Hot Off the Press: the 2015 Cyberthreat Defense Report
Recently, SC Magazine published a compelling article by Craig Shumard, The Security Model Is Broken, in which he declared:
“Our security model is broken and needs to be revamped. If [a major financial institution] – with a budget of $250 million and 1,000 security professionals – cannot stop or detect a major security breach, there is little hope for the rest of us. Unless something changes…”
To underscore Craig Shumard’s point, according to a recent report from Gemalto, in 2014 cyber criminals compromised more than a billion data records in over 1,500 breaches. Compared to 2013, that’s a 49% increase in data breaches and a 78% increase in the number of data records stolen or lost.
How does your security effectiveness compare?
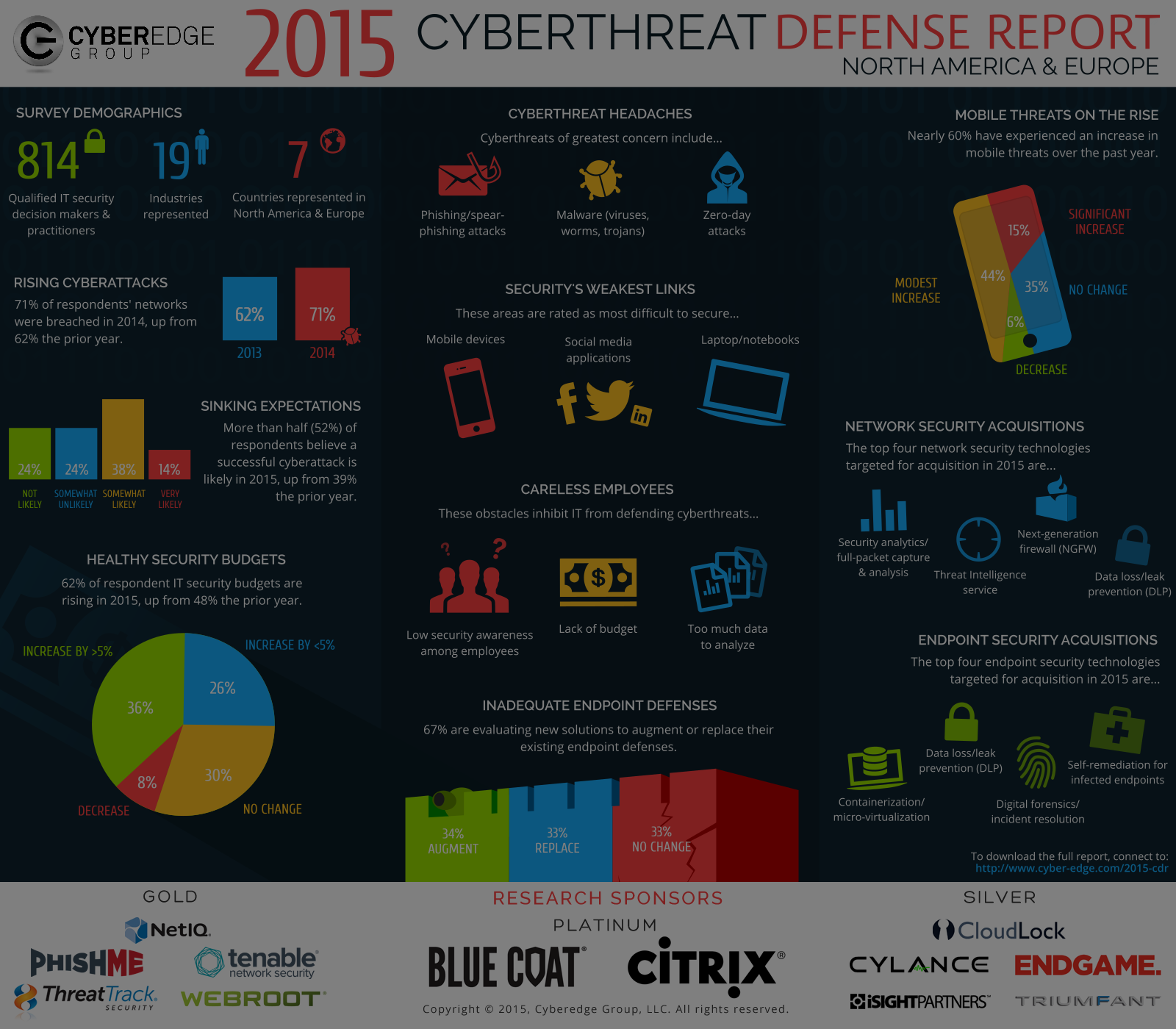
With Gemalto’s sobering numbers in mind, take a look at the newly-released 2015 Cyberthreat Defense Report from the CyberEdge Group (and co-sponsored by Tenable). Based on an analysis of 814 survey responses from North American and European IT security professionals, the report covers a wide range of issues you can use to benchmark your security practices with those of your peers. The report also offers insights into questions you may have such as:
- Where do we have gaps in our cyberthreat defenses, relative to other organizations?
