Managing Cloud Compliance and Security Posture with Cloud Compliance Tools

Why compliance and access security in the public cloud are so challenging – and how carefully-chosen CSPM tools can help.
Security and compliance practitioners in organizations running workloads in the public cloud face many challenges in managing compliance. Advanced cloud security posture management (CSPM) tools can help provide visibility, monitoring and auditing capabilities based on policies, all in an automated manner. In this post, we’ll look at compliance- and access-security challenges in the cloud and explain how to find the optimal CSPM tool for your use.
The challenges of compliance in the cloud
The cloud has made applications and data more accessible for users and customers, but it has made work more complex for the professionals doing the heavy lifting. The cloud has posed new challenges to DevOps teams developing and maintaining cloud environments; developers pushing code to production without visibility; and security people protecting a distributed architecture with thousands of assets and digital identities.
This is also the case for compliance officers. Being responsible for compliance requires great attention to detail, a focus on process and a good understanding of the regulations and recommended guidelines.
Because cloud environments are very complex, meeting these compliance requirements has become harder. Cloud environments contain thousands of components and services that are globally dispersed and interconnected in diverse ways. The architecture is seldom entirely visible and is ever-changing, making it even more laborious to identify compliance issues like misconfigurations or poor access management.
In addition, to identify and alert about regulatory issues, you need an understanding of how these convoluted cloud technologies were developed and how they perform. Few have this skill set today, making it hard for compliance officers to get the training, assistance and support they need when running audits, or reviewing processes and procedures.
The main challenge of compliance officers may in fact lie with the regulating bodies. Many compliance standards were initially designed for on-premises environments. Explaining the differences between cloud and on-premises to regulators is not easy due to the complexity of cloud infrastructure and lack of technological know-how by some compliance officers. Above all, the industry lacks sufficient tools that can demonstrate how a cloud organization is being compliant. Which brings us to the next point.
The on-premises compliance ecosystem is brimming with professionals, platforms, consultation services and online resources designed to help businesses and compliance officers. But for the cloud, the number and scope of resources are not so abundant. CSPM (cloud security posture management) and other solutions, such as compliance for Kubernetes environments, are being developed to address this gap, but their market penetration is far and few. This is expected to change since the cloud is still fairly new. But regulators and auditors won’t wait until then, and compliance officers and professionals need to find another way to get help today.
Finally, in the cloud, credentials are the number one attack vector. When searching for regulation breaches and demonstrating compliance, compliance professionals must address the issue of identity and access management (IAM) security. But securing access and permissions, let alone reporting on it for audits, is not easy – and highlights the importance of navigating cloud security posture with deep discovery of identities and access. If you sidestep understanding risk based on identity and access, you’ll get a false view of your cloud security posture and true compliance status.
It wasn’t that easy before the cloud
Let’s be honest: being compliant even before the cloud was not easy. Compliance regulations are not a step-by-step plan. Rather, they describe an ideal end-state, and it’s up to the business and the auditors to figure out how to demonstrate compliance.
In addition, compliance officers are often left out of strategic discussions on business decisions that affect compliance. As a result, they are left to execute with little influence.
These challenges do not disappear with cloud architecture. If anything, they are intensified due to the complexities described above.
Finding solutions for compliance
The burden of compliance falls on the shoulders of compliance officers and stakeholders. What can they do?
Tip #1: Get guidance and help from external consultants
1+1=3. Get assistance from experts who have experience in building practical steps for demonstrating cloud compliance. Start at the drawing board, identifying what needs to be audited, proceed to how and then end with the actual audit and analysis of results.
Tip #2: Get the organization on board
You may be in charge of compliance but being compliant is in the organization’s best interests. Legal and monetary ramifications could affect IPOs, M&As and the bottom line. Evangelize internally with leadership, security and engineering. Train them in compliance requirements so they can help you identify potential regulatory pitfalls and how to close the gap.
Tip #3: Find technological cloud compliance tools that can help
We used to rage against the machine. Now we need machines to take away the tasks we hate so we’re free for more quality work. So, what is CSPM? A CSPM tool uses automation and templates to identify how the cloud environment is implementing policies that correlate with compliance regulations. Some tools can also auto-remediate in case of deviations and help the organization immediately improve its compliance posture. The bottom line: a good CSPM tool can make compliance easier.
