Linux/UNIX Patch Auditing Using Nessus
Comprehensive Linux and UNIX Patch Knowledge
Ensuring that your Linux and UNIX systems are up-to-date with the latest patches is no small task. Largely due to ever evolving Linux distributions and virtual machine (VM) sprawl, you likely have a much larger Linux footprint than ever before. Systems administrators must keep tabs on the plethora of patches being released for each platform. Unlike Microsoft Windows systems, which have a regular patch cycle, Linux and UNIX variants, for the most part, release patches for software as they become available.
Thankfully, Nessus is here to help. More than 1,000 plugins have been released this year that check for local Linux and UNIX operating system's missing patches. This includes kernel patches and security updates to software packages being maintained by each distribution.
Nessus can help you:
- Prioritize patching by using credentialed scanning and result filtering to identify the most critical patches.
- Overcome false positives caused by back-ported security fixes.
- Find vulnerabilities hidden by network and host-based firewalls.
- Find and prioritize remotely-exploitable vulnerabilities.
Detect Missing Local Patches
Finding the missing patches on your Linux/UNIX systems is easy once you provide credentials to the Nessus server. In a lab environment, you can provide a root-level account and password to allow Nessus to log in. In production, I highly recommend the following configuration which uses sudo for privilege elevation:
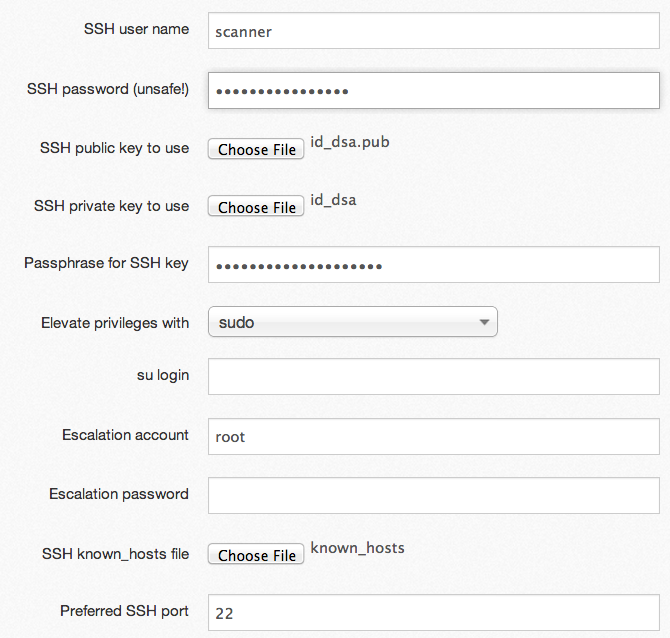
- Generate a private/public key pair for your Nessus server and assign a passphrase.
- Add an account to your targets (for example, called "scanner") with normal user privileges, and assign a password.
- Allow the Nessus server to log into all of your targets using the private/public key.
- Configure the scanner account to use "sudo" to escalate to root privileges.
- Upload the private/public key of the scanner account to your Nessus server, and provide the passphrase.
- Configure Nessus to use "sudo" to become root.
- Upload a list of known hosts to Nessus which defines the systems Nessus will attempt to log into.
