Tenable
Security Center
オンプレミスで管理できる世界 No.1 の脆弱性管理ソリューションを使ってサイバーセキュリティの弱点を顕在化して解決
IT / OT インフラ全体のリスクを低減します。脆弱性管理というカテゴリを実現したソリューションが、事業リスクを高める深刻なサイバーエクスポージャーから企業を守り続け、今も業界水準を先導しています。
デモを申し込む
オンプレミスで管理できる世界 No.1 の脆弱性管理ソリューション
Know IT の脆弱性を把握する
アクティブスキャン、エージェント、パッシブモニタリング、外部アタックサーフェス管理、CMDB 統合を組織の環境全体でフルに活用して、影響の大きい脆弱性を可視化
Expose IT の理想と現実を可視化
業界最大の CVE カバレッジを使用して素早く、確信を持って、攻撃に悪用されやすい、事業を影響する恐れのある危険度の高いエクスポージャーを付き止める
Close危険なエクスポージャーを解決
脆弱性データ、脅威インテリジェンス、データサイエンスを駆使した Tenable の予測に基づいた優先順位付けの技術を活用して、迅速に確固たる行動をとり、深刻なエクスポージャー解決して修正作業を実行
Tenable Security Center スイート
Tenable Security Center は利用者のニーズに合わせてカスタマイズできる製品スイートです。リスクを理解して脆弱性を素早く解決するのに必要な可視性と文脈を提供します。
Tenable Security Center
- リスクベースの脆弱性管理、オンプレミス
- 無制限の Nessus スキャナーでネットワークを即座に可視化
- 高度にカスタマイズ可能なダッシュボード、レポート、ワークフローを備え、データを明瞭で実行可能なインサイトに変えて提示
- 組み込みのリスクスコアとコンテキスト化された脅威インテリジェンスで、脆弱性を即座に特定し、優先順位を付ける
- カスタマイズ可能な構成アラート、通知、チケッティングにより、インシデント対応をスピードアップ
- クライアント統合、データ収集、データのエンリッチ化のための無料 API
- 今まで確認できなかった外部アタックサーフェス上の資産の検出
Tenable Security Center Plus
Tenable Security Center のすべての機能に加えて、以下が含まれます。
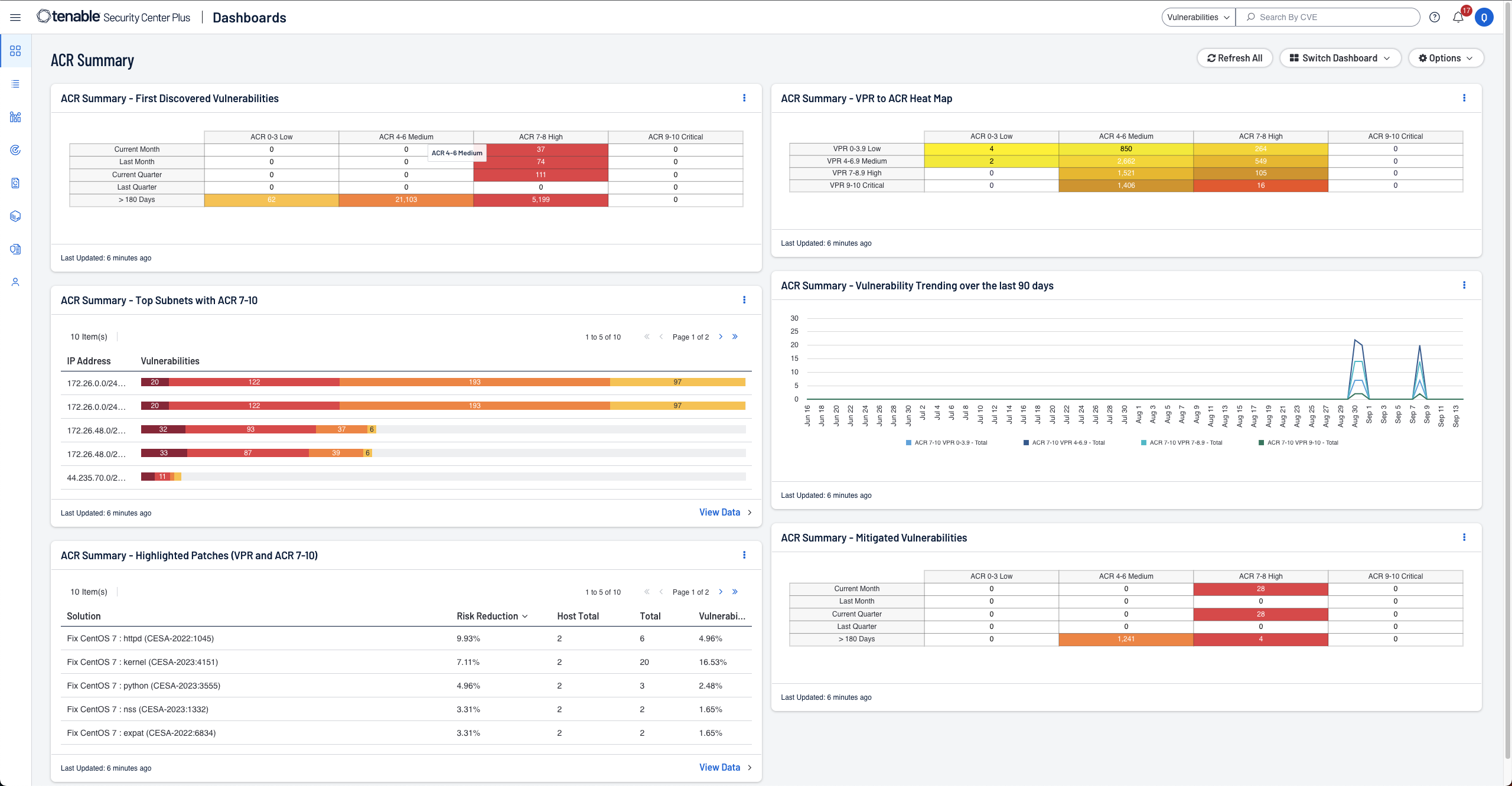
