ProxyNotShell, OWASSRF, TabShell: Patch Your Microsoft Exchange Servers Now

Several flaws in Microsoft Exchange Server disclosed over the last two years continue to be valuable exploits for attackers as part of ransomware and targeted attacks against organizations that have yet to patch their systems. Patching the flaws outlined below is strongly recommended.
Background
Over the last few years, threat actors from all walks of life have begun to favor a class of exploits found in Microsoft Exchange Server, a popular mail server used by tens of thousands of organizations around the world.
This shift began following the disclosure of ProxyLogon (CVE-2021-26855) and related vulnerabilities (CVE-2021-26857, CVE-2021-26858, CVE-2021-27065) in March 2021. These vulnerabilities were originally exploited in the wild as zero days by a state-sponsored threat actor known as HAFNIUM.
In August 2021, following the disclosure of another set of Exchange Server vulnerabilities, dubbed ProxyShell, attackers actively searched for vulnerable Exchange Server instances to target. Both ProxyLogon and ProxyShell continue to be exploited over a year after they were disclosed and patched.
Recent Exchange Server bugs
ProxyNotShell disclosed in September 2022 with no patches, just mitigation guidance for two months
At the end of September 2022, researchers at GTSC Cybersecurity Technology Company Limited publicly disclosed two zero-day vulnerabilities, collectively referred to as ProxyNotShell (CVE-2022-41040, CVE-2022-41082). At the time, Microsoft acknowledged both flaws, but did not issue a patch for them. Instead, Microsoft issued temporary mitigation guidance for organizations to thwart exploitation until patches became available. Patches for ProxyNotShell were released on November 8, a month after the public disclosure of these flaws.
OWASSRF: Researchers discover a mitigation bypass for ProxyNotShell
In December 2022, researchers at CrowdStrike published details regarding a new exploitation method that bypasses the mitigations for ProxyNotShell dubbed “OWASSRF.” The researchers determined that the mitigation guidance issued for ProxyNotShell only stopped exploitation through the Microsoft Exchange Server Autodiscover endpoint, and that it was still possible to gain remote code execution through the Outlook Web Access (OWA) endpoint. This was made possible through the use of CVE-2022-41080, an elevation of privilege vulnerability, which was patched as part of Microsoft’s November Patch Tuesday release that included fixes for the ProxyNotShell vulnerabilities.
This means that those organizations that did not apply Microsoft’s November Exchange Server patches, but had applied the mitigation guidance from September, were still vulnerable to attacks using OWASSRF.
There are confirmed reports that the Play and Cuba ransomware groups have been leveraging the OWASSRF vulnerability as part of attacks since November 2022.
TabShell: Using OWASSRF to exploit Exchange Remote PowerShell
Researchers at Viettel Security published a separate blog post at the end of December 2022, detailing how they had previously discovered OWASSRF and chained it together with a separate vulnerability. The vulnerability, identified as CVE-2022-41076, is a remote code execution vulnerability in PowerShell that was patched in Microsoft’s December 2022 Patch Tuesday release. Dubbed TabShell, the researchers were able to use both vulnerabilities to break out of the PowerShell sandbox and execute arbitrary PowerShell cmdlets. It can be exploited by abusing a feature of Exchange Server and Exchange Online that allows users to connect to Exchange Servers using remote PowerShell. A public proof-of-concept is available, and some researchers are wondering why it remains “so underrated.”
Exchange TabShell RCE PoC (CVE-2022-41076)
— Janggggg (@testanull) January 9, 2023
(Just copy paste the poc from @vcslab's blog post)
Still wondering why this vulnerability is so underrated xD
PoC script (for copy paste purpose): https://t.co/4jLfIxXkC3https://t.co/nHrJvpxqVn
Over 60,000 Exchange Servers are still vulnerable to ProxyNotShell
At the beginning of January 2023, researchers at the Shadowserver Foundation found that there are over 60,000 accessible Exchange Servers that remain vulnerable to ProxyNotShell. These are Exchange Server instances that have not applied the November 2022 Patch Tuesday updates based on the reported x_owa_version header.
Patching behavior shows decline in number of vulnerable Exchange Servers
In November 2022, as part of the Patch Tuesday release, Tenable published plugins to address multiple Exchange Server flaws, including ProxyNotShell and what we now know as OWASSRF. Looking at anonymized scan data from these plugins from a subset of our customer base, our findings from November 2022 through the first week of January show that, while there has been a slow and steady decline in the number of vulnerable Exchange Servers, a decent number of Exchange Servers still remain vulnerable (see chart below).
