Cybersecurity Snapshot: Global Agencies Target Criminal “Bulletproof” Hosts, as CSA Unveils Agentic AI Risk Framework

Cyber agencies call on ISPs to help combat "bulletproof" internet hosts that shield cybercriminals. Meanwhile, the CSA introduced a new methodology to assess the risks of autonomous AI. Plus, get the latest on the CIS Benchmarks, drone-detection systems, and malware infections.
Key takeaways
- Crackdown on “bulletproof” hosting: International cyber agencies are urging ISPs and network defenders to help degrade internet infrastructure used by cybercriminals.
- New agentic AI risk framework: The Cloud Security Alliance introduced the Capabilities-Based Risk Assessment (CBRA) to help organizations quantify risks associated with autonomous AI systems.
- Fresh CIS Benchmarks: A new batch of configuration guides covers Windows Server 2025 and various Linux distros, alongside updates for software products from Google, IBM, Oracle and others.
Here are five things you need to know for the week ending November 21.
1 - Cyber agencies ask for help in defusing “bulletproof” internet hosts used by criminals
Multi-national cybersecurity agencies are asking ISPs and network defenders to help unmask and dismantle bulletproof hosting providers (BPH), which offer internet infrastructure services to cyber criminals.
“The authoring agencies have observed a marked increase in cybercriminal actors using BPH infrastructure to support cyber operations against critical infrastructure, financial institutions, and other high-value targets,” reads the joint advisory “Bulletproof Defense: Mitigating Risks From Bulletproof Hosting Providers.”
“BPH providers continue to pose a significant risk to the resilience and safety of critical systems and services,” adds the advisory from cyber agencies in Australia, Canada, the Netherlands, New Zealand, the U.K., and the U.S.
BPHs intentionally ignore legal processes, abuse complaints, and law enforcement takedown requests, shielding cybercriminals and helping them launch ransomware attacks, extort data, deliver malware, conduct phishing campaigns, and more.
They provide obfuscation through techniques like fast flux, effectively masking the identity and location of the perpetrators.

However, identifying criminal activity facilitated by BPHs isn’t easy because BPH infrastructure is woven into the infrastructure of legitimate ISPs.
“BPH providers lease their own infrastructure to cybercriminals. Increasingly, they resell stolen or leased infrastructure from legitimate hosting providers, data centers, ISPs, or cloud service providers who may unknowingly enable BPH providers to provide infrastructure to cybercriminals,” reads the document.
The advisory offers guidance for ISPs and network defenders to take “nuanced” steps to gum up BPHs’ services without impacting legitimate infrastructure.
Ultimately, the idea is to help degrade the effectiveness of BPHs’ infrastructure to the point where their cyber criminal customers are forced to leave their BPH safe havens and switch to legitimate service providers, which, unlike BPHs, do respond to abuse complaints and to law-enforcement requests.
Recommendations include:
- Conducting rigorous traffic analysis
- Curating and automating reviews of "high confidence" lists of malicious internet resources
- Establishing robust standards for ISP accountability
- Proactively creating filtering tools
- Maintaining transparent communication regarding malicious resource lists
“Bulletproof hosting is one of the core enablers of modern cybercrime,” Acting CISA Director Madhu Gottumukkala said in a statement. “By shining a light on these illicit infrastructures and giving defenders concrete actions, we are making it harder for criminals to hide and easier for our partners to protect the systems Americans rely on every day.”
In a related development, Australia, the U.K. and the U.S. jointly sanctioned Russia-based BPH company Media Land and its network, the U.S. Treasury Department said in a statement. Meanwhile the U.K. and U.S. governments also sanctioned Hypercore Ltd., a front company for BPH company Aeza Group, along with several individuals, it added.
For more information about BPH:
- “Bulletproof hosting providers: Cracks in the armour of cybercriminal infrastructure” (Australian Cyber Security Centre)
- “Bulletproof hosting provider Proton66 steps-up malware campaigns” (SC World)
- “Why Bulletproof Hosting is Key to Cybercrime-as-a-Service” (Infosecurity Magazine)
- “US sanctions ‘bulletproof’ hosting provider Aeza for cybercrime ops” (SC World)
- “Key to Qilin's Ransomware Success: Bulletproof Hosting” (Bank Info Security)
2 - CSA unveils agentic AI risk assessment tool
To assess the risks of using agentic AI, conventional risk models may fall short. So how can you determine the risks your organization faces from these autonomous AI tools?