- Asset Criticality Rating (ACR) により資産をより深く理解してコンテキストを把握
- リアルタイムで資産や脆弱性を検出し、最高レベルの可視性を実現する継続的モニタリング
- リアルタイムメトリクスや違反に対する事前アラートで合理化されたコンプライアンス報告
- ボットネットおよびリモートトラフィックのリアルタイム検出
- これまで知られていないリソース、挙動変化、新しいアプリケーションの使用方法を洗い出す
Tenable Security Center Director
複数の Tenable Security Center コンソールをご使用中のお客様は、Tenable Security Center Director を Tenable Security Center または Tenable Security Center Plus のアドオンとしてご利用いただけます。
- すべての Tenable Security Center コンソールにまたがるネットワークを単一の画面で表示および管理が可能
- Tenable Security Center の各コンソールのスキャンを 1 か所から簡単に表示
- 複数のコンソール、スキャナー、資産のレポートと稼働時間を容易に把握できる一元化された洞察
- 複数の Tenable Security Center コンソールからのレポートが一元化され、サイバーリスクを簡単に測定可能
セキュリティリスクやコンプライアンスリスクを素早く測定して分析
-
自由に選べるデータ管理方法
脆弱性管理をリードするオンプレミスソリューションである Tenable Security Center をぜひご利用ください。オンプレミスまたはハイブリッドでの導入で活用できる柔軟なオプションが用意されており、組織のリスクを軽減しながらデータ管理を行えます。 -
資産の重要度を把握
Tenable Security Center Plus には、資産重要度の格付け (ACR) が導入されており、資産の重要度について深い理解を得られます。組織のリスク軽減のため、情報に基づいた意思決定を行うのに必要な知識を身につけましょう。 -
脅威を先行的に文脈化する
Tenable Research がサポートする豊富なデータとインテリジェンスに基づいて、脆弱性を検索、コンテキスト化、対応します。方法を見る -
即時にデータの詳細情報を得る
-
レポートを簡単にカスタマイズ
特定の対象者向けに設計されたさまざまなレポートを作成することで、重大な脅威に即座に対応できます。オンデマンドまたはスケジュールに従ってレポートを作成し、担当者に自動的に配信して共有することができます。 -
