by Josef Weiss
November 1, 2022
Ransomware attacks leverage well-known and established software vulnerabilities and poor cyber hygiene. Successful ransomware attacks can cripple an organization with increased costs and lost revenue. This dashboard highlights a path forward with an in-depth focus on cyber hygiene by enabling IT staff to focus on vulnerabilities that could have the most impact to the organization in the event of a ransomware attack.
There are many contributing factors to the upward trend of ransomware. The most important is the large number of software vulnerabilities and misconfigurations, along with Active Directory (AD) weaknesses that enable attackers to escalate privileges. Threat actors leverage poor cyber hygiene to their advantage to gain a foothold and propagate attacks. Ransomware has been very profitable for organized crime, which targets lucrative businesses that can afford large payouts. Many organizations purchase ransomware insurance to mitigate the cost of a breach, but insurers are starting to push back against large payouts if the organization is found to be negligent in following industry security guidance.
Ransomware is a symptom of poor cyber hygiene and security awareness, which can impact operational availability and lead to increased cost. Comprehensive and regularly tested Disaster Recovery and Data Recovery plans go a long way toward combating the effects of ransomware and other threats to the business. This dashboard highlights a path forward with an in-depth focus on cyber hygiene by enabling IT staff to focus on vulnerabilities that could have the most impact to the organization in the event of a ransomware attack. For more information, see the Tenable blog: Focus on the Fundamentals: 6 Steps to Defend Against Ransomware.
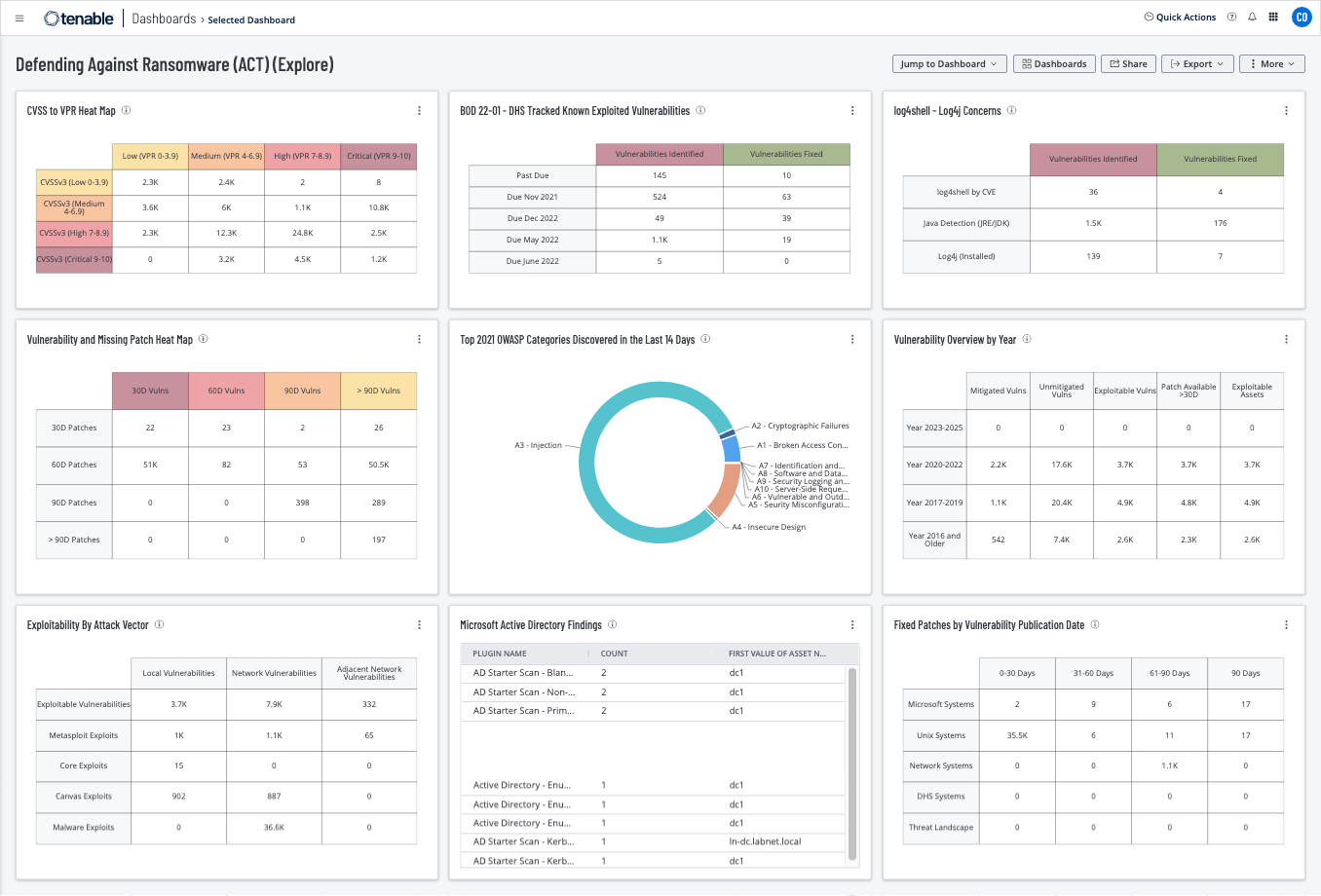
The first row of this dashboard indicates the most significant areas of concern. Displayed in the first column are vulnerabilities that have a published exploit. The middle column displays the current hygiene state. The vulnerability mitigation state is shown in the right column.
