Microsoft’s September 2025 Patch Tuesday Addresses 80 CVEs (CVE-2025-55234)

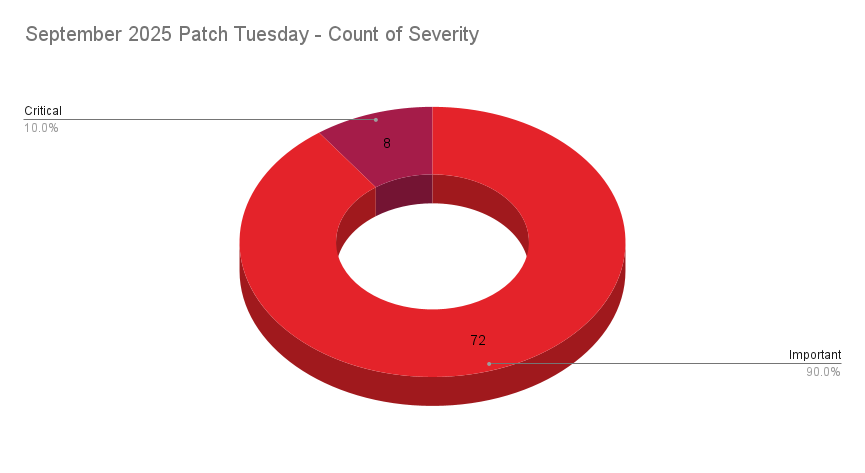
- 8Critical
- 72Important
- 0Moderate
- 0Low
Microsoft addresses 80 CVEs, including eight flaws rated critical with one publicly disclosed.
Microsoft addresses 80 CVEs in its September 2025 Patch Tuesday release, with eight rated critical, and 72 rated important. Our counts omitted one vulnerability reported by VulnCheck.
This month’s update includes patches for:
- Azure Arc
- Azure Windows Virtual Machine Agent
- Capability Access Management Service (camsvc)
- Graphics Kernel
- Microsoft AutoUpdate (MAU)
- Microsoft Brokering File System
- Microsoft Graphics Component
- Microsoft High Performance Compute Pack (HPC)
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office PowerPoint
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Office Word
- Microsoft Virtual Hard Drive
- Role: Windows Hyper-V
- SQL Server
- Windows Ancillary Function Driver for WinSock
- Windows BitLocker
- Windows Bluetooth Service
- Windows Connected Devices Platform Service
- Windows DWM
- Windows Defender Firewall Service
- Windows Imaging Component
- Windows Internet Information Services
- Windows Kernel
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Management Services
- Windows MapUrlToZone
- Windows MultiPoint Services
- Windows NTFS
- Windows NTLM
- Windows PowerShell
- Windows Routing and Remote Access Service (RRAS)
- Windows SMB
- Windows SMBv3 Client
- Windows SPNEGO Extended Negotiation
- Windows TCP/IP
- Windows UI XAML Maps MapControlSettings
- Windows UI XAML Phone DatePickerFlyout
- Windows Win32K GRFX
- Xbox

Elevation of Privilege (EoP) vulnerabilities accounted for 47.5% of the vulnerabilities patched this month, followed by Remote Code Execution (RCE) vulnerabilities at 27.5%.
CVE-2025-55234 | Windows SMB Elevation of Privilege Vulnerability
CVE-2025-55234 is an EoP vulnerability affecting Windows Server Message Block (SMB). It was assigned a CVSSv3 score of 8.8 and rated as important. Successful exploitation would allow an unauthenticated attacker to elevate their privileges to that of the compromised user's account. According to Microsoft, this vulnerability was publicly disclosed prior to a patch being made available.
CVE-2025-55234 appears to have been released to help customers audit and assess their environment and identify incompatibility issues prior to utilizing some of the hardening capabilities for SMB Servers.
CVE-2025-55234 is the fifth Windows SMB vulnerability patched in 2025 and the third Windows SMB EoP disclosed this year. In the June 2025 Patch Tuesday release, Microsoft patched CVE-2025-33073, another publicly disclosed Windows SMB EoP vulnerability. A day after the June 2025 Patch Tuesday release, researchers from RedTeam Pentesting GmbH, one of many researchers credited with reporting the flaw to Microsoft, released a blog post detailing the vulnerability, including proof-of-concept details.