コンプライアンスレポート作成を簡略化
コンプライアンスを維持し、企業のコンプライアンス体制を即座に可視化できるようにします。業界標準と規制要請に基づき事前定義されたチェック項目を用いて、コンプライアンスの遵守を容易に実証します。 -
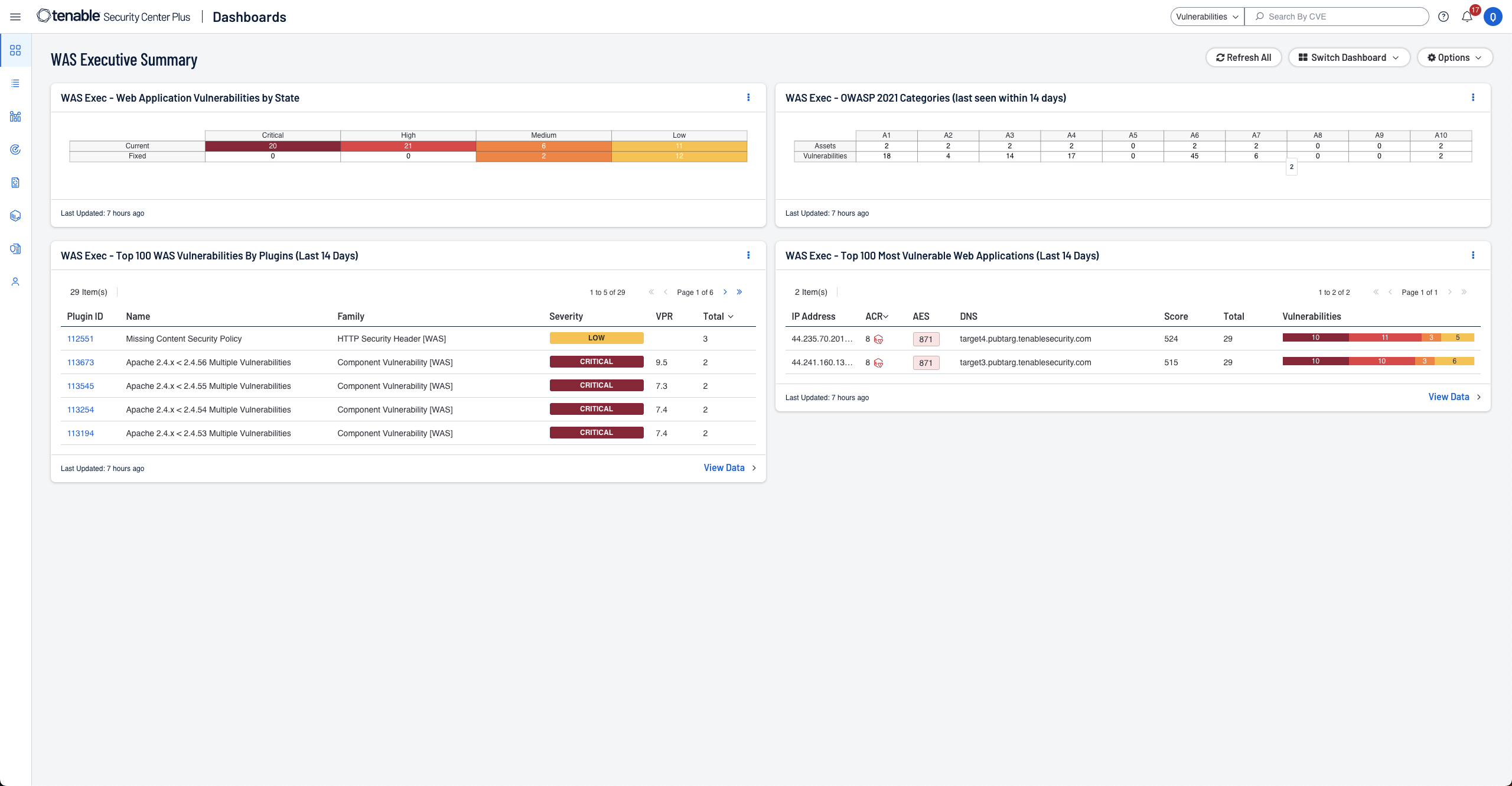
オンプレミスのウェブアプリケーションスキャン
オンプレミスの Tenable Web App Scanning を Tenable Security Center の UI 内に統合しました。ユーザーフレンドリーな最新のウェブアプリケーション脆弱性スキャンにより、スキャンの自動化、ウェブアプリケーションの脆弱性評価、評価の効率化が可能です。 -
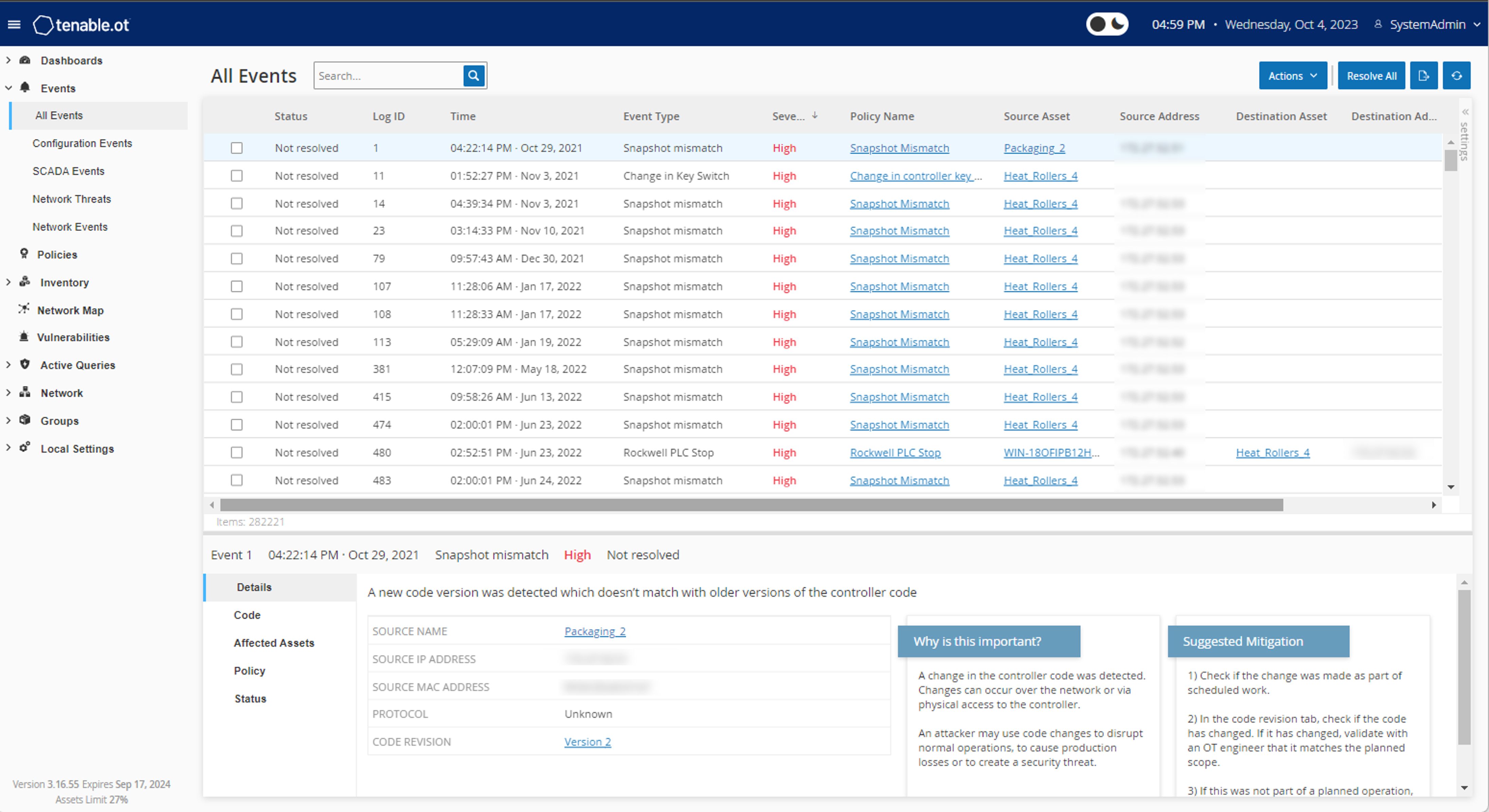
オペレーショナルテクノロジー (OT) における可視性を強化
Tenable OT Security との統合により、組織を危険にさらすサイバーフィジカル (OT/IoT) 脅威に対する可視化・防御・統制を包括的に実現します。 -
脆弱性のエクスポージャーを解決
自動パッチ機能と、Tenable の優れた脆弱性カバレッジ、組み込みの優先順位付け、脅威インテリジェンス、リアルタイムの洞察を組み合わせることで、修正までの平均時間 (MTTR) を短縮します。方法を見る

Tenable One が提供する 世界唯一の AI を活用したサイバーエクスポージャー管理プラットフォーム
Tenable One は現代のセキュリティの中核にある課題 - サイバーリスクの捉え方と対処方法が深く断片化されていること - を解決します。Tenable はセキュリティの可視性、インサイト、行動をアタックサーフェス全体で統合してリスクを削除し、迅速にセキュリティギャップを可視化して解決していきます。Tenable One は、危険度の高いサイバー上の弱点を排除し、ITインフラ、クラウド環境、基幹インフラ、その他のあらゆる環境を攻撃から守るために世界のお客様によってご利用いただいています。
もっと詳しく
Tenable Security Center は、当社のネットワークにおける現状を正しく伝えてくれます。説明責任を裏付ける一層深い知見を得られるので、セキュリティプログラムがうまくいっていることが検証でき、役員会に伝えることがができます
よくあるご質問
Tenable Security Center とは?
