Tenable versus CrowdStrike Falcon Exposure Management
Proactively secure your attack surface — not just your endpoints
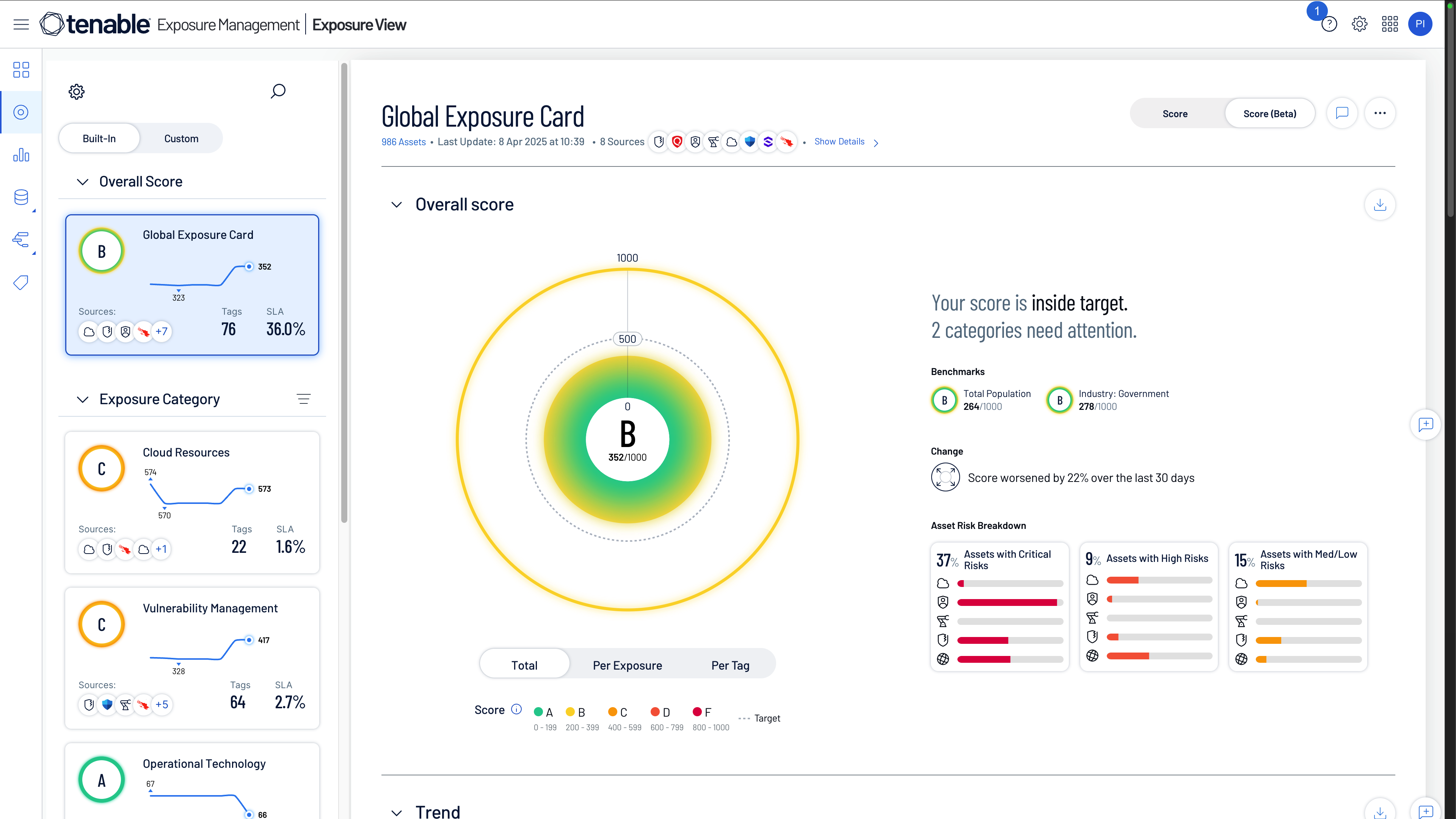
Tenable has defined proactive security with best-in-class vulnerability management for more than two decades. And now, we are leading the way to exposure management. While CrowdStrike specializes in reactive incident response with endpoint detection and response (EDR), we enable security leaders to identify, prioritize and mitigate cyber risks effectively before attackers can exploit them.