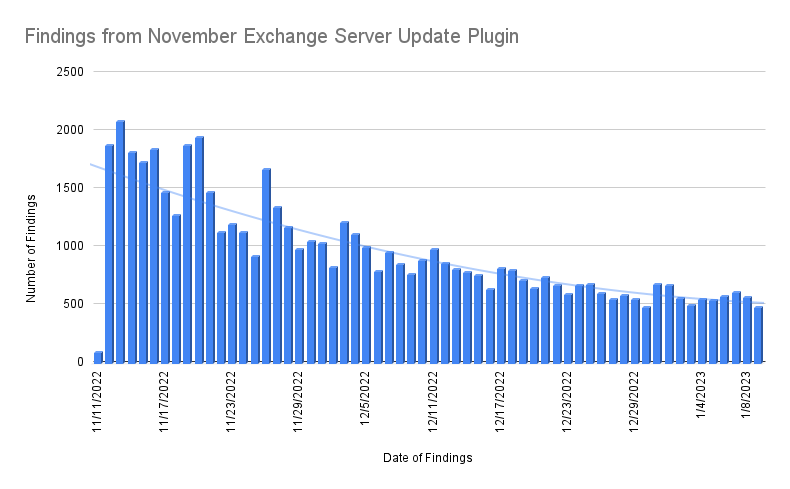
Addressing the confusion surrounding being vulnerable to OWASSRF
One confounding factor for security professionals is how to determine whether their organization is vulnerable to ProxyNotShell and OWASSRF. To try and clear things up, we’ve put together a table outlining mitigations and patches and the status of whether or not your organization is vulnerable to either flaws.
How to tell if your organization is vulnerable to ProxyNotShell and OWASSRF
| Did you apply the September ProxyNotShell mitigations? | Did you apply the November patches? applied | Then your organization is… |
|---|---|---|
| Yes | No | Vulnerable to OWASSRF |
| No | No | Vulnerable to ProxyNotShell and OWASSRF |
| No | Yes | Not vVulnerable to ProxyNotShell or OWASSRF |
| Yes | Yes | Not vVulnerable to ProxyNotShell or OWASSRF |
Entry points for attackers via Microsoft Exchange Server
To summarize, here are the key vulnerabilities in Microsoft Exchange Server that have been used as an entry point for a variety of attackers over the last two years:
| CVE | Description | Nickname | Notes |
|---|---|---|---|
| CVE-2021-26855 | Microsoft Exchange Server Server Side Request Forgery Vulnerability | ProxyLogon | Exploitable without Authentication |
| CVE-2021-34473 | Microsoft Exchange Server Remote Code Execution Vulnerability | ProxyShell | Exploitable without Authentication |
| CVE-2021-34523 | Microsoft Exchange Server Elevation of Privilege Vulnerability | ProxyShell | Exploitable without Authentication |
| CVE-2021-31207 | Microsoft Exchange Server Security Feature Bypass Vulnerability | ProxyShell | Authentication Required |
| CVE-2022-41040 | Microsoft Exchange Server Elevation of Privilege Vulnerability | ProxyNotShell | Authentication Required |
| CVE-2022-41082 | Microsoft Exchange Server Remote Code Execution Vulnerability | ProxyNotShell | Authentication Required |
| CVE-2022-41080 | Microsoft Exchange Server Elevation of Privilege Vulnerability | OWASSRF | Authentication Required |
Please note that at the time this blog post was published on January 31, 2023, we have not seen any confirmed reports of TabShell being used by attackers.
Tenable audit for Exchange Server mitigations
Tenable Research’s Audits and Compliance team published an audit file that can be used by organizations to audit whether or not Microsoft’s ProxyNotShell mitigations remain in place.