CSPM and beyond: How to find the right tool
A high quality CSPM tool can relieve a lot of the compliance-related work from you while hardening the organization’s compliance with all relevant industry regulations. An ideal solution will encompass the following capabilities:
- Broad and relevant regulation scope: Covers a broad range of security best practices and leading industry and compliance standards. These include GDPR, HIPAA, ISO, NIST, PCI, SOC 2, CIS for Kubernetes and others. Make sure the regulations you need are included in the platform’s provided templates and policies.
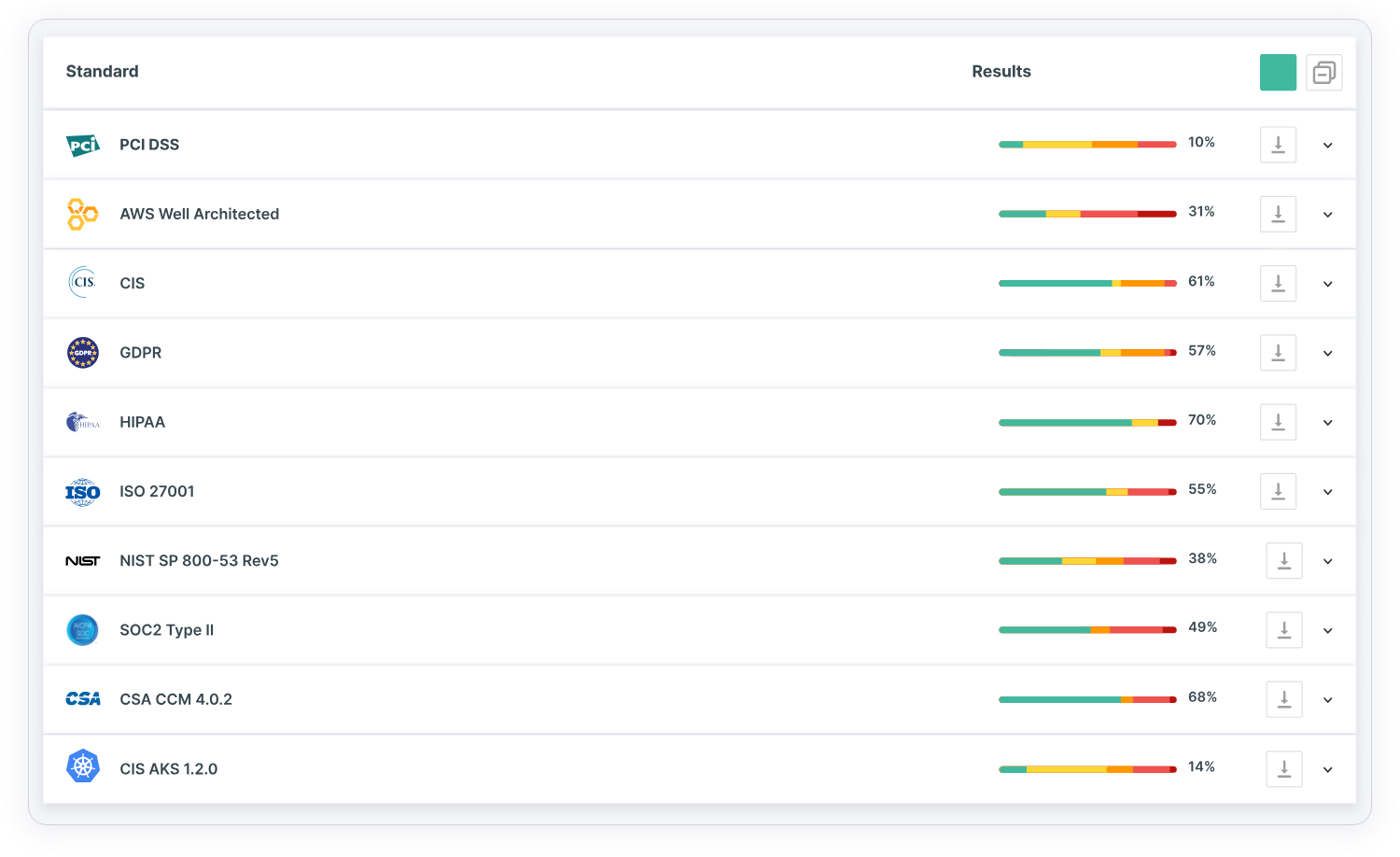
Carry out continuous compliance audit for regulatory standards and security best practices
- Compliance-cloud correlation: Maps each standard to specific cloud configuration, cloud security and cloud activity policies while providing a clear inventory of compliance status per asset/account. For example, a publicly exposed Lambda service might be breaching NIST Cybersecurity Framework (CSF), ISO 27001 and/or other compliance regulations and guidelines.