Tenable を動画でご視聴ください
事業を特に危険な攻撃リスクにさらしているさまざまなネット環境の弱点。Tenable がそれらをどのようにして可視化して解決できるように支援しているか、ご覧になりませんか。
カスタマイズした見積もりやデモをご希望の場合は、こちらのフォームにご記入ください。
Why customers choose Tenable over CrowdStrike
Compare Tenable Exposure Management
to CrowdStrike Falcon Exposure Management
Core focus
Unified exposure across IT, cloud, identity, and OT
Exposure from endpoint and identity telemetry
エクスポージャー管理
Combines integrated metrics across risk-based vulnerability management, web app scanning (WAS), cloud security, identity exposure, OT security, EASM and third-party data
Lacks comprehensive network scanning, web app security (WAS), identity data and holistic context beyond endpoints
資産インベントリ
Unified asset graph across IT, cloud, OT, and identities
Based on discovered external and managed endpoint assets
エクスポージャー対応
Exposure Response to track risk remediation with SLAs — instead of cumulative risk scores — and a single end-to-end workflow and a risk-based approach, regardless of patch availability
提供されていない
コンプライアンス
Covers a wide variety of compliance frameworks across various OSs
Limited support for CIS benchmarks
競合他社に対するベンチマーキング
Comparison of cyber risk to industry peers and to quickly identify shortcomings and strengths
提供されていない
Coverage scope
Coverage for a wide variety of asset types — endpoints, network devices, OT, cloud workloads, web apps
Primarily focused on endpoints with a Falcon agent and network devices visible to a Falcon agent
Scanning technology
Agent-based, agentless and network scanning
Agent-based and network scanning for devices visible to a Falcon agent
Tool consolidation potential
High—replaces scanners, CSPM, IAM risk tools, attack graphing, custom dashboards
Low—adds exposure context to Falcon but doesn’t replace core security tools
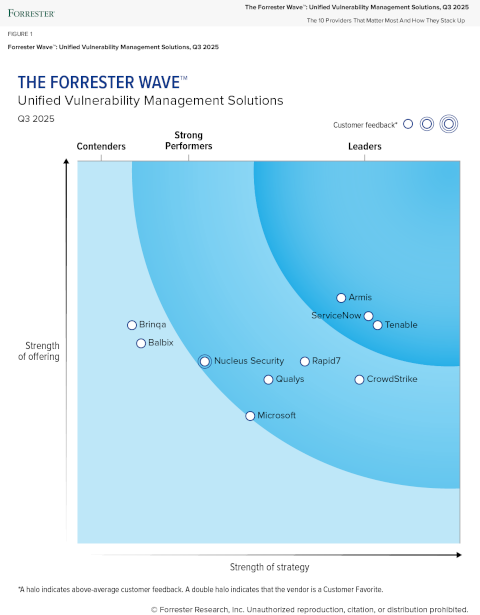
See why Tenable is a leader in vulnerability management
Tenable、Forrester の統合型脆弱性管理のレポート「Forrester Wave™: Unified Vulnerability Management, Q3 2025」でリーダー格に選出
Tenable continues to extend its established vulnerability assessment offerings into exposure management with its Tenable One platform
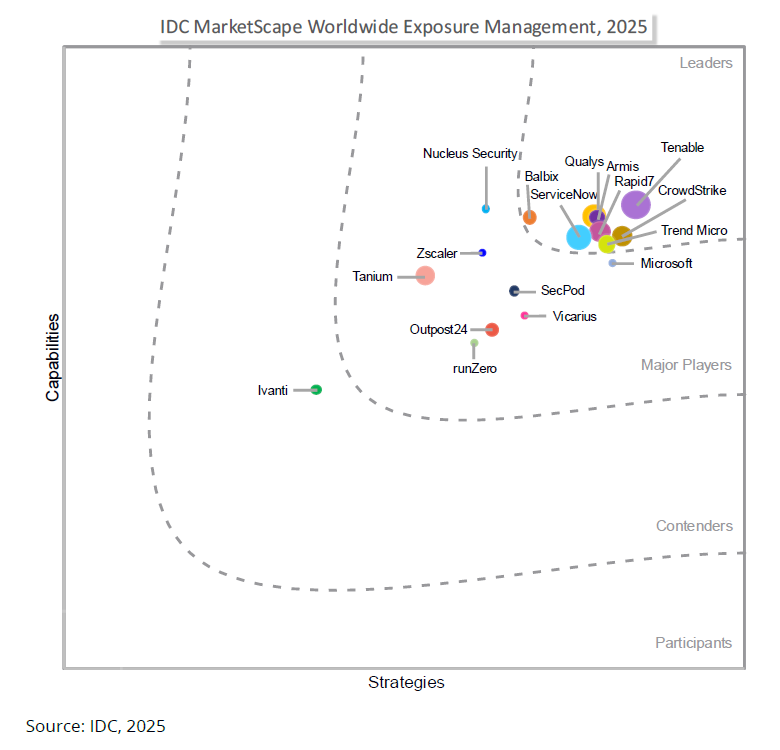
Tenable が IDC MarketScape Worldwide Exposure Management 2025 Vendor Assessment でリーダーグループに選出
IT、クラウド、OT/IoT、アイデンティティ、アプリケーション環境全体にわたる幅広い資産カバレッジを提供する統合型エクスポージャー管理プラットフォームを検討している組織は、Tenable One の導入を検討すべきです。
報告書を読むTenable One を始めましょう
Tenable One はエンジニアが手作業にかける時間を 75% 削減し、本当のエンジニアリングの作業に集中することを可能にしました