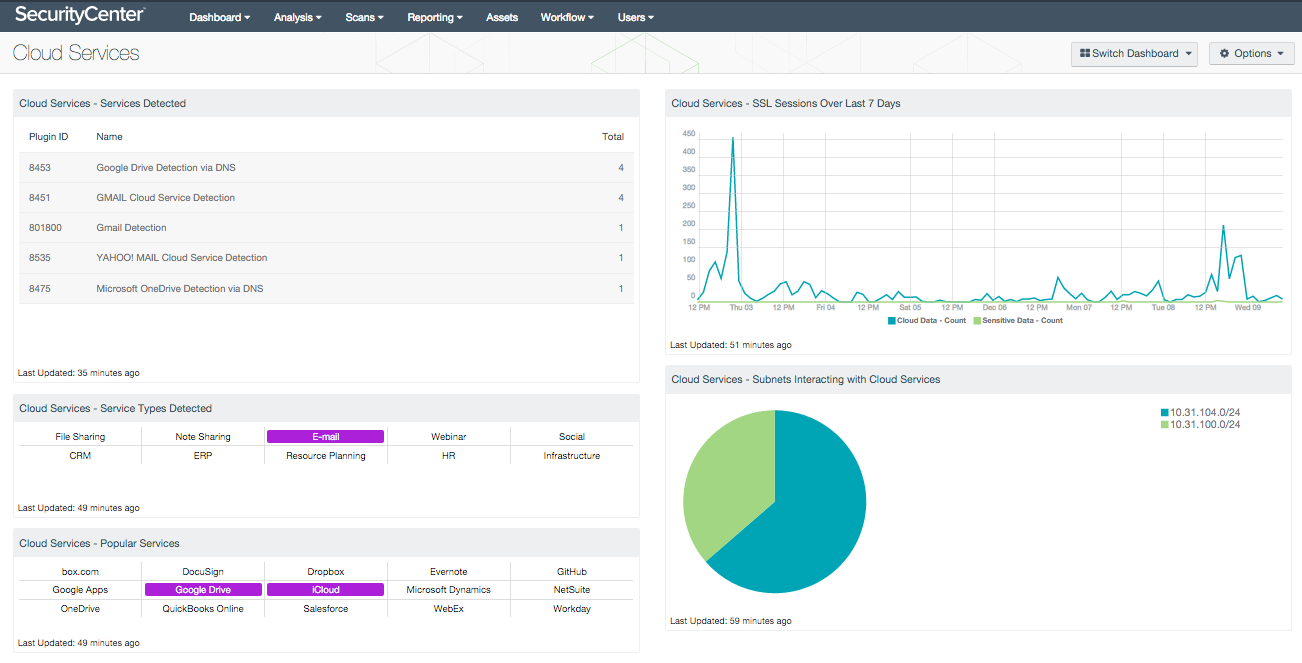
To enable you to see the unknowns, SecurityCenter CV collects and analyzes data from a variety of sensors—active scanning, passive listening of network activity and event data, and data feeds from intelligent connectors. For example in the dashboard below, SecurityCenter CV passively listens for network interactions with cloud services and reports back which services it detects and whether those services fit into known profiles that are allowed by the organization.
Get more information about the Cloud Services dashboard.
Gaining visibility into unknown and shadow assets is just the first step. To understand if these assets pose a threat to your environment, SecurityCenter CV profiles them to determine their risk and lets you know if they’re interacting with other known assets. For example, a DropBox account set up by an employee who wants to share materials with a partner might pose a different level of risk than a DropBox account that’s interacting with an internal SAP server.
Taking the right action
Once you know what’s really on your network and the associated risk, then it’s a matter of taking the right action … do you remove assets, investigate them more, simply make them part of your ongoing security programs, or something else? With limited time and resources, it’s about taking the right action. As Peter Drucker also said, “Efficiency is doing things right. Effectiveness is doing the right thing.” Here, SecurityCenter CV offers a number of pre-defined reports and dashboards to help you quickly make sense of all the collected data from unknown and shadow assets. These reports and dashboards drill down into detected vulnerabilities and present them in the context of your greater security program, so you can make informed decisions for effective and rapid response.