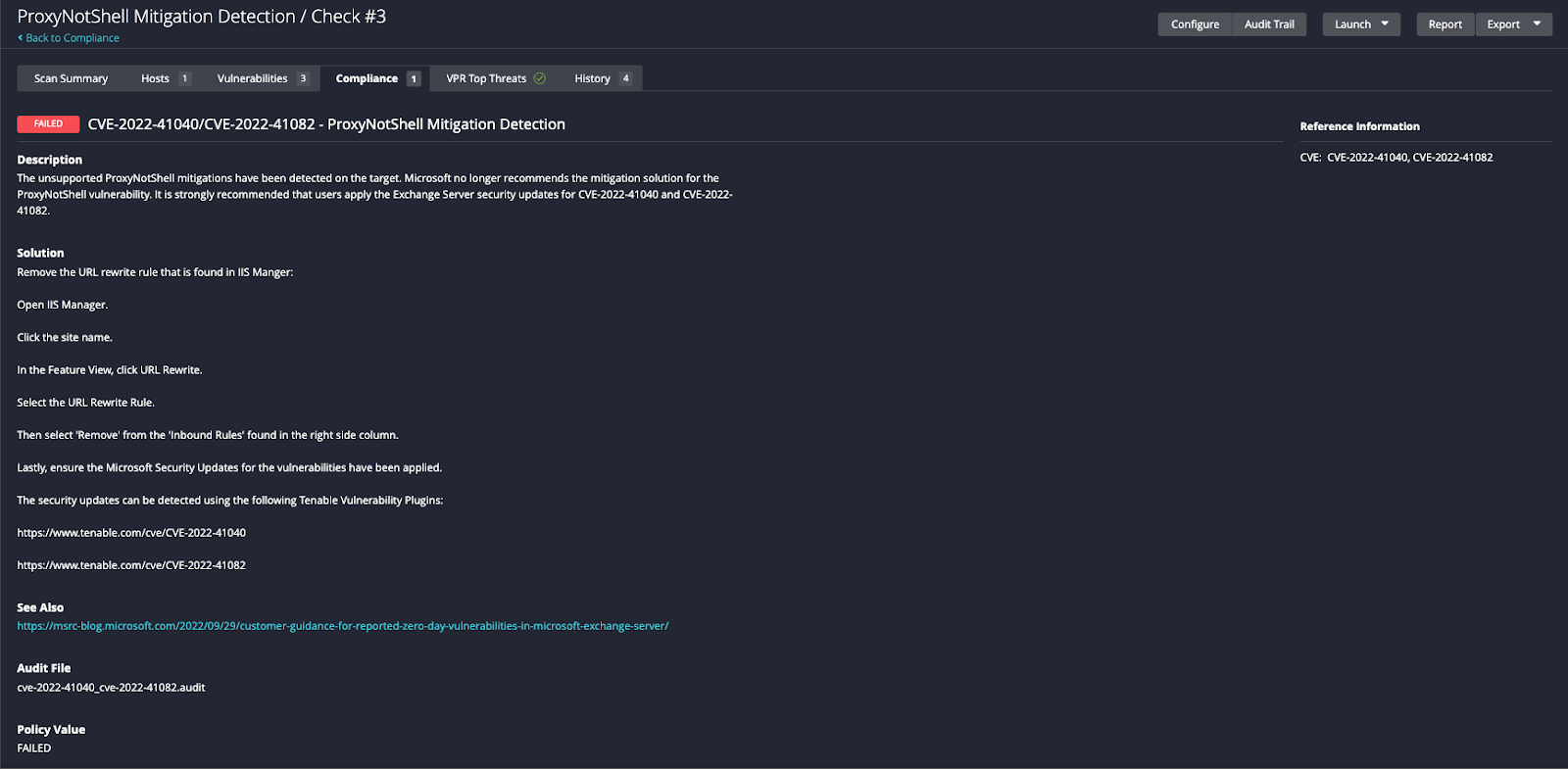
An example of a failing target where the ProxyNotShell mitigations were found
As a reminder, organizations remain vulnerable to the OWASSRF and ProxyNotShell exploit chain if the November 2022 Exchange Server patches have not yet been applied and even if the ProxyNotShell mitigations are still in place.
Exchange Server flaws remain a valuable asset for attackers in 2023 and beyond
Based on the historical exploitation of Microsoft Exchange Server, our primary concern is that there are still far too many systems that remain vulnerable to a number of Exchange Server flaws, making them ripe targets for ransomware groups and nation state actors to exploit. It is why legacy vulnerabilities across a number of products, including Exchange Server, remain popular with attackers, despite patches being available for months if not years.
While we recognize that patching Exchange Server is far from an easy or simple endeavor, it is one that will be of significant benefit to organizations in the long run.
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities can be found here. This link uses a search filter to ensure that all matching plugin coverage will appear as it is released.
Get more information
- Exposure Management