Auditing Linux Security Updates
When provided with credentials as shown above, Nessus will report on all of the missing security patches for each target. If the target hosts haven’t had updates applied in some time, the resulting report can be quite lengthy. For example, I performed a credentialed patch audit against an older Ubuntu distribution:
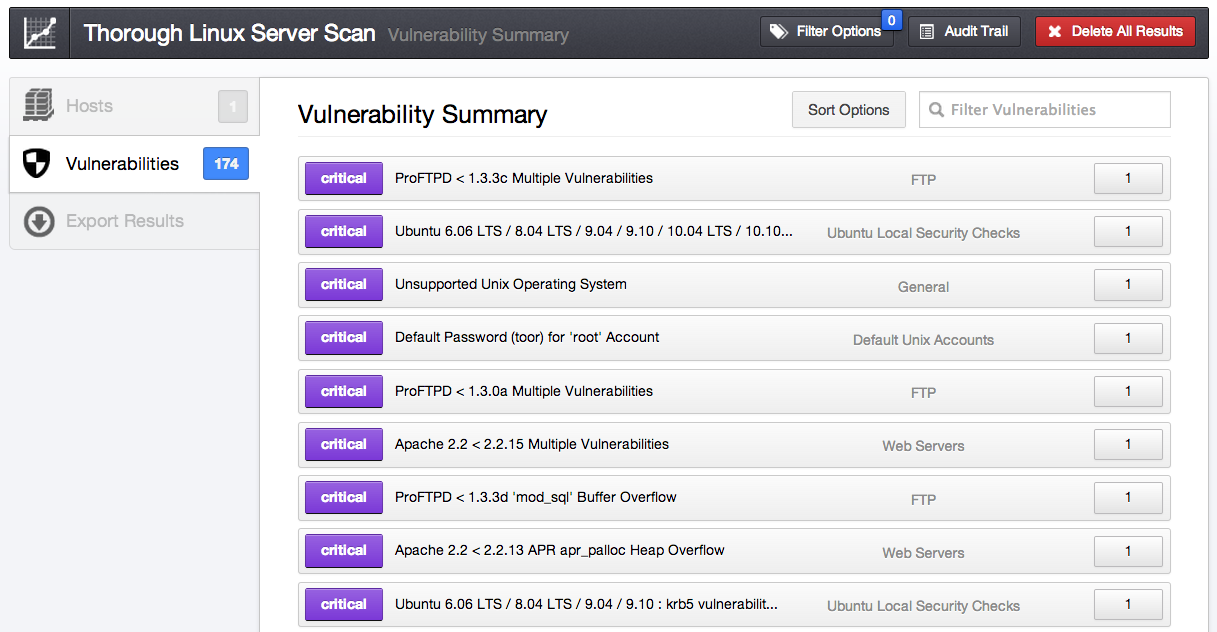
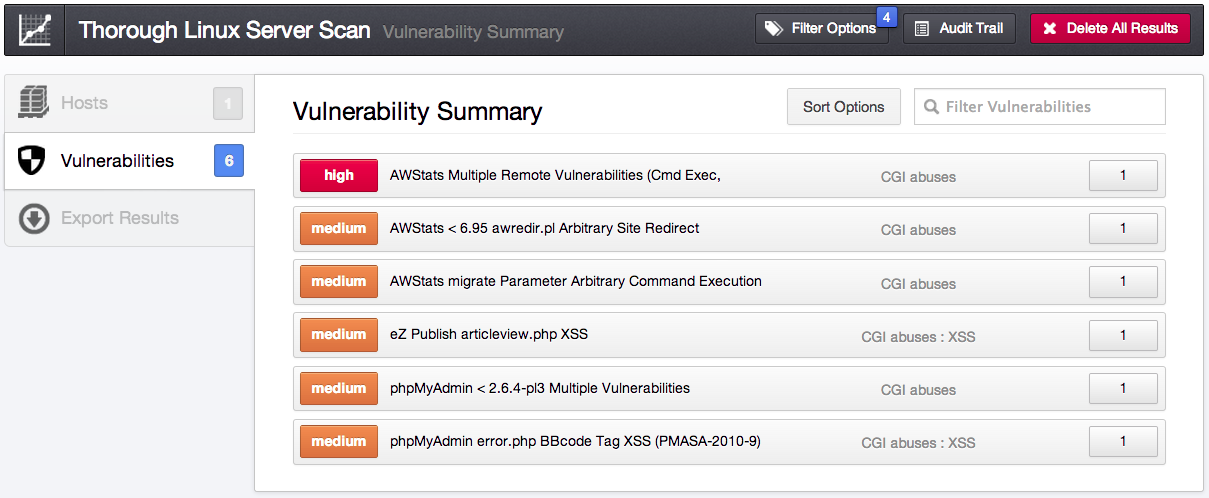
Although I was only scanning one target, Nessus discovered 174 vulnerabilities. Prioritizing such a large number of vulnerabilities can be tricky. On the flip side, a complete package update will install several of the new updates. However, this doesn’t take into account packages installed from source code. To retrieve only the list of missing packages maintained by the distribution, you can apply a simple filter to search for plugins of type Local, and the resulting vulnerabilities drop to 77.
But, just how bad a shape are you really in? To pare the 77 number down even further, you can add a filter for exploitability. After applying the filter, the number of locally-exploitable vulnerabilities is down to a more manageable 36!
