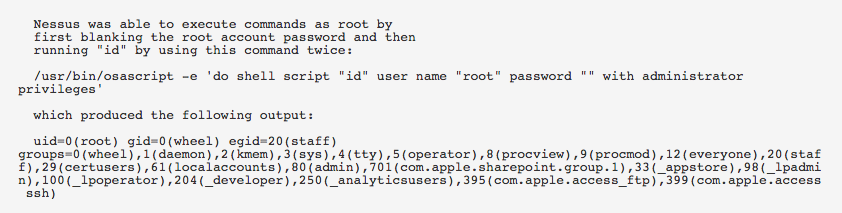
Detecting macOS High Sierra root account vulnerability (CVE-2017-13872)
On November 28, 2017 a software developer (Lemi Orhan Ergin) reported a critical flaw in macOS High Sierra which allows any local user to log in as root without a password after multiple attempts. The vulnerability was originally thought to only be exploitable if you had physical access to the computer, but our researchers have been able to exploit this vulnerability to elevate privileges over an authenticated Secure Shell (SSH) session using a lower privileged account and remotely using Virtual Network Computing (VNC) if screen sharing is enabled.
Understanding the Root Cause
Patrick Wardle provides a very in-depth discussion on the root cause (no pun intended) of the issue. When a person (authorized or unauthorized) tries to login to a macOS High Sierra system and the account is not enabled (i.e. root), a new account is created with the password supplied to the GUI. Even if the password is empty, a new account will be created with a blank password. Regardless of attempting to log in over the keyboard, VNC, or over an authenticated SSH session, the new account is created on the first attempt, and then you are able to login the second attempt.
If you are a home user and have not enabled SSH or VNC, then you are not at risk to remote attacks. For corporate environments, this vulnerability is very real problem, as most of the management tools use remote access like SSH and VNC. Many management systems, like Nessus® and Tenable.io™, use SSH to perform management operations. Therefore, organizations that have users with macOS High Sierra computers are at extreme risk to this vulnerability.
Detecting Vulnerable Hosts
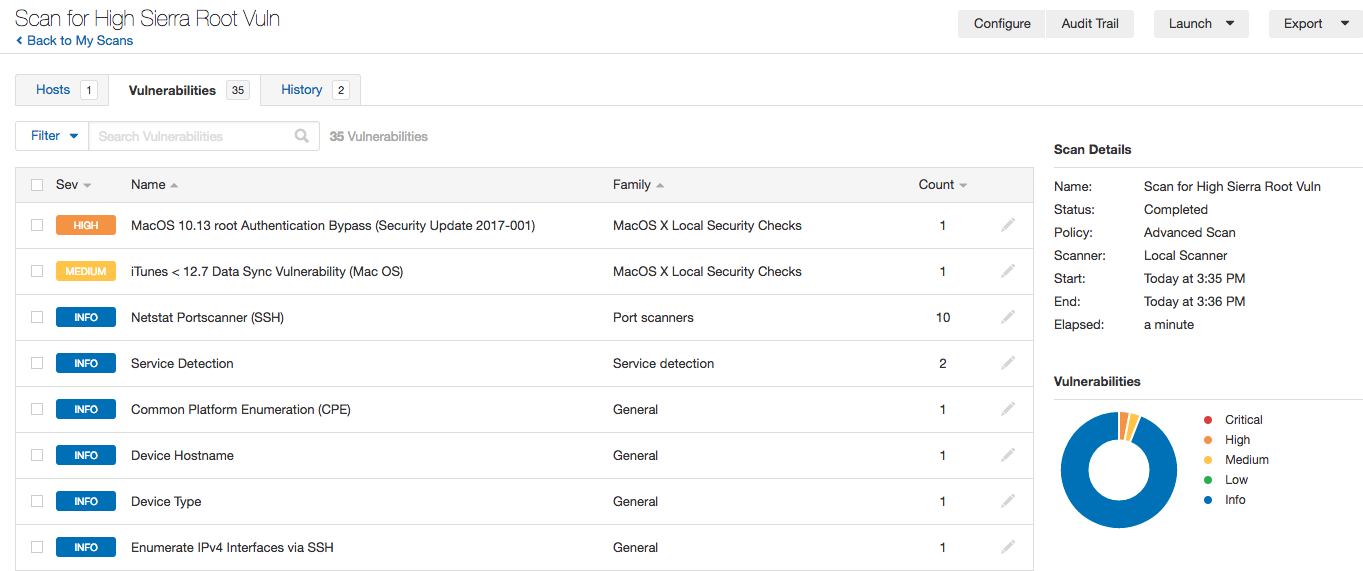
We are releasing several plugins to detect vulnerable hosts. Plugin #104814 detects whether patch (Security Update 2017-001) has been applied on the target host. Plugin #104848 tries to confirm the existence of a vulnerability by escalating privileges from a non-admin/non-root user to a root user. The plugin is only enabled when ‘safe checks’ are disabled since it changes the system state by disabling the root account if the host is vulnerable and has a blank root password set. Please review ‘Advanced Scan Policy Steps’ for instructions to enable this plugin.