-
Tenable Security Center および Tenable Security Center Plus は、Tenable のオンプレミス脆弱性管理ソリューションです。業界をリードする Nessus テクノロジーに基づいて構築された Tenable Security Center 製品ファミリーを使用すると、脆弱性を特定、調査、優先順位付けして、セキュリティとコンプライアンスの態勢をリスクベースで把握できるようになります。これらのソリューションの詳細については、Tenable Security Center データシートおよびTenable Security Center Plus データシートを参照してください。
Tenable Security Center と Tenable Security Center Plus の違いは?
-
Tenable Security Center Plus は、Tenable Security Center の機能に基づいて構築された脆弱性管理プラットフォームです。資産と脆弱性のコンテキストに関する追加の情報として、資産重要度評価 (ACR) などのさらなるリスク指標を提供します。これらのメトリクスにより、脆弱性管理プログラムにおいてよりカスタマイズしたアプローチが可能になる上、すべて Tenable Security Center Plus インスタンス上で計算されるため、データをオンプレミスに残すことができます。さらに、Tenable Security Center Plus を Tenable のサイバーエクスポージャー管理プラットフォームである Tenable One と統合すると、Security Center Plus が提供する情報の価値をさらに高めることができます。
Tenable Security Center は Tenable One と連携できますか?
-
はい。Tenable Security Center Plus は Tenable One と統合した場合、ハイブリッドな脆弱性管理ツールとして配備できるので、オンプレミスのお客様にとってエクスポージャー管理プラットフォームの利点を有効に活用できるソリューションになります。
Tenable One とは?
-
Tenable One は、サイバーエクスポージャー管理プラットフォームです。現代のアタックサーフェス全体の可視化、起こり得る攻撃を防ぐための取り組みへのフォーカス、エクスポージャーリスクの正確な伝達を支援することで、最大限のビジネスパフォーマンスを発揮できるようにします。このプラットフォームは、Tenable Research による高速で広範な脆弱性カバレッジを基盤として構築されており、IT 資産、クラウドリソース、コンテナ、ウェブアプリケーション、ID システムにわたる、業界で最大の網羅性を誇る脆弱性カバレッジを提供します。また、包括的な分析機能により、作業の優先順位付けやサイバーリスクの伝達を可能にします。 Tenable One は、以下を実現します。
- 現代のアタックサーフェス全体の包括的な可視化
- 脅威を予測し、攻撃を防ぐための作業の優先順位付け
- より適切な判断を可能にする、サイバーリスクの伝達
Tenable Security Center Director とは?
-
Tenable Security Center Director は、Tenable Security Center のアドオンです。これにより企業のお客様は、複数の Tenable Security Center コンソールにまたがる大規模で分散したネットワーク全体を単一の画面から確認できます。Tenable Security Center Director ではインスタンスの完全な可視化と管理が可能なため、脆弱性管理への集中と管理業務のオーバーヘッド削減が可能です。
Tenable Security Center は Tenable Web App Scanning と連携していますか?
-
Tenable Security Center を使用すると、Tenable はオンプレミスのウェブアプリケーションセキュリティを導入することで防御を強化できます。Security Center の UI にシームレスに統合された Tenable Web App Scanning により、ネットワークおよび ウェブアプリケーション全体の脆弱性を特定して対処できるようになり、セキュリティ態勢が強化されます。
Tenable Web App Scanning は、ウェブアプリケーションを徹底的に評価する動的アプリケーションセキュリティテスト (DAST) ツールです。ウェブアプリケーションをクロールしてサイトマップを作成し、フロントエンドをスキャンしてカスタムコードとサードパーティコンポーネントの脆弱性を検出します。
予測に基づいた優先順位付けとは何のことで、脆弱性の優先順位付けにどのように役立つのですか?
-
予測に基づいた優先順位付けは、Tenableが収集した脆弱性データをサードパーティーの脆弱性や脅威データと組み合わせ、Tenable Researchが開発した最新のデータサイエンスアルゴリズムを活用して分析します。どの脆弱性にも Vulnerability Priority Rating (VPR) が付与され、深刻度 (severity)とともにその脆弱性が次の28日間に攻撃に悪用される可能性が数値で表されます。VPR を使えば、ユーザー企業環境内での脆弱性のサイバーリスク度が把握できるので、最も影響を受けると考えられる脆弱性の修正を優先することができます。
Tenable Security Center はどのようにして資産と脆弱性を検出しますか?