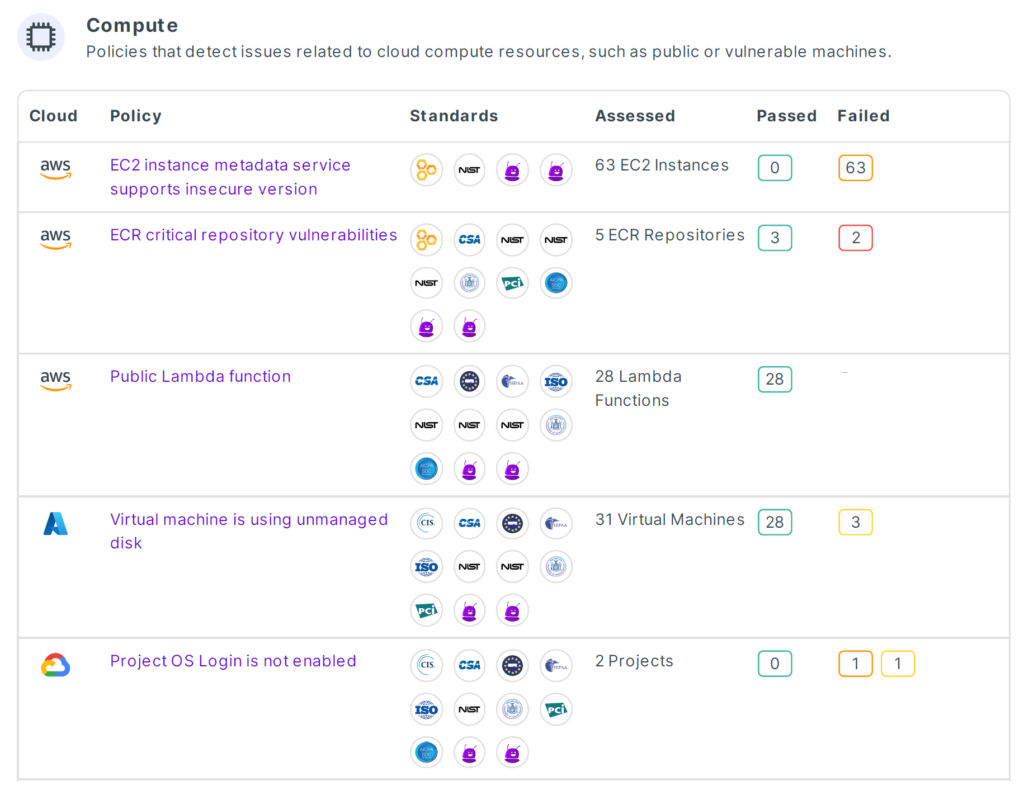
Compliance report: which services relate to which regulations and their status - Continuous Monitoring: Constantly checks the entire environment against the policies to ensure compliance and identify deviations and anomalies. The status of compliance should be visible to you and any stakeholder at any given point and without waiting for strenuous compliance audits.
