Tenable Automates NIST Cybersecurity Framework Technical Controls

At RSA this week, Tenable is announcing a new capability in SecurityCenter Continuous View™ that automates and simplifies adoption of the NIST Cybersecurity Framework.
Adoption of the NIST Framework for Improving Critical Infrastructure Cybersecurity (CSF) is growing fast as a way to build a defensible security posture. The CSF is just barely two years old, however Gartner predicts, “By 2020, more than 50% of organizations will use the NIST Cybersecurity Framework, up from the current 30% in 2015.”
The CSF, a best practice security framework, is gaining broad acceptance beyond organizations that deliver critical infrastructure. The National Association for Corporate Directors has recommended that “directors set the expectation that management has considered the CSF in developing the company’s cyber-risk defense and response plans.” The above mentioned Gartner report also stated, “Organizations that choose to ignore the framework due to its voluntary nature may be missing a strategic planning opportunity.”
The CSF Core contains five functions to improve security posture. These functions (Identify, Protect, Detect, Respond, and Recover) are the “high level view,” and each function contains numerous categories and subcategories that drive particular security outcomes. These categories and subcategories can be thought of as “controls” or “control objectives” used in other security and compliance frameworks.
There are two control types: administrative and technical. Administrative controls are typically procedural and can be implemented and audited using manual processes. In contrast, technical controls typically deal with huge amounts of fast moving data. Therefore, automation is necessary to implement and audit the technical controls, which account for about half of all of the controls listed in the CSF.
If your organization has adopted CSF or plans to, how will you automate its controls and track your progress and success?