You might want to check out a new risk-assessment framework for agentic AI systems from the Cloud Security Alliance (CSA).
The framework, called Capabilities-Based Risk Assessment (CBRA) is detailed in a new CSA white paper and evaluates agentic AI systems across four areas:
- System criticality
- AI autonomy
- Access permissions
- Impact radius
These factors are combined to generate a composite risk score, allowing enterprises to quantify the potential consequences of system failure or misuse.

“AI autonomy and access are expanding faster than traditional risk management models can adapt,” Pete Chronis, Co-Chair of the CSA AI Safety Initiative CISO Council, said in a statement.
“CBRA allows enterprises to align their governance investments with actual risk exposure – protecting high-impact agentic systems while accelerating safe innovation elsewhere,” he added.
The CBRA is integrated with the CSA’s AI Controls Matrix (AICM). CBRA maps its three-tier risk levels — low, medium, and high — to the AICM’s library of over 240 AI-specific controls, so that security measures taken are proportionate to the risk.
For more information about AI security, check out these Tenable Research blogs:
- “Frequently Asked Questions About DeepSeek Large Language Model (LLM)”
- “Frequently Asked Questions About Model Context Protocol (MCP) and Integrating with AI for Agentic Applications”
- “Frequently Asked Questions About Vibe Coding”
- “AI Security: Web Flaws Resurface in Rush to Use MCP Servers”
- “CVE-2025-54135, CVE-2025-54136: Frequently Asked Questions About Vulnerabilities in Cursor IDE (CurXecute and MCPoison)”
3 - CIS releases batch of new and updated Benchmarks
Time to tighten the screws on the software configurations of products from Oracle, Microsoft, Google, IBM, Apple, and more. The Center for Internet Security (CIS) just refreshed a variety of its existing Benchmarks and introduced multiple new ones.
The following CIS Benchmarks were updated:
- CIS Palo Alto Firewall 11 Benchmark v1.2.0, which includes enhanced automated compliance and audit readiness
- CIS Oracle MySQL 8.0 Enterprise Benchmark v1.5.0, which includes improved account security by enforcing password policies for all accounts
- CIS Oracle MySQL 8.0 Community Server Benchmark v1.2.0, which includes backporting password enforcement recommendations
- CIS Microsoft Azure Foundations Benchmark v5.0.0, which adds 22 new recommendations and updates 58 others to better align with cloud security practices
- CIS Google Android Benchmark v1.6.0, which includes better alignment with iOS benchmarks for consistent mobile security
- CIS Microsoft Edge Benchmark v4.0.0, which includes refined browser hardening with new ADMX-based security settings
- CIS IBM Db2 11 Benchmark v1.2.0, which includes improved clarity and remediation steps
CIS also launched seven entirely new Benchmarks. The CIS Microsoft Windows Server 2025 Stand-alone Benchmark v1.0.0 provides foundational security guidance for the latest Windows server environment. Linux coverage was expanded with new Benchmarks for Red Hat Enterprise Linux 10, Rocky Linux 10 and AlmaLinux OS 10. Additionally, new guides were released for IBM z/OS with RACF, FortiGate 7.4.x, and Apple iOS/iPadOS 18 for Intune, the latter specifically tailored for device management via Microsoft Intune.
Meanwhile, there are new Build Kits for various Oracle, Microsoft and Red Hat products. Build Kits automate the CIS Benchmarks’ configuration process.
- CIS Rocky Linux 10 Benchmark v1.0.0
- CIS Microsoft Windows Server 2025 Stand-alone Benchmark v1.0.0
- CIS Oracle Linux OS 10 Benchmark v1.0.0
- CIS AlmaLinux OS 10 Benchmark v1.0.0
- CIS Microsoft Edge Benchmark v4.0.0
- CIS Red Hat Enterprise Linux 10 Benchmark v1.0.1

Currently, CIS has 100-plus Benchmarks to harden the configurations of cloud platforms; databases; desktop and server software; mobile devices; operating systems; and more.