- macOS 10.13 root Authentication Bypass (Security Update 2017-001) (104814)
- macOS 10.13 root Authentication Bypass Direct Check (104848)
- macOS 10.13 Authentication Bypass Remote Check (CVE-2017-13872) (105003)
Advanced Scan Policy Steps
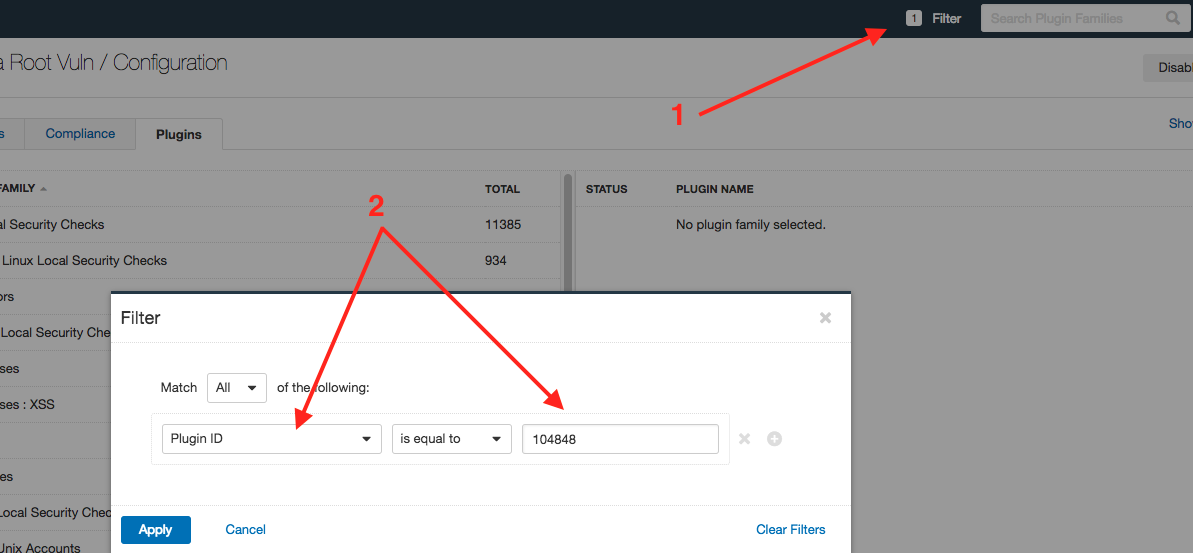
When executing the macOS 10.13 root Authentication Bypass Direct Check (104848) plugin, we recommend scanning systems with a non-root account. To set-up a scan for this vulnerability, you will need to follow these steps:
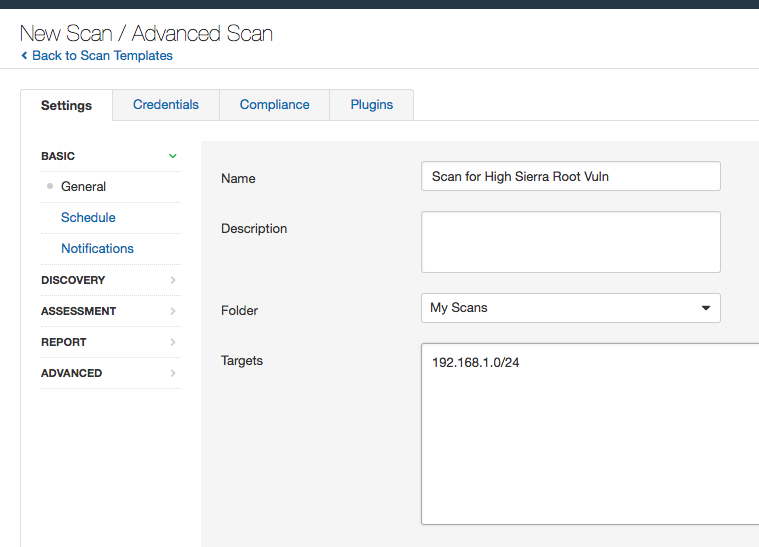
1. Add a new scan and choose advanced scan.
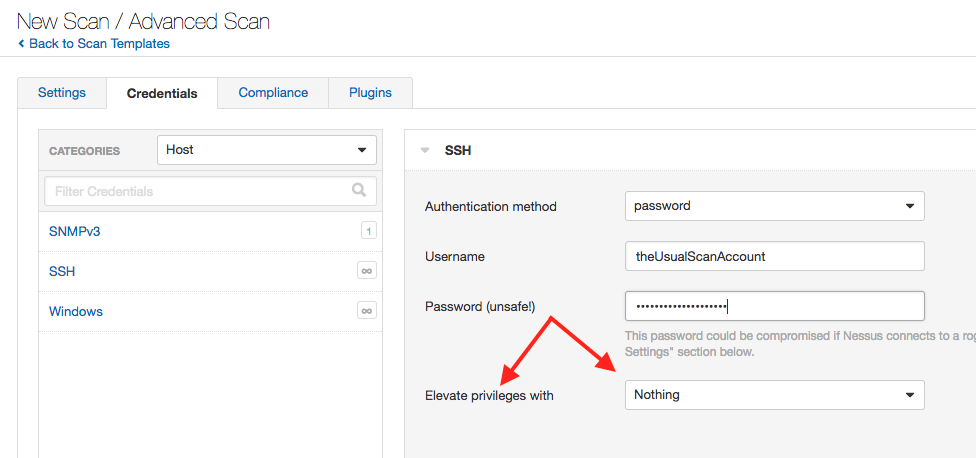
2. Next, add the credentials. Remember to use an account but set the “Elevate privileges with” to “Nothing.” The key to using this plugin is to use the same account that scan with, but no escalation is authorized. All the systems you are scanning need to have the same account, which is common for scanning.
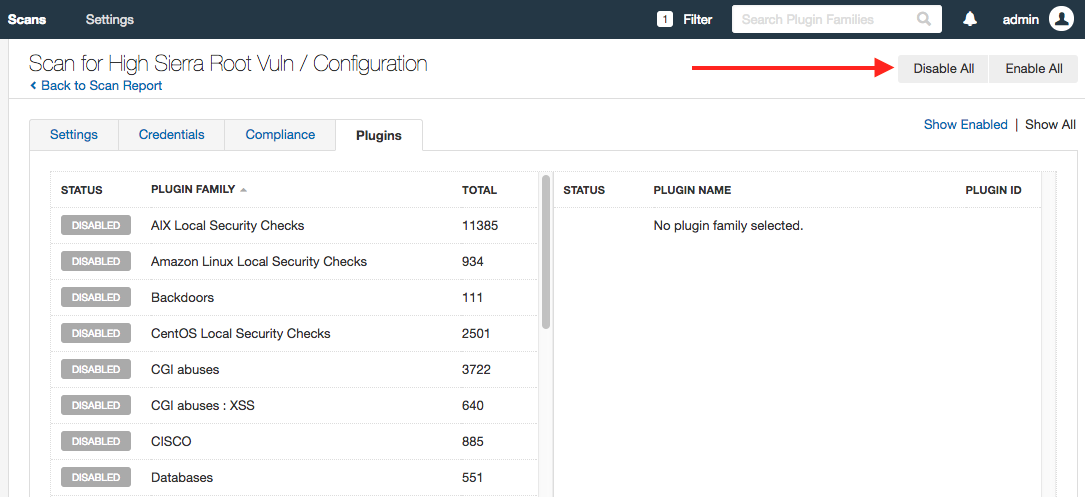
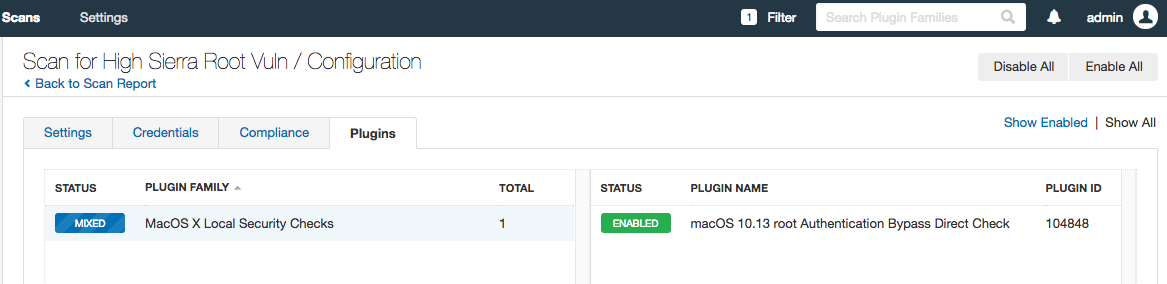
3. Next, disable all other plugins, and then enable only the plugin 104848.
(Disable all other plugins)
(Search for the plugin)
(Enable the single plugin)
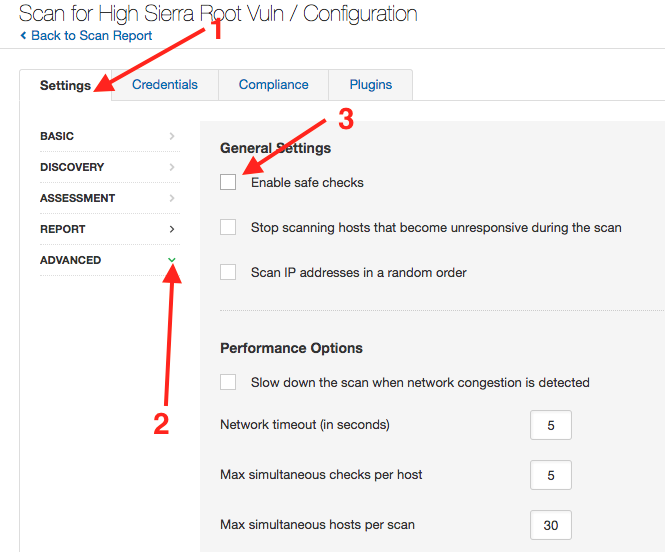
4. Disable Safe Checks. This setting can be found under ‘Advanced’ in the setting menu. NOTE: Scanning with agents is not supported due to the inability to disable safe checks.
5. After selecting the plugins, add in the target range and scan your targets.
How Does the Plugin Work?
Plugin #104848 exploits the privilege escalation vulnerability to verify the system is vulnerable. The plugin works as follows:
- Nessus or Tenable.io will scan the system with the account you supplied in the advanced policy. Note that this must be a non-root account. After logging in, the scanner will attempt to run a command as the root user, authenticating with a blank password. If the host has the root account disabled and is vulnerable, this will cause the host to enable the root account and set a blank password, even though the attempted command will fail.
- The scanner attempts to run this command again, and if the host is vulnerable it will now succeed.
- If root access is granted, then the plugin runs a clean-up process that does the following:
- Disables the root account
- Removes the blank password hash for the root account
Patch Update
If you recently applied the patch and then upgraded to macOS 10.3.1, you will need to reapply the security patch.
Wrapping Up
We continue to research this vulnerability, and investigate different ways to detect the vulnerability. When we have new information, we will release additional plugins.
This vulnerability is a real and present danger to all organizations and should be patched immediately. Apple recently released a patch to resolve this vulnerability. Customers with a tightly controlled patch cycle or change control process should consider asking for an exception for the patch, as allowing systems vulnerable to this privilege escalation to go un-patched for any period of time could be devastating to your network. Should a malicious user gain access to one of these systems, the attacker could begin causing all sorts of havoc on the network for some time.
Note: This blog post was updated on Dec. 4, 2017 with plugin 105003 and a note about reapplying the patch after upgrading.