-
Tenable Security Center は、さまざまなセンサーでネットワーク、資産、脆弱性をリアルタイムで継続的に検出および評価します。
Tenable Security Center は、次のようなソースを使用して企業全体からセキュリティデータを収集します。
- パッシブモニタリング : ネットワークトラフィックやイベントをリアルタイムで監視することで、インターネットに接続している資産や、その通信状況に関する情報を提供します。新規または未知のデバイスやアプリケーションを識別し、疑わしい動作をその都度検出します。
- アクティブスキャ二ング :資産の状態を徹底的に分析し、脆弱性、不適当な構成、マルウェアやその他の弱点を識別します。
- ホストデータ : アクセスや変更に関するインサイトを含むホストアクティビティやイベントを積極的にモニタリング
- インテリジェントコネクター : Tenable Security Center では、他のセキュリティ投資を活用して追加のセキュリティデータを統合すると、コンテキストと分析の改善も可能です。どちらも、Active Directory (AD)、設定管理データベース (CMDB)、パッチ管理システム、モバイルデバイス管理 (MDM) システム、クラウド プラットフォーム、ウェブアプリケーションなどを含む幅広いデータソースからの情報を分析します。
- エージェントスキャン : 認証情報なしでインターネットに断続的に接続している一時的な資産や、スキャンが困難な資産を瞬時に監査します。インストール後、エージェントは継続的なホストの認証情報なしで、認証スキャンを実行することができます。
Nessus Agent とは? Tenable Security Center とどのように連携しますか?
-
Nessus Agentsはホスト (ノートパソコン、仮想システム、デスクトップおよび/またはサーバー) 上でローカルにインストールする軽量のプログラムです。エージェントは中央 Nessus Manager サーバーからスキャン命令を受け取り、スキャンをローカルで実行し、脆弱性、コンプライアンス、およびシステム結果のレポートをを中央サーバーに返します。Nessus Agent は、Tenable Vulnerability Management および Tenable Security Center で利用できます。
Tenable Security Center と Nessus Agent を利用する場合、継続的なホスト認証情報が必要な資産やオフライン資産など、問題のある資産のスキャンが容易になるので、スキャン範囲の拡大や盲点の排除が可能です。エージェントを使用することで、ネットワークに影響をほとんど与えることなく大規模な同時スキャンを実行することもできます。
Nessus Agent の詳細については、以下のリソースをご確認ください。
Tenable Security Center は何種類の脆弱性を検出しますか?
-
Tenable Research は、Tenable Security Center をサポートしており、世界トップクラスの Cyber Exposure インテリジェンス、データサイエンスのインサイト、アラート、セキュリティアドバイザリを提供しています。Tenable は業界でも最大級の広範囲な脆弱性とインテリジェンスのデータセットを保持しており、CVE カバレッジは 79,000 個以上で最大数を誇り、2019 年 1 月以来、476 個のゼロデイ脆弱性を公開しています。新たな脆弱性は毎日出現するため、Tenable は脆弱性データベースを毎日更新しています。Tenable Research は 100 件以上の検出結果を毎週配信しています。
Tenable Security Center が脆弱性を検出した後はどうなりますか?
-
Tenable Security Center が脆弱性を検出すると、検出された各脆弱性に関する次のような詳細情報が得られます。
- 脆弱性情報 : 脆弱性の名称や説明、修正方法、発見日や脆弱性が観察された直近の日付、CPE、パッチの配布日、パッチ状況、プラグイン ID と詳細
- ホスト情報 : ホスト名、影響を受けたホスト、IP アドレス、DNS、Mac アドレス、NetBIOS、レポジトリ
- リスク情報 : 脆弱性の重大度、VPR スコア、CVSS スコアおよびベクトル、脆弱性の経過時間、既知のエクスプロイト、エクスプロイトコード成熟度、製品カバレッジ、脅威の強度、脅威の最新性、脅威のソース、パッチングによりリスク軽減される割合
Tenable Security Center のレポート機能とは?
