CVE-2020-12695: CallStranger Vulnerability in Universal Plug and Play (UPnP) Puts Billions of Devices At Risk

Universal Plug and Play (UPnP), a ubiquitous protocol used by “billions of devices,” may be vulnerable to data exfiltration and reflected amplified TCP distributed denial of service (DDoS) attacks.
Background
On June 8, researcher Yunus Çadirci published an advisory for CallStranger, a vulnerability in the Universal Plug and Play (UPnP) protocol. UPnP is currently managed by the Open Connectivity Foundation (OCF). As its name implies, UPnP is a protocol designed to allow a variety of networked devices to universally communicate with each other without any special setup or configuration.
Because of its ubiquitous nature, UPnP is used by a wide variety of devices, including personal computers, networking equipment, video game consoles and internet of things (IoT) devices such as smart televisions. As a result, Çadirci says this particular vulnerability potentially affects “billions of devices.”
Analysis
CVE-2020-12695 is a server-side request forgery (SSRF)-like vulnerability in devices that utilize UPnP. The vulnerability exists due to the ability to control the Callback header value in the UPnP SUBSCRIBE function.
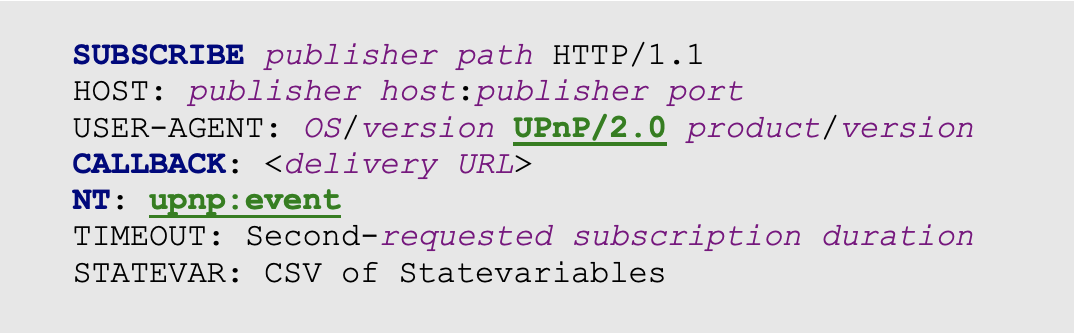
Source: CallStranger Technical Report
The SUBSCRIBE function is part of the UPnP standard that allows devices to monitor changes in other devices and services. For example, the PoC published on GitHub shows port 2869 for Microsoft’s Xbox One — which is used to monitor device changes on the network for features like media sharing — as vulnerable.
In order to exploit the flaw, an attacker would need to send a specially crafted HTTP SUBSCRIBE request to a vulnerable device.
An attacker could utilize this vulnerability in the following scenarios:
- Intranet device port scanning to gather additional data from trusted assets within an organization’s LAN, bypassing organizational Data Loss Prevention (DLP) standards.
- Send large amounts of traffic to arbitrary destinations. Targets flooded by the affected devices could crash under the increased network load, resulting in a denial of service (DoS). This is a result of UPnP attempting to establish a TCP handshake with multiple SYN packets for all Callback values in the SUBSCRIBE request.
- Exfiltrate sensitive device data by directing callback information to arbitrary targets.
With the exception of the DoS, these scenarios provide a stealthy method for an attacker to steal data from a compromised network. This sensitive information could potentially open up an organization to further attack.
Proof of concept
The original proof of concept (PoC) created by Çadirci has been added to his GitHub repository.
Solution
Since CallStranger is a protocol-level vulnerability, OCF has made changes to the UPnP protocol specification. Therefore, manufacturers of affected devices are in the process of determining its impact. As a result, we anticipate newly affected devices will be reported and patches will be released over time for devices still receiving product support. Tenable product coverage for this vulnerability can be found in the “identifying affected systems” section below.
At the time this blog post was published, the CallStranger website listed the following operating systems, networking equipment, printers, IoT devices and applications as reportedly vulnerable.
Operating Systems
| Vendor/Model | Version |
|---|---|
| Windows 10 | 10.0.18362.719 |
| Xbox One OS | 10.0.19041.2494 |
Networking Equipment
| Vendor/Model | Version |
|---|---|
| ASUS | RT-N11 |
| Broadcom ADSL | - |
| Cisco Wireless Access Point | WAP150 WAP131 WAP351 |
| D-Link | DVG-N5412SP |
| Huawei | HG255s (HG255sC163B03) HG532e MyBox |
| NEC AccessTechnica | WR8165N |
| Netgear | WNHDE111 |
| Ruckus ZoneDirector | - |
| TP-Link | Archer C50 |
| ZTE | ZXV10 W300 H108N |
| Zyxel | AMG1202-T10B |
Printers
| Vendor/Model | Version |
|---|---|
| Canon Selphy | CP1200 |
| Dell | B1165NFW |
| EPSON EP, EW, XP Series Printers | - |
| Hewlett Packard Deskjet, Photsmart and Officejet ENVY | - |
| Samsung | X4300 |
Internet of Things
| Vendor/Model | Version |
|---|---|
| Canal Digital ADB | TNR-5720 SX |
| Belkin Wemo | - |
| Nokia HomeMusic Media Device | - |
| Panasonic | BB-HCM735 VL-MWN350 |
| Philips | 2k14MTK TV (TPL161E_012.003.039.001) |
| Samsung | UE55MU7000 (T-KTMDEUC-1280.5, BT - S) MU8000 |
| Siemens | CNE1000 |
| Trendnet | TV-IP551W |
Applications
| Vendor/Model | Version |
|---|---|
| ASUS Media Streamer | - |
| LG Smartshare Media | - |
| Sony Media Go Media | - |
| Stream What You Hear | - |
| Ubiquiti UniFi Controller | - |
Identifying affected systems
A list of Tenable plugins to identify this vulnerability will appear here as they’re released. Additionally, the table below lists several Tenable plugins to help identify devices within your network that may have UPnP enabled.
| Plugin ID | Description | Product |
|---|---|---|
| 10829 | UPnP Client Detection | Nessus |
| 35711 | Universal Plug and Play (UPnP) Protocol Detection | Nessus |
| 8061 | UPNP Traffic Detection (Client) | Nessus Network Monitor (NMM) |
| 1948 | UPNP Traffic Detection | Nessus Network Monitor (NMM) |
Get more information
- CallStranger Disclosure Site
- CERT/CC CallStranger Advisory (VU#339275)
- Proof of Concept Code released on GitHub
Join Tenable's Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.
- Vulnerability Management
- Vulnerability Scanning