To get more details, read the CIS blog “CIS Benchmarks Monthly Update November 2025.” For more information about the CIS Benchmarks list, check out its home page and FAQ, as well as:
- “Getting to Know the CIS Benchmarks” (CIS)
- “Security Via Consensus: Developing the CIS Benchmarks” (Dark Reading)
- “How to Unlock the Security Benefits of the CIS Benchmarks” (Tenable)
- “CIS Benchmarks Communities: Where configurations meet consensus” (Help Net Security)
- “CIS Benchmarks: DevOps Guide to Hardening the Cloud” (DevOps)
4 - CISA: Drone-detection tools have their own cyber risks
As critical infrastructure organizations rush to buy drone-detection systems to protect themselves from malicious drones, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) is raising a red flag: the detection tools themselves can be vulnerable.
In a guide published this week to help critical infrastructure organizations choose these tools, CISA warned that an important aspect of the selection process is the cybersecurity posture of these unmanned aircraft systems (UAS), as drones are formally known.
“Cybersecurity vulnerabilities can compromise the confidentiality, integrity, and availability of UAS detection information,” reads the guide “Unmanned Aircraft System Detection Technology Guidance.”

Examples of cybersecurity flaws in these UAS-detection products include:
- Insecure collection and transfer of data
- Malicious executables hidden within required software and firmware updates
- Vulnerable connected devices utilized by detection systems
CISA recommends that critical infrastructure organizations ask UAS-detection vendors questions including:
- Can your product’s operating system be physically accessed or tampered with?
- Can you provide both a software bill of materials (SBOM) and hardware bill of materials (HBOM) for your product?
- How long will you provide security and firmware updates for your product?
- What data does your product’s sensor collect and store?
- Who will have access to the data collected by your product?
“The new risks and challenges from UAS activity demonstrate that the threat environment is always changing, which means our defenses must improve as well,” CISA Acting Director Madhu Gottumukkala said in a statement.
The 12-page guide also addresses non-cyber criteria for choosing a drone-detection system.
CISA published two other drone-security guides in July for critical infrastructure organizations: “Suspicious Unmanned Aircraft System Activity Guidance for Critical Infrastructure Owners and Operators” and “Safe Handling Considerations for Downed Unmanned Aircraft Systems.”
5 - Malware infections jump almost 40% in Q3
Malware infection reports spiked 38% from the second to the third quarter of 2025, according to data from CIS’ Multi-State Information Sharing and Analysis Center (MS-ISAC) monitoring services.
SocGholish, which attackers use in fake software-update attacks, once again ranked as the most prevalent malware variant, a spot it has held for the past two years.
SocGholish’s prevalence reflects the popularity of fake software-update attacks among hackers. These attacks attempt to trick unsuspecting users into downloading a software update that appears legit. Of course, the “update” infects victims’ devices with malware.
Following SocGholish is CoinMiner, a cryptocurrency miner that spreads via Windows Management Instrumentation (WMI), and Agent Tesla, a remote access trojan (RAT) known for harvesting credentials and capturing keystrokes.
Notably, Q3 2025 saw the return of the Gh0st, Lumma Stealer, and TeleGrab variants, and the debut of Jinupd.
According to CIS, Lumma Stealer’s reappearance is significant as it follows a previous law enforcement takedown of its "malware as a service" (MaaS) infrastructure for targeting banking data and personal information.
Jinupd, the newcomer, is a point-of-sale (POS) infostealer that scrapes credit card data from memory, often disguising itself as a Java updater.
The report tracks three primary infection vectors: Dropped (delivered by other malware), Malspam (malicious emails), and Malvertisement (malicious ads). However, "Multiple" was the leading infection vector category for this quarter.