Security leaders need to SEE everything, PREDICT what matters most and ACT to address cyber risk and effectively align cybersecurity initiatives with business objectives. Tenable.io discovers and analyzes assets continuously to provide an accurate and unified view of an organization's security posture. The requirements for this dashboard are: Tenable.io Vulnerability Management (Nessus, NNM) and Tenable Web Application Security (WAS). The requirements for this dashboard are: Tenable.io Vulnerability Management (Nessus, NNM) and Tenable Web Application Security (WAS).
Widgets
CVSS to VPR Heat Map - This widget provides a correlation between CVSSv3 scores and Vulnerability Priority Rating (VPR) scoring for the vulnerabilities present in the organization. The CVSSv3 scores are the standard scoring system used to describe the characteristics and severity of software vulnerabilities. Tenable's VPR helps organizations refine the severity level of vulnerabilities in the environment by leveraging data science analysis and threat modeling based on emerging threats. Each cell is comprised of a combination of cross-mapping of CVSS & VPR scoring. Using a heat map approach, the filters begin in the left upper corner with vulnerabilities that present least risk. Moving to the right and lower down the matrix the colors change darker from yellow to red as the risk levels increase. Tenable recommends that operations teams prioritize remediation for risks in the lower right corners, and then work towards the upper left cells. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Vulnerability and Missing Patch Heat Map - This widget provides a correlation between Patch Published dates and Vulnerability Published dates for the vulnerabilities present in the organization. The Patch Published dates indicate when a vendor published a patch for the vulnerability, while the Vulnerability Publication date is the date when the vulnerability definition was first published (for example, the date the CVE was published). Each cell consists of a cross-mapping of Patch Publication and Vulnerability Publication. The widget uses a heat map approach, with the upper left corner containing the vulnerabilities and patches that have been published in the last 30 days. Moving lower and to the right in the matrix, the colors change from yellow to red as the risk levels increase. Tenable recommends mitigating risks shown in the lower right cells and working towards the upper left cells, since the lower right cells represent missing patches associated with vulnerabilities that have been present within the organization for a longer time period. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Exploitability by Attack Vector - This widget displays three columns of exploitable vulnerabilities by the CVSS Exploitability Metric Vectors: AV:N (Network), AV:A (Adjacent Network), and AV:L (Local). A row for each exploit framework is provided. The CVSS metric vector specifies the pathway that can be used to exploit the vulnerability. Vulnerabilities that can be exploited remotely are a greater risk, since there is a global threat vector. Vulnerabilities that can be exploited locally require local access to the system through another mechanism, such as an authorized user or a remote-execution vulnerability. Threat vectors are designated as Network (AV:N), Adjacent (AV:A), and Local (AV:L). Security analysts can effectively reduce risk to the organization by prioritizing remediation on vulnerabilities that can be remotely exploited from known exploits and exploit frameworks. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
BOD 22-01– DHS Tracked Known Exploited Vulnerabilities - This widget displays vulnerability status counts for DHS tracked known vulnerabilities derived from the CISA Known Exploited Vulnerabilities Catalog. The widget uses the CVE filter to exactly match the CVEs included in the CISA Known Exploited Vulnerabilities Catalog and sorts the results in rows by: past due vulnerabilities The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Top 2021 OWASP Categories Discovered (Last 14 Days) - This widget displays the percentages of active Web Application vulnerabilities from Tenable.io WAS by OWASP category for 2021. The requirement for this widget is: Tenable Web Application Security (WAS).
Microsoft Active Directory Findings - This widget displays a vulnerability summary for assets that contain any vulnerabilities related to Active Directory. This widget uses the application CPE filter to cross reference Tenable plugins that contain active_directory, including those from the AD Starter Scan. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
log4shell - Log4j Concerns - This widget widget alerts organizations to potential concerns regarding the Log4j vulnerability. Displayed are the vulnerabilities that are directly associated with the log4shell CVEs (CVE-2021-44228, CVE-2021-44832, CVE-2021-45046, CVE-2021-4104, and CVE-2021-45105) and Log4j installations. Since installing Java v8 is also a requirement to address this exploit, a row is presented of vulnerabilities that are associated with Java, JRE, and JDK. Identifying where Log4j and Java are installed in the organization enables security teams to prioritize remediation. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Vulnerability Overview by Year - This widget tracks vulnerability mitigations by year. Each row covers a time period. The bottom row displays vulnerabilities that were made public from 2016 and earlier. The ascending rows display vulnerabilities from more recent time periods, up to the current year. The Mitigated column displays the total number of mitigated vulnerabilities. The Unmitigated column displays the total number of vulnerabilities that have not yet been mitigated. The Exploitable column displays the number of those unmitigated vulnerabilities that are known to be exploitable. The Patch Available column displays the number of unmitigated, exploitable vulnerabilities that have had a patch available for more than 30 days. The Exploitable Assets column displays the number of assets on the network that have unmitigated, exploitable vulnerabilities. Drilling down into the widget provides more details about vulnerabilities discovered by this filter. This information demonstrates the effectiveness of the security program over time. If vulnerabilities from previous years are still present in the environment, security management needs to address why they are not mitigated. The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).
Fixed Patches by Vulnerability Publication Date - This widget displays columns that contain counts of fixed vulnerabilities grouped by the patch publication dates of 0-30, 31-60, 61-90, and more than 90 days ago. Each cell contains a count of fixed vulnerabilities grouped in rows by Microsoft Windows systems, Unix Systems, Network Systems, and vulnerabilities specified in the DHS BOD 22-01 and Tenable's 2021 Threat Landscape Retrospective. This matrix helps organizations map mitigation progress to ensure compliance with organizational policies and Service Level Agreements (SLAs). The requirements for this widget are: Tenable.io Vulnerability Management (Nessus, NNM).