What the Latest Shadow Brokers Dump Means for Your Business

Last week the hacker group known as Shadow Brokers published on the internet a large cache of weaponized software exploits and hacking tools targeting numerous vendor products. This fifth release appears to be the largest and most damaging to date, featuring several previously unknown exploits in widely used enterprise IT products and details on alleged U.S. capabilities to access and monitor SWIFT banking transactions. The sheer size of this leak made this weekend a challenging one for CISOs all over the world as they rushed to make sure that they weren’t vulnerable to these new exploits before attackers started using them.
The good news is that there appears to be a patch available for just about everything in the package. In some cases — such as the exploits for Windows XP and Windows Server 2003 — there will never be any patch since support for those products has long since been discontinued. Any CISOs who still have these older systems on their networks are now vulnerable to attack and will be defenseless targets to anyone who is able to get a foothold on those networks.
Many of the patches for the exploits provided by the Shadow Brokers have only just recently been released, meaning that many organizations may have not had time to run those patches through their patch management processes and get them applied to their critical systems. Of course, just because a patch is available doesn’t automatically mean your organization is safe. The pervasiveness and severity of some of the vulnerabilities in this drop makes it critical that you’re able to properly prioritize and patch every affected system in your environment.
In some cases, those patches may never be applied, whether due to a conscious decision to preserve the operational status of a crucial system, or possibly due to imperfect knowledge about what’s on the network and the impact of these blind spots on overall security. A look at historical patch MS08-67 is an excellent example. This critical vulnerability from 2008 is one that lived for years within organizations. This is the first thing that penetration testers would look for when compromising a network. MS08-67 has now been replaced by MS17-10. While there is a patch available, there will always be one machine that someone overlooked that a penetration tester or an attacker will find and use to compromise your network.
This is why conducting a proper system inventory is of such high importance to any commercial organization or government agency. You can’t protect what you don’t know. You can’t patch it either.
The Tenable research team spent the weekend reviewing the files released by the Shadow Brokers. Here are the highlights:
- Microsoft patched vulnerabilities in all supported versions of Microsoft software.
- Unsupported software such as IIS 5/6, Windows XP, Windows 2000/XP/Vista/2003, Exchange 2007 are vulnerable and should be upgraded to supported versions.
- Disable SMBv1. Microsoft and CERT have long recommended disabling SMBv1 where possible.
- A toolkit is already being leveraged to push Cobalt Strike, Metasploit, PoisonIvy, Empire and other payloads that are available as DLLs using DLL injection.
Tenable coverage and solutions
Tenable.io
Tenable has released an easy-to-use scan template for Tenable.io™ customers to quickly identify all vulnerabilities targeted by the Shadow Brokers disclosures and any derivatives that are sure to follow. For example, the template scans for MS17-010 (CVE-2017-0144) both with and without credentials:
SecurityCenter
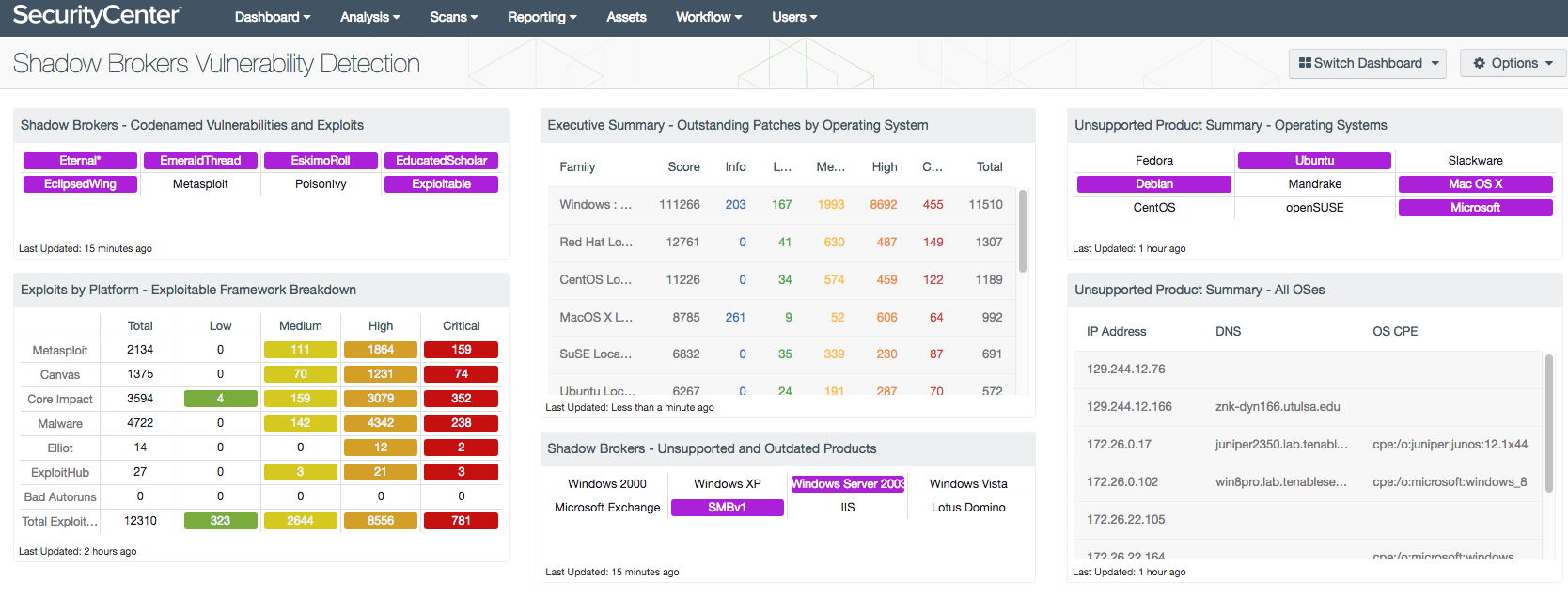
We have also developed a SecurityCenter® dashboard tailored to identify hosts that may be susceptible to the vulnerabilities and exploits published by the Shadow Brokers hacking group. The Shadow Broker Vulnerability Detection dashboard is available through the SecurityCenter Feed to provide insight into the vulnerability of your network and the progress made toward upgrading outdated hosts.
The Tenable Research Team has many plugins already available to address these vulnerabilities. We are also actively developing new plugins specific to this package. Here are the relevant solutions; we will continue to update this post as more plugins become available.
| Exploit | Plugin Title/Comments | Plugin ID |
|---|---|---|
|
EternalBlue EternalChampion EternalSynergy EternalRomance |
MS17-010: Security Update for Microsoft Windows SMB Server (4013389) |
|
|
EmeraldThread |
MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) |
|
|
EsikmoRoll |
MS14-068: Vulnerability in Kerberos Could Allow Elevation of Privilege (3011780) |
|
|
EducatedScholar |
MS09-050: Microsoft Windows SMB2 _Smb2ValidateProviderCallback() Vulnerability (975497) MS09-050: Vulnerabilities in SMBv2 Could Allow Remote Code Execution (975517) |
|
|
EclipsedWing |
||
|
EsteemAudit |
Microsoft Windows XP Unsupported Installation Detection Microsoft Windows Server 2003 Unsupported Installation Detection |
|
|
ExplodingCan |
||
|
EMPHASISMINE |
||
|
EnglishmanDentist |
||
|
DOUBLEPULSAR |
Many thanks to the Tenable research team for their contributions to this blog.
Updated May 26, 2017
- Executive Management
- Plugins
- Vulnerability Scanning