Dealing with Backported Software Patches
Often, a Linux distribution will not upgrade their packages to the latest and greatest versions of software. Instead, they’ll keep the existing software version and only apply the security patch, keeping the version number the same. In this instance, the software no longer contains a vulnerability, but the version being displayed by the banner will trace back to being vulnerable. When this occurs, Nessus will report potentially backported software versions as follows:
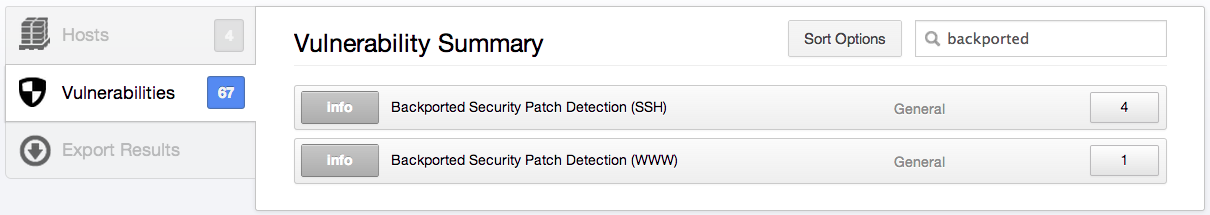
When you see the alerts above, it's an indication that using credentials is a much better way to scan. Once credentials are supplied, you may still see the backported software, but the following message will display:
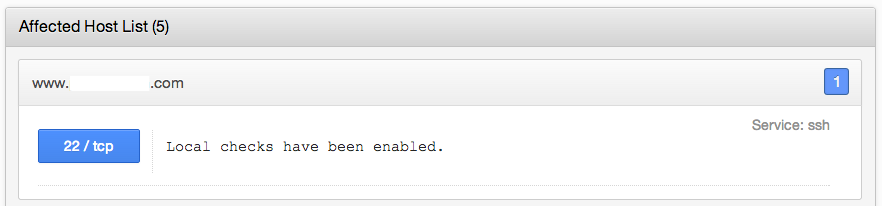
Bad Daemons, Bad Daemons
Sometimes, administrators are forced to install packages from source code; either they are not happy with the distributions configuration, or the