-
Tenable Security Center には、非常に柔軟なレポート機能があります。これを利用すると、350 を超える事前構築済みのテンプレートとユーザーフレンドリーなレポート作成インターフェースから、カスタマイズしたレポートを簡単に作成できます。HTML5 形式のレポートは、各部門のデータを集約できるので、企業全体のセキュリティ対策の効果を測定したり分析したりすることができます。 既存のテンプレートを使用して、特定の項目を追加または削除したり、フィルターを調整してデータを完全にカスタマイズすることで、さまざまなニーズに合うレポートを作成できます。
自社の適切なチームや意思決定者に有益でタイムリーなレポートを提供するために、収集したデータを異なる観点から分析した複数のカスタムレポートを作成することもできます。レポートは極めて詳細なものから、高レベルなサマリーまで様々な種類の作成が可能です。出力には標準的な PDF 形式と CSV 形式が利用できます。スケジュールを設定して自動的にレポートをメールで配信したり、特定のコンソールユーザーと共有したり、さらに完成したレポートをウェブサイトに発行したりすることもできます。
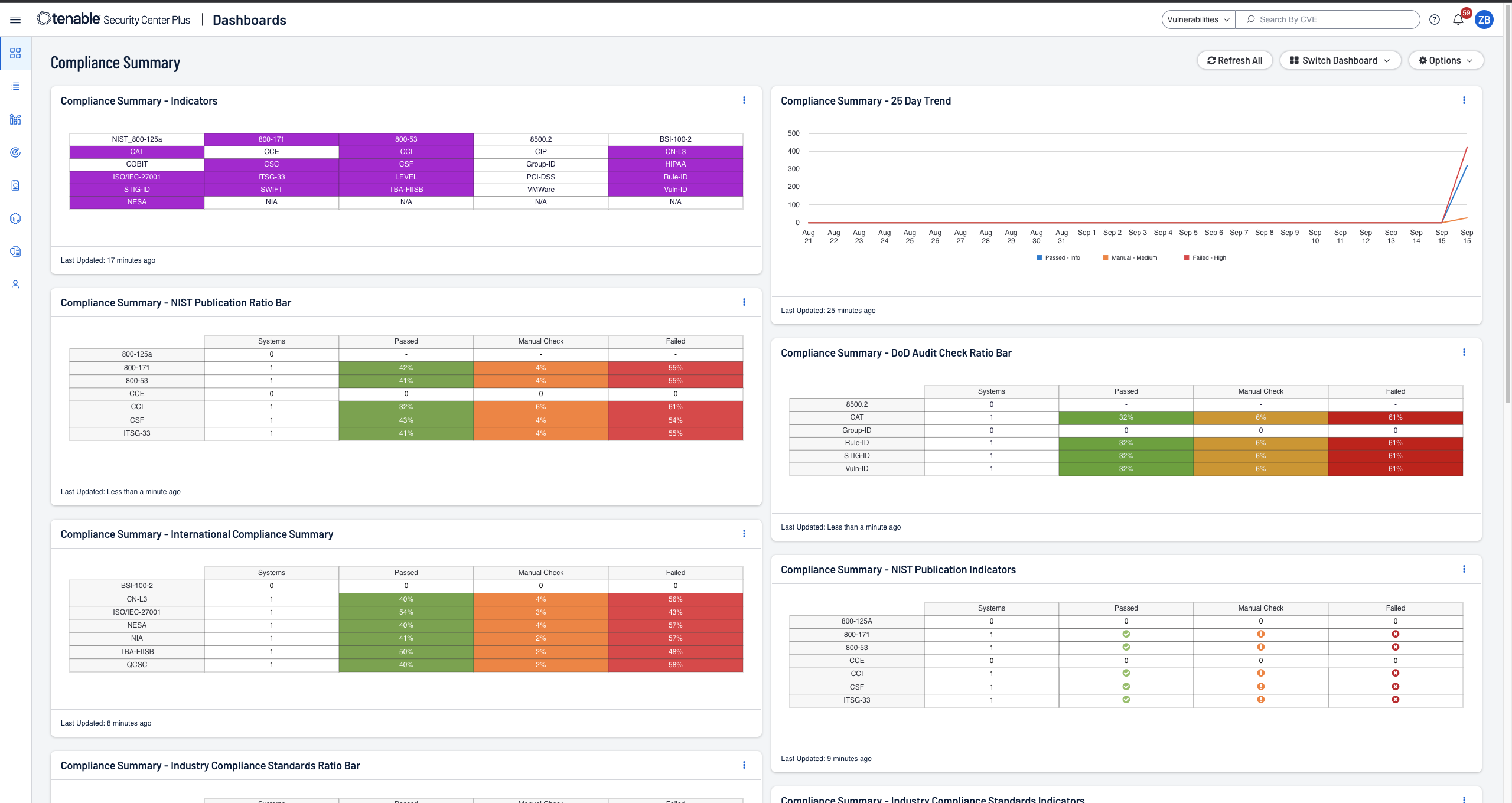
Tenable Security Center では、PCI や NIST といった複雑な標準に対するネットワークの準拠状況を包括的かつ自動的にレポートすることもできます。
Tenable Security Center はコンプライアンスの維持に役立ちますか?
-
はい。Tenable Security Center はコンプライアンスの維持に役立ちます。コンプライアンス態勢がリアルタイムで可視化されているので、適合している状態の維持と監視が可能です。ISO/IEC 27001/27002、PCI、NIST サイバーセキュリティフレームワーク、NIST SP 800-171、CIS Critical Controls などの業界標準や規制要件に対する事前定義済みのチェックリストが用意されているので、遵守しているかどうかを簡単に実証できます。
Tenable Security Center には、主要なセキュリティ標準とコンプライアンス義務に特化した、すぐに使用可能かつ完全にカスタマイズ可能なレポートとダッシュボードが備わっています。標準装備のままでも、特定のセキュリティやビジネスのニーズに合わせてカスタマイズしてお使いいただくことも可能です。例えば、事業部門ごとのレポートやダッシュボードも簡単に作成することができます。
Tenable AI Aware とは何ですか?
-
Tenable AI Aware は Tenable Vulnerability Management および Tenable Security Center の一部として提供される機能です。急速な人口知能テクノロジーの導入にかかわるリスクを監視して緩和することを支援します。高度の検出技術 (エージェント、パッシブネットワーク監視、ダイナミックなアプリケーションセキュリティテスト(DAST)、スキャンエンジンの分散配置など) によって無断で使われている AI ソリューションを特定し、AI の脆弱性を検出し、想定外の AI や 大規模言語モデル (LLM) の開発に光を当てます。AI Aware は、組織のデジタルエコシステムの各所にある AI ソフトウェア、ライブラリ、ブラウザのプラグインを奥深く可視化して、AI 関連のリスク管理に包括的なセキュリティ第一のアプローチを提供します。Tenable AI Aware について詳細はこちらから。
外部アタックサーフェス管理 (EASM) とは何ですか?