CVE-2025-54918 | Windows NTLM Elevation of Privilege Vulnerability
CVE-2025-54918 is an EoP vulnerability in Windows New Technology LAN Manager (NTLM). It was assigned a CVSSv3 score of 8.8 and is rated critical. It was assessed as “Exploitation More Likely” according to Microsoft’s Exploitability Index. According to the advisory, successful exploitation would allow an attacker to elevate their privileges to SYSTEM.
This is the second month in a row that a critical NTLM EoP vulnerability was patched and the third in 2025. In the August 2025 Patch Tuesday release, Microsoft patched CVE-2025-53778, and CVE-2025-21311 in the January 2025 Patch Tuesday release.
CVE-2025-54916 | Windows NTFS Remote Code Execution Vulnerability
CVE-2025-54916 is a RCE in Microsoft Windows New Technology File System (NTFS). It was assigned a CVSSv3 score of 7.8 and is rated important and assessed as “Exploitation More Likely.” An attacker that successfully exploits this flaw would gain RCE on the targeted system. According to the advisory, any authenticated attacker could leverage this vulnerability.
Since 2022, the bulk of NTFS vulnerabilities patched across Patch Tuesday have been EoP or Information Disclosure vulnerabilities. However, this is the second NTFS RCE vulnerability since 2022 and the second in 2025. The first, CVE-2025-24993, patched in the March 2025 Patch Tuesday release, was exploited in the wild as a zero-day.
CVE-2025-54910 | Microsoft Office Remote Code Execution Vulnerability
CVE-2025-54910 is a RCE in Microsoft Office. It was assigned a CVSSv3 score of 8.4 and is rated critical and assessed as “Exploitation Less Likely.” An attacker could exploit this vulnerability by convincing a target to open a specially crafted Office document. Additionally, the advisory notes that exploitation is possible through Microsoft Outlook’s Preview Pane. Successful exploitation would grant the attacker RCE privileges on the target system. For users of Microsoft Office LTSC for Mac 2021 and 2024, the advisory states that updates are not yet available, but will be released soon.
CVE-2025-54897 | Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2025-54897 is a RCE vulnerability in Microsoft SharePoint. It was assigned a CVSSv3 score of 8.8 and is rated important and assessed as “Exploitation Less Likely.” In order to exploit this flaw, an attacker would need to be authenticated as any user and privileged accounts, such as admin or other elevated privileges are not necessary to exploit this flaw. Once authenticated, an attacker could either write arbitrary code or use code injection to execute code on a vulnerable SharePoint Server to gain RCE.
CVE-2025-55224 | Windows Hyper-V Remote Code Execution Vulnerability
CVE-2025-55224 is a RCE in Windows Hyper-V. It was assigned a CVSSv3 score of 7.8, rated as critical and assessed as “Exploitation Less Likely.” According to the advisory, an attacker who is able to win a race condition could traverse from the guest hosts security boundary in order to execute arbitrary code on the Hyper-V host machine. While the attack complexity for this vulnerability is high, the impact would be significant for an attacker who is able to successfully exploit this vulnerability.
CVE-2025-54091, CVE-2025-54092, CVE-2025-54098, CVE-2025-54115 | Windows Hyper-V Elevation of Privilege Vulnerabilities
CVE-2025-54091, CVE-2025-54092, CVE-2025-54098, CVE-2025-54115 are EoP vulnerabilities in Windows Hyper-V, Microsoft’s virtualization product. CVE-2025-54091, CVE-2025-54092, CVE-2025-54098 were assigned a CVSSv3 score of 7.8 while CVE-2025-54115 was assigned a CVSSv3 score of 7.0. CVE-2025-54098 was assessed as “Exploitation More Likely” while the remaining three flaws were assessed as “Exploitation Less Likely.”
A local, authenticated attacker could exploit these vulnerabilities to elevate to SYSTEM privileges, though in order to exploit CVE-2025-54115, an attacker would first need to win a race condition, which is what contributed to its lower CVSS score.
Tenable Solutions
A list of all the plugins released for Microsoft’s September 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
- Microsoft's September 2025 Security Updates
- Tenable plugins for Microsoft September 2025 Patch Tuesday Security Updates
Join Tenable's Research Special Operations (RSO) Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.
- Exposure Management
- Vulnerability Management