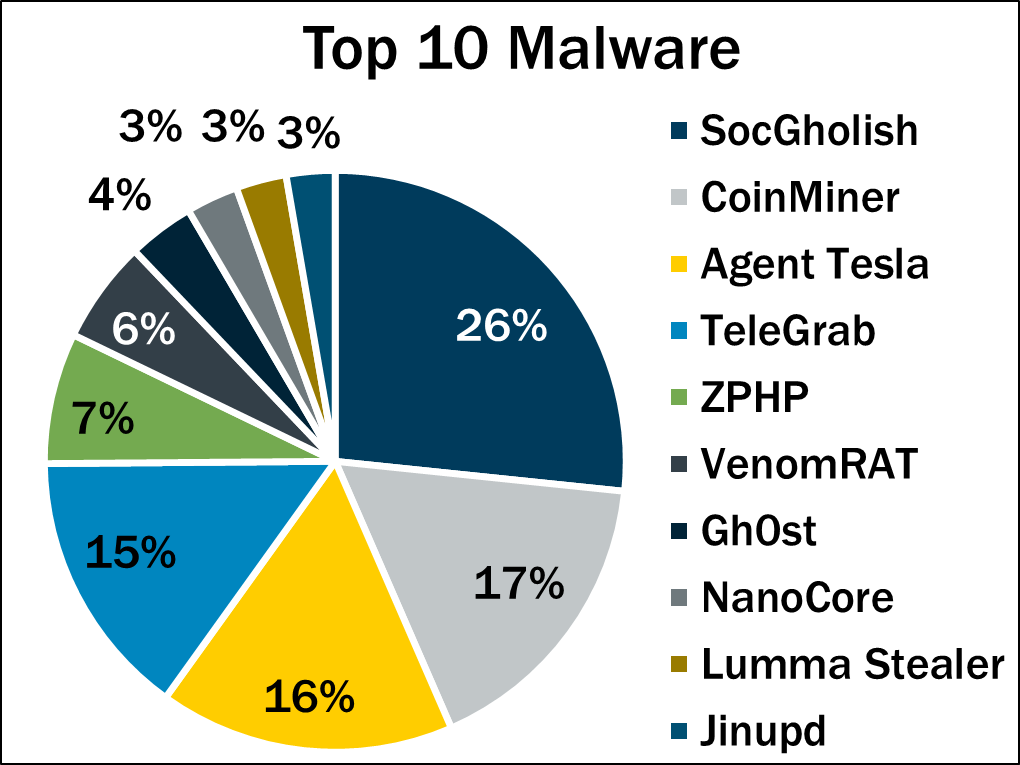
Here’s Q3’s malware hit parade:
- SocGholish, a downloader distributed through malicious websites that tricks users into downloading it by offering fake software updates
- CoinMiner, a cryptocurrency miner that spreads using Windows Management Instrumentation (WMI)
- Agent Tesla, a RAT that captures credentials, keystrokes and screenshots
- TeleGrab, an infostealer that targets Telegram, swiping cache and key files, hijacking chat sessions, and stealing contacts and chat history
- ZPHP, a RAT that captures credentials, keystrokes and screenshots
- VenomRAT, an open-source malware whose features include keylogging, data exfiltration and screen capturing
- Gh0st, a RAT designed to control infected endpoint devices
- NanoCore, a RAT that spreads via malspam as a malicious Excel spreadsheet
- Lumma Stealer, an infostealer used to swipe personal information, credentials, cookies and banking information
- Jinupd, a point-of-sales infostealer that steals credit card information by scraping memory from payment-processing applications
To get more information, check out the CIS blog “Top 10 Malware Q3 2025,” where you’ll find more details, context and indicators of compromise for each malware strain.
For details on fake software-update attacks:
- “The Fake Browser Update Scam Gets a Makeover” (Krebs on Security)
- “Watch Out: Attackers Are Hiding Malware in 'Browser Updates'” (Dark Reading)
- “Hackers Use Fake Browser Updates for AMOS Malware Attacks Targeting Mac Users” (MSSP Alert)
- “Malware crooks find an in with fake browser updates, in case real ones weren't bad enough” (The Register)
- “Hackers have been spreading malware via fake Chrome updates” (TechRadar)
- Cloud
- Cybersecurity Snapshot