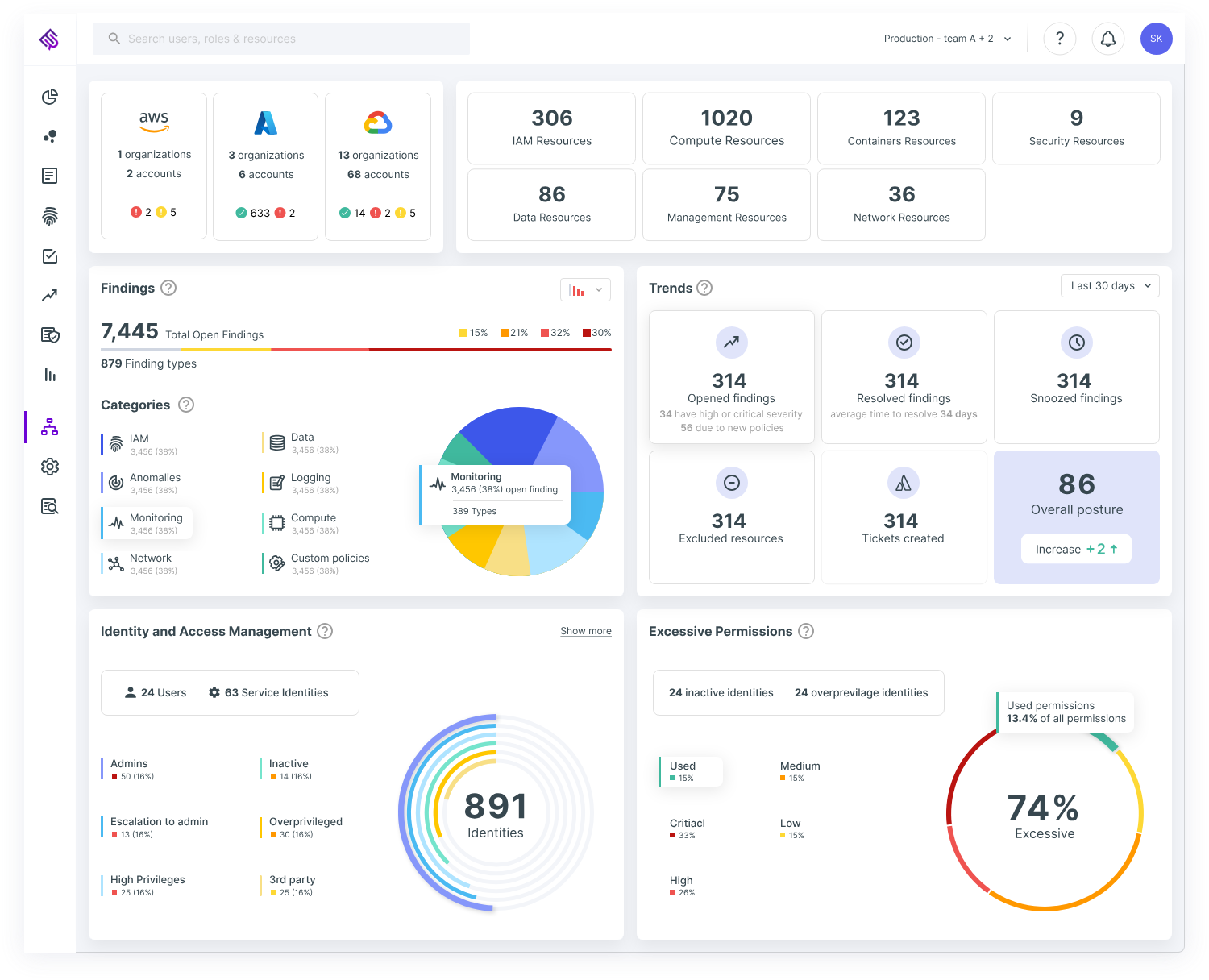
Manage cloud security posture and other cloud security needs in one multicloud platform
- Customization: Lets you create proprietary standards and policies on top of government regulations.
- Audit Reports: Helps you demonstrate compliance to auditors through visibility and flexible reporting for all organizational levels (e.g., entire organizations, specific accounts, specific projects), allowing to generate compliance reports for internal and external auditors. Ideally, your CSPM solution is one that auditors know and trust.
- Automation: Monitors, identifies, alerts and auto-remediates misconfigurations. Compliance teams are often strapped for resources and automation can help them focus.