-
外部アタックサーフェス管理は、ネットワーク境界の外側の盲点を可視化する Tenable が提供する機能です。ドメイン内をスキャンして、従来確認できなかったインターネットに接続された資産を検出します。ネットに露出している資産は、企業にとって高度のリスクとなる恐れがあります。
Tenable Security Center では外部アタックサーフェス管理が可能ですか?
-
はい。Tenable Security Center には外部アタックサーフェス管理機能が備わってます。結果に追加のドメイン、頻度、メタデータが必要な場合、Tenable Attack Surface Management アドオンをご購入ください。
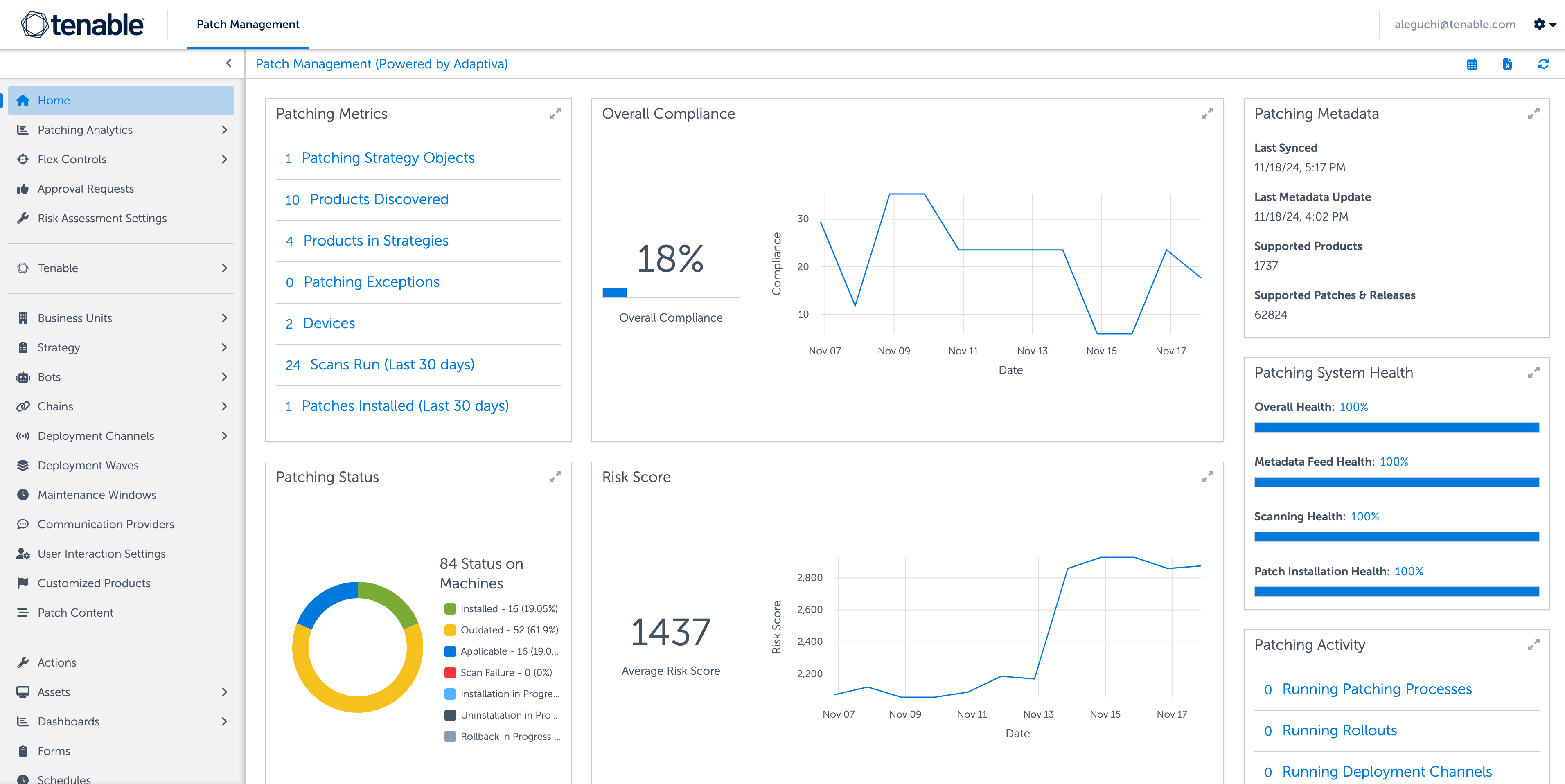
Tenable Patch Management とは?
-
Tenable Patch Management は、業界をリードする Tenable の優先順位付け機能と自律パッチ機能を組み合わせたパッチ管理モジュールです。脆弱性と最新の修復アクションの自動関連付けにより、脆弱性の優先順位付けと修復の間に発生する可能性のあるボトルネックを克服できます。Tenable Patch Management は、あらゆる組織に合わせてスケールアップまたはスケールダウンできるように構築されています。これを使用することで、組織はデプロイメント、テスト、承認、アプリケーションなどの設定をきめ細かく正確に管理できます。
Tenable Patch Management を使用するには、Tenable Vulnerability Management、Tenable Security Center、Tenable One、または Tenable Enclave Security のライセンスが必要です。詳細はこちら。
Tenable Security Center は他の製品と統合されていますか?
-
はい。Tenable Security Center は他の製品と統合されています。 Tenable の脆弱性に対するインサイトをチケッティングやパッチ管理ソリューション、SIEM、SOAR、その他のサードパーティ製品に活用できるように、標準装備として統合されています。テクノロジーエコシステムページから、ご利用いただける統合サービスやエコシステムパートナーの詳細をご覧ください。Tenable Security Center の API を利用すると、カスタマイズした統合を開発することもできます。
さらに、Tenable Security Center には、Tenable OT Security、Tenable Web App Scanning、Tenable Patch Management との統合が組み込まれています。Tenable Security Center Plus は Tenable One と統合されており、ハイブリッド脆弱性管理の導入、オンプレミスの顧客によるサイバーエクスポージャー管理プラットフォームの利用が可能となります。
Tenable Security Center の価格とライセンスはどのように設定されますか?