SecurityCenter CV supports over 90% of the CSF technical controls and builds them into an automated control foundation that helps organizations manage risk and achieve their target security profile.
Tenable SecurityCenter CV supports over 90% of the CSF technical controls and builds them into an automated control foundation that helps organizations manage risk and achieve their target security profile. SecurityCenter CV includes 20 new interactive dashboards purpose-built to inform security staff with continuous visibility of control operation. If an unexpected condition is reported by a dashboard, staff can quickly drill down to gain the critical context necessary to prioritize further investigation.
For example, the SecurityCenter CV Asset Discovery Dashboard addresses the Identify: Asset Management-1 control, which instructs that physical devices and systems within the organization should be inventoried. SecurityCenter CV uses multiple technologies, including active scanning, passive monitoring, and integration with other IT systems, to accurately inventory hardware assets. The dashboard pictured below provides visibility of new hardware, hosts, network devices, wireless, and mobile devices to give you continuous visibility of all hardware assets on your network.
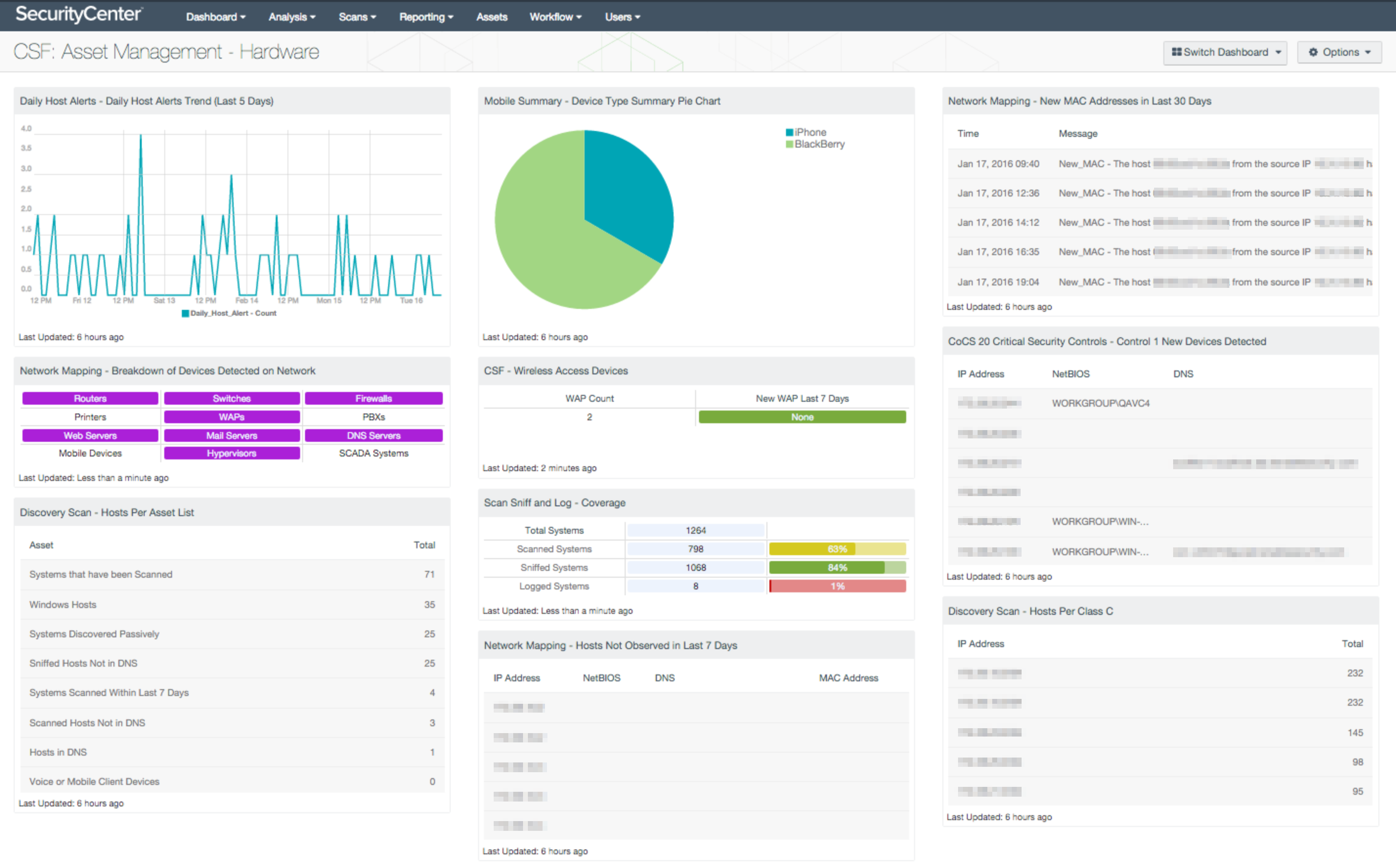
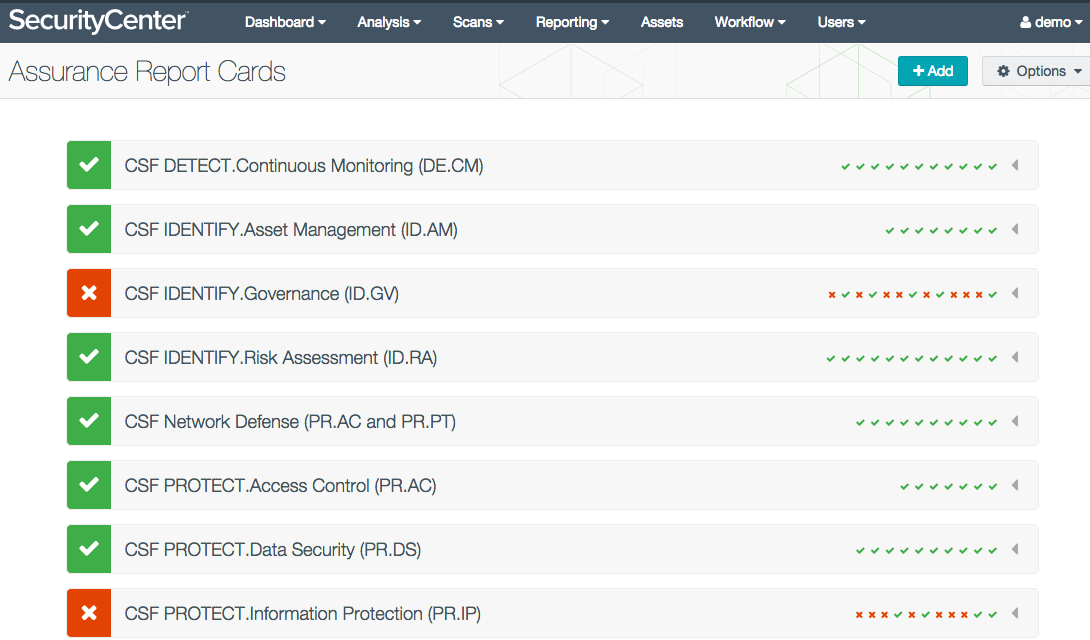
Additionally, eight new Assurance Report Cards (ARCs) communicate CSF conformance to business leaders. ARCs can graphically summarize progress towards the attainment of CSF target profiles. All of the dashboards and ARCs are templates that can be easily tailored and applied to specific business services. The ARC below shows high-level CSF conformance that can be communicated to non-technical stakeholders.
Please take a minute to learn more about how SecurityCenter CV can help you automate and simplify CSF adoption.
- Announcements
- NIST
- SecurityCenter