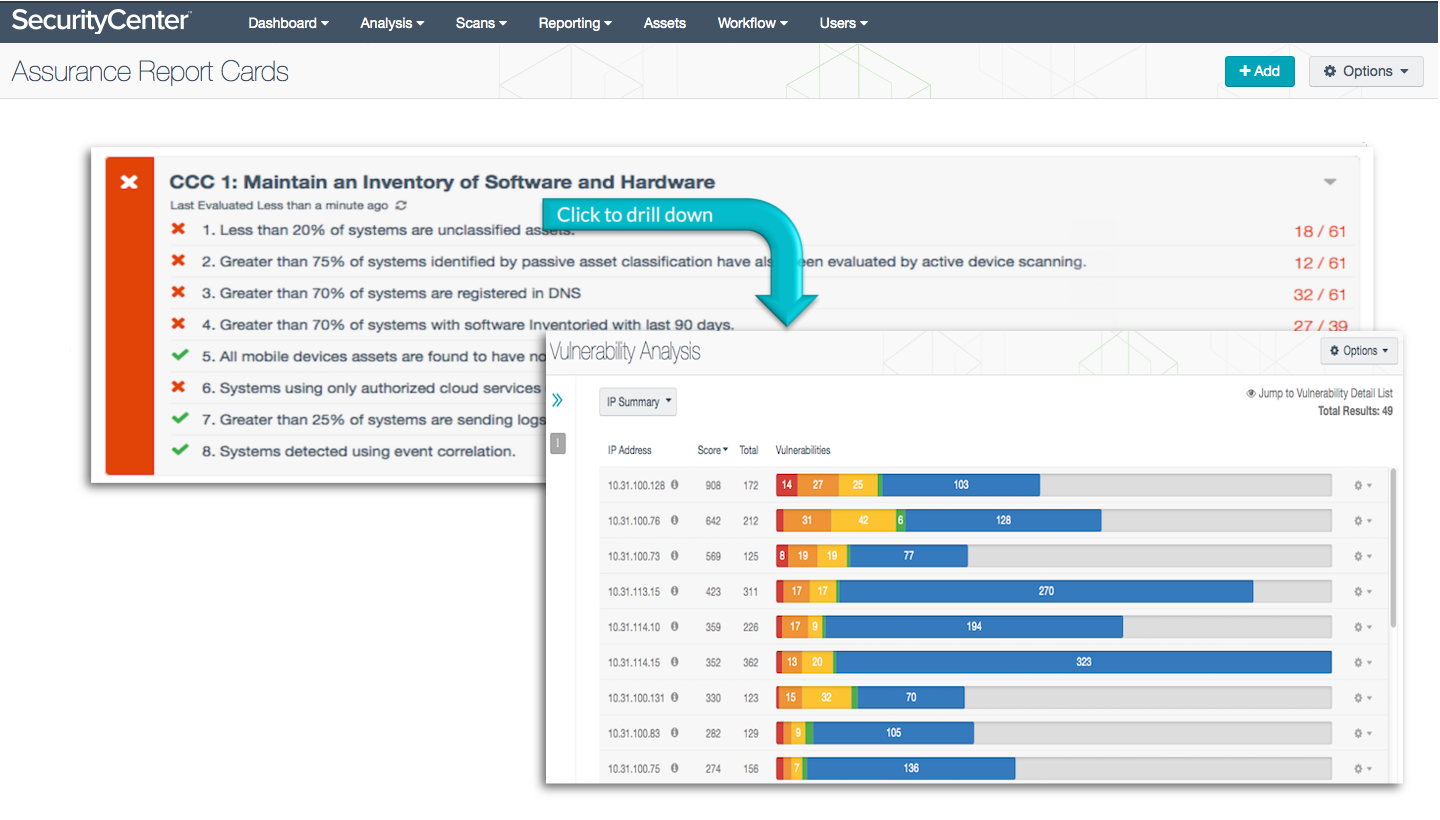
For example, one of the metrics displayed in the following Assurance Report Card (ARC) is the number of assets discovered by SecurityCenter CV that are unknown, or unclassified. The ARC displays your organization’s goal (“Less than 20%”) as well as other software and hardware inventory goals. Drilling down provides quick insight into the vulnerabilities associated with the unknown, or unclassified assets, enabling security professionals to quickly see what’s in their environment, what risk is posed and where they should take action.
Learn more about this Assurance Report Card.
Summary
With mobile, virtual and cloud all growing exponentially, stamping out unknown assets and shadow IT may never happen. But with SecurityCenter CV, bringing unknown and shadow assets into the light is not only possible, it’s a necessary part of a robust and effective security program.
For more information, visit our Unknown and Shadow Assets solution page.
- Announcements
- SecurityCenter
- Shadow IT