- Have we fallen behind in our defensive strategy to the point where our organization is now the “low-hanging fruit” (i.e., more likely to be targeted by attackers because of our relative weaknesses in cybersecurity defenses)?
- Are we on track with both our approach and progress in addressing traditional areas of concern – such as strengthening endpoint security and reducing our attack surface – as well as tackling newer areas, such as providing mobile security and defending against advanced persistent threats?
- How are our IT security practitioner peers thinking differently about cyberthreats and their defenses, and should we adjust our perspective and plans to account for these differences?
One of the report’s findings that is especially encouraging relates to the growing reliance on continuous network monitoring:
“Half of those surveyed rely on continuous monitoring technologies for discovering network assets, achieving policy compliance, and mitigating vulnerabilities and security misconfigurations. This is a positive trend for the industry, as only 38 percent of respondents conduct full-network scans more often than quarterly.”
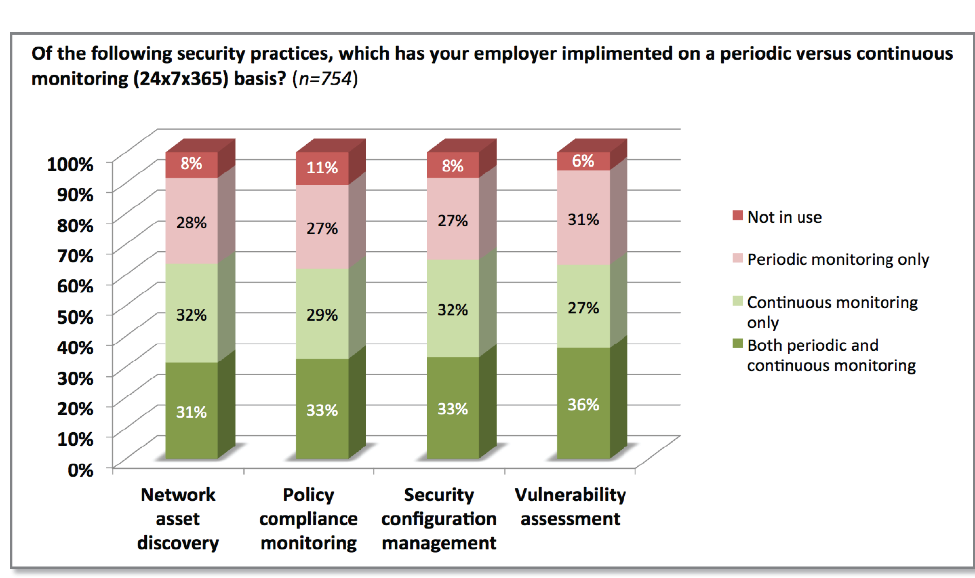
Continuous network monitoring is a process that Tenable recommends for organizations to continually discover, assess, and report on every component of the network against a security policy. Continuous network monitoring helps close gaps in security defenses and strengthens security procedures.
Read the report and hear from the author
For more insights, we encourage you to download and read your own copy of the 2015 Cyberthreat Defense Report. In addition, we invite you to join us at 2pm ET on March 25, 2015 for a webinar discussion with Steve Piper, the report’s co-author, and co-founder and CEO of the CyberEdge Group. We’ll be taking your questions throughout the webinar, so read the report and come prepared for a lively discussion.
- Vulnerability Management
- Vulnerability Scanning