distribution is not offering the latest version. Nessus contains a plugin to easily identify running processes that are not associated with a distributions package:
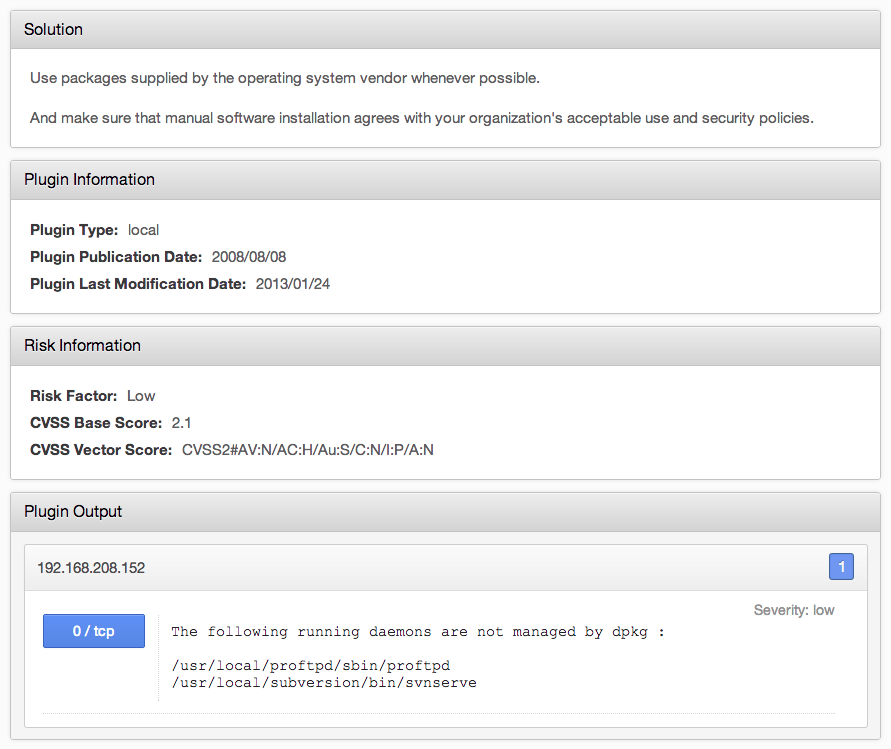
Next, let’s use a filter to look for remote vulnerabilities and see if you can identify vulnerabilities associated with ProFTPD that were found remotely without credentials:
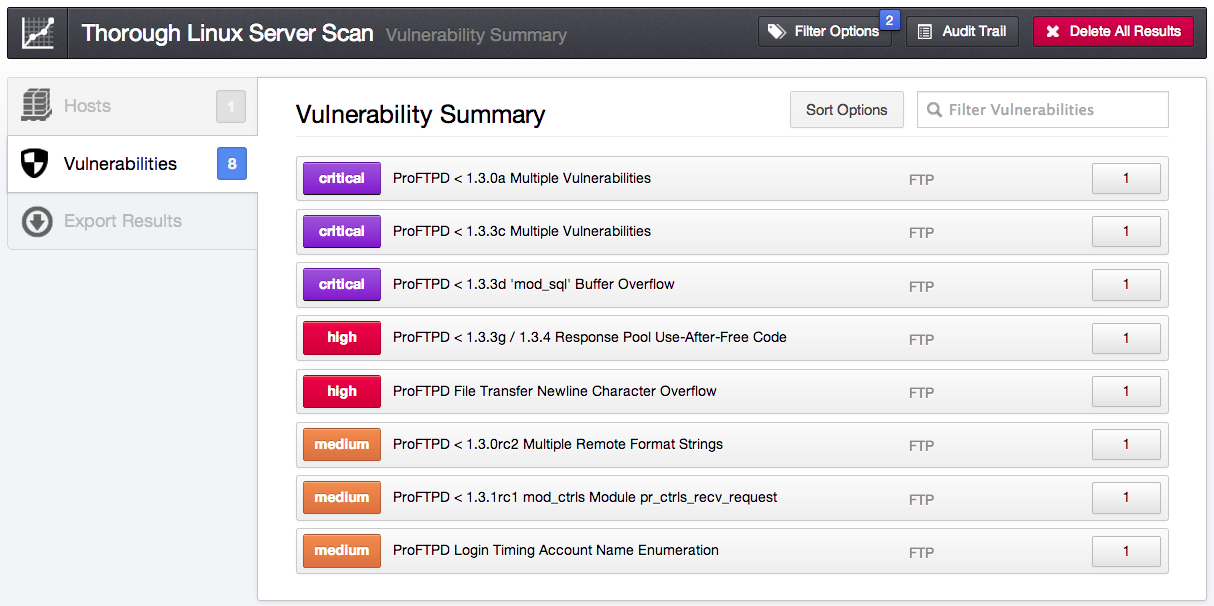
To get the results above, I set a plugin-type filter to "remote" and the plugin name filter to contain "proftpd".
Identify Exploitable Vulnerabilities
Another great way to prioritize patching is to use the exploitability index. If you've mastered credentialed scanning, you may want to focus on finding remotely-exploitable vulnerabilities. For example, the result filter can be used in the following ways:
Easily-exploitable remote vulnerabilities released before 2010:
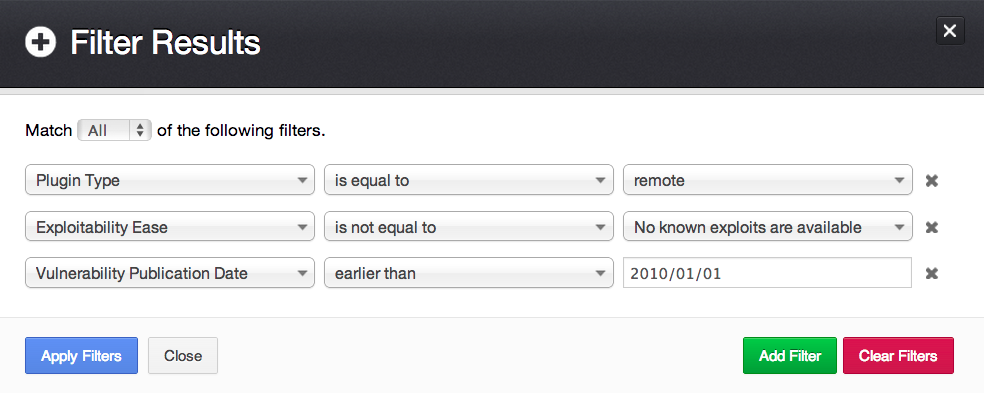
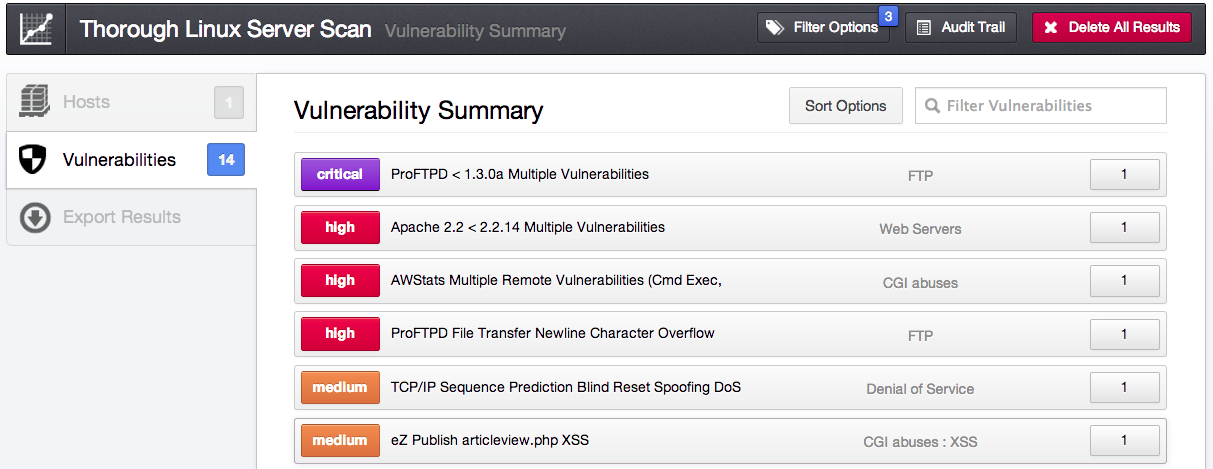