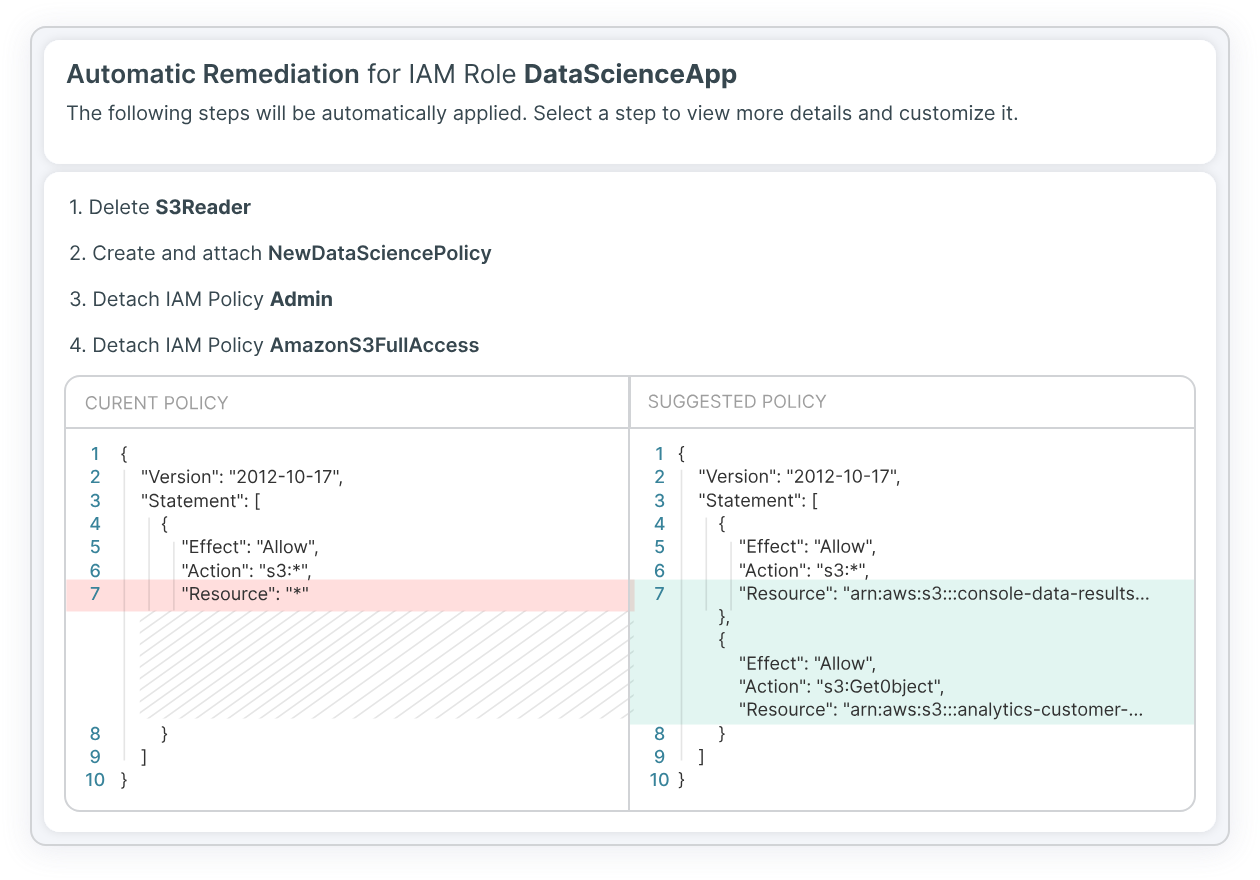
Ticket optimized policies and configuration fixes with your CI/CD pipelines
- Identity-related and access management related detection: Includes monitoring and remediation of access management guidelines, with permissions-related monitoring, for the public cloud’s unique security needs and as required by various guidelines. This capability is offered by some CSPM vendors.
Compliance officers working in cloud environments: What’s next?
Achieving compliance in the cloud starts with translating compliance guidelines to the reality of cloud architecture. Understanding which cloud assets you have, the types of vulnerabilities they’re susceptible to and how these are related to auditing guidelines is essential for enabling the ongoing compliance work of monitoring, reporting and fixing. Once you have that mapping, you can proceed to automated monitoring based on compliance or customized policies. Finally, you can generate an automated report that helps demonstrate your compliance to auditors.
Platforms exist today that combine robust CSPM and other capabilities for automating these processes, bridging the technological and manual gaps that come with compliance audit – and preventing cloud data breaches that would adversely impact compliance and the entire organization. These will free you up to focus on higher quality work like investigation, guiding the process and internal evangelism.
- Cloud