-
Tenable Security Center は年間サブスクリプションによってライセンスが付与され、IP によって価格が設定されます。永久ライセンスもご用意しています。
Tenable Security Center のドキュメントはどこにありますか?
-
Tenable Security Center およびすべての Tenable 製品の技術ドキュメントは、https://docs.tenable.com/にあります。
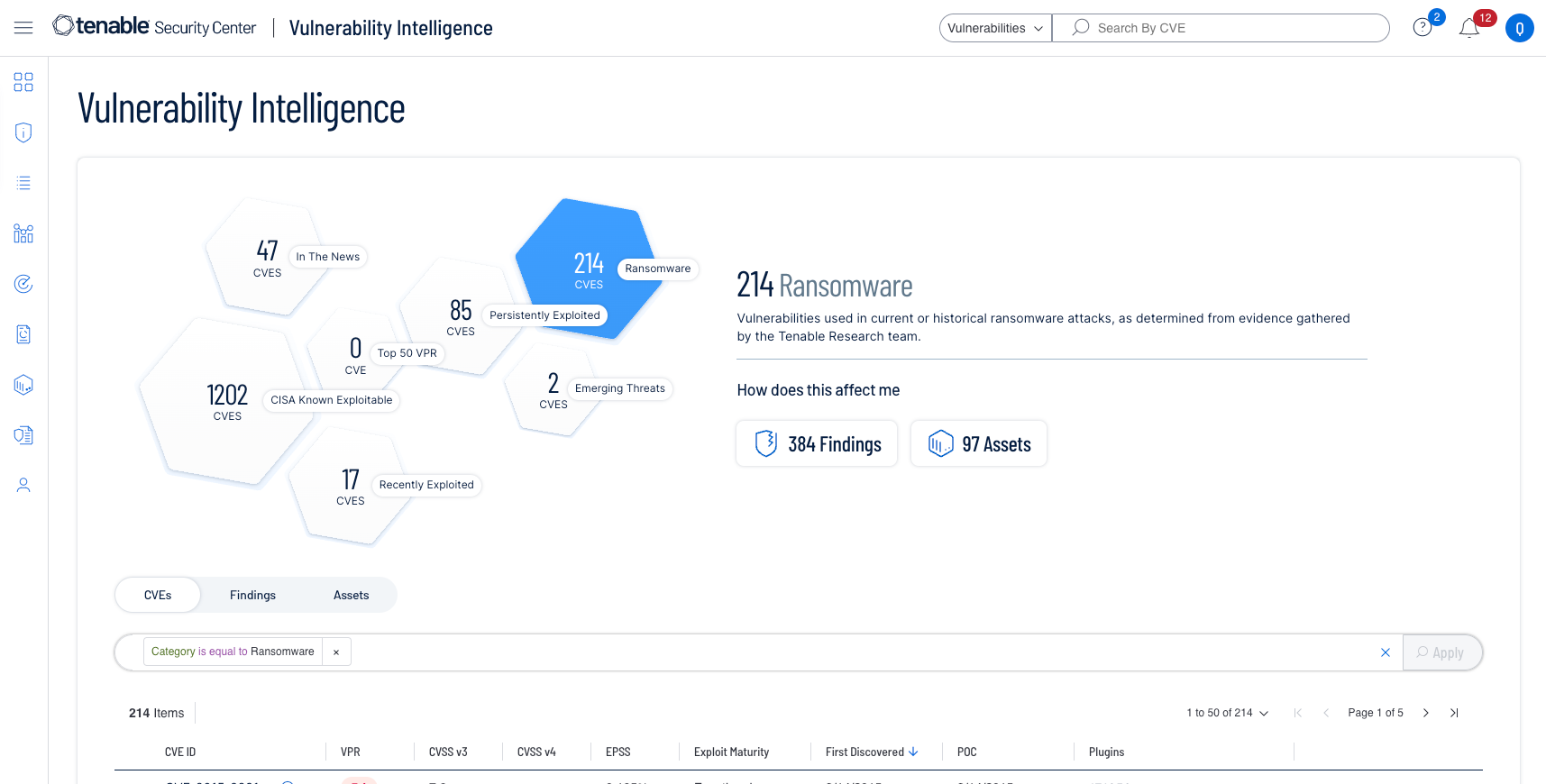
- Vulnerability Intelligence とは?
-
Vulnerability Intelligence とは、外部のデータソースと内部の脆弱性データに基づき、脆弱性管理に実用的なインサイトを提供する機能です。あらゆる脆弱性の極めて重要な文脈を提供するため、脆弱性を攻撃者が悪用する可能性の程度や、自組織の環境への影響範囲を把握できるようになります。
Vulnerability Intelligence は、Tenable の広範な脆弱性調査情報、データサイエンスの洞察、セキュリティ対応、脆弱性管理データを 1 つの統合された場所にまとめます。この豊富なインテリジェンスに基づくことで、脆弱性の調査や文脈を踏まえた対応が簡単になったり、脆弱性が組織に与える影響を経営陣に報告したりできます。
関連製品
関連リソース
Tenable Security Center のデモを予約
右のフォームに連絡先をご記入ください。営業担当者がらデモのスケジュールについてご連絡いたします。
- Tenable Security Center