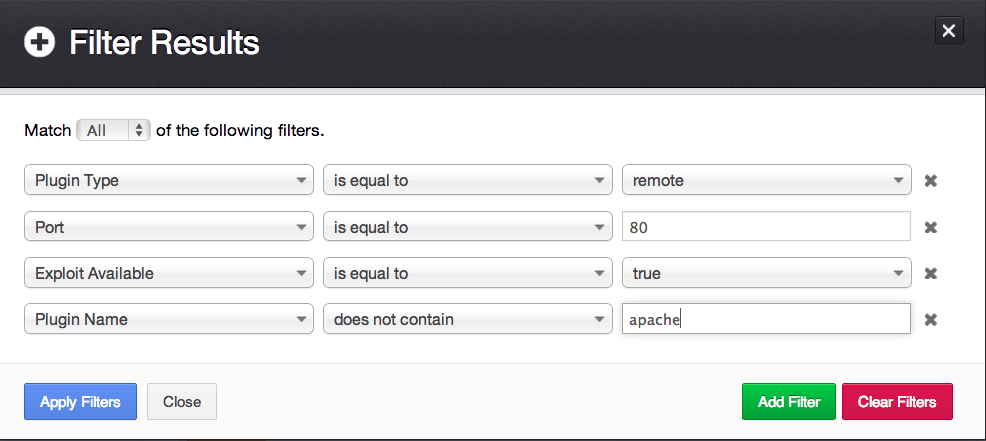
Remotely-exploitable web application vulnerabilities:
Conclusion
Nessus provides a comprehensive view of your Linux and UNIX patch status. It allows you to dig deeply into your systems to identify remote vulnerabilities, find missing local patches, and pare down your results to prioritize patching.
The Passive Vulnerability Scanner (PVS) can also be used to sniff the network for potential vulnerabilities, providing an even deeper look into what’s lurking on your network.
Finally, for enterprise vulnerability management, you can use SecurityCenter, which allows you to spread scans across multiple Nessus servers while managing credentials from one central location. SecurityCenter also provides a robust platform for allowing users to run their own scans, report, alert, and track vulnerabilities. Below is a list of SecurityCenter dashboards that allow you to easily visualize missing patches in conjunction with compliance audits:
- Nessus
- Patch Auditing

