Transforming Vulnerability Management: Introducing Tenable.io

The vulnerability management industry is at a crossroads: solve long-standing problems and equip security teams for the future, or become obsolete.
As more organizations adopt cloud, mobile, and DevOps as core business enablers, the fundamental concept of an asset changes. This radically impacts how security teams interact with their peers and do their jobs. Even the ownership of assets changes with the rise of DevOps, as security teams must now work with developers, not just IT and network administrators. New thinking is required to deliver a modern approach to vulnerability management (VM) that solves these challenges without penalizing customers for using new technologies like cloud and containers.
Introducing Tenable.io
Tenable has embraced the challenge of transforming vulnerability management. Today we are proud to introduce Tenable.io™, the first vulnerability management platform built for today’s dynamic assets. Using our renowned Nessus® technology, Tenable.io delivers a fresh, asset-based approach that accurately tracks resources and prioritizes vulnerabilities, while accommodating dynamic assets like cloud and containers.
Tenable.io delivers a fresh, asset-based approach
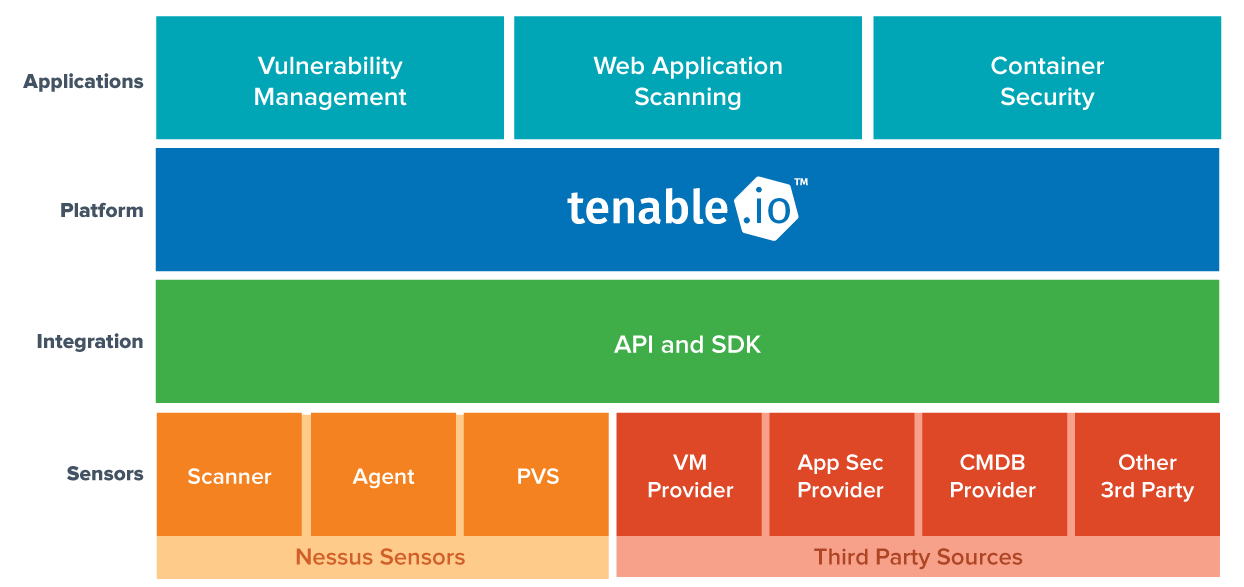
The Tenable.io platform includes state-of-the-art applications for specific business needs, supported by horizontal capabilities like data collection and integration. These applications include not only Tenable.io Vulnerability Management, but also two new products that we are excited to announce: Tenable.io Container Security and Tenable.io Web Application Scanning.
Reorienting VM around a true view of assets
With the rise of transient and short-lived assets – laptops, mobile devices, cloud instances and now containers – Tenable has redefined vulnerability management around true asset identities, rather than IP addresses. This approach permeates the entire Tenable.io experience – from how it tracks vulnerabilities to how you license the product.
Tenable has redefined vulnerability management around true asset identities, rather than IP addresses
We addressed the asset challenge through an advanced asset fingerprinting algorithm. Think of it as facial recognition software for IT – no matter where assets come from and go to, Tenable.io sees their true identity. This allows security teams to have a fact-based dialogue with their peers in IT, networking and development about the organization’s overall security posture and what to remediate.
Customer-friendly licensing
Given these shifts in how organizations are managing assets and vulnerabilities, conventional licensing approaches are ill-suited to the modern environment. In their place, we are pleased to introduce Elastic Asset Licensing.
With Elastic Asset Licensing, each asset consumes just a single license unit
This industry-first model enables you to accurately license all your assets. Each asset consumes just a single license unit, even those with multiple IP addresses like laptops, mobile devices and cloud instances. This elastic model also allows product usage to continue when license counts are temporarily exceeded, and automatically recovers licenses for rarely scanned assets or one-time bursts. If you’ve ever had to “hoard” IP addresses with another VM solution, your frustration is over.
Moreover, we don’t nickel-and-dime customers the way some cloud VM vendors do. You pay only for the business applications you use and nothing more. All of the rich platform capabilities are included at no extra cost – including our popular Nessus sensors. You receive full and unfettered use of an unlimited number of internal and external scanners, agents and other data collection components.
Expanding vulnerability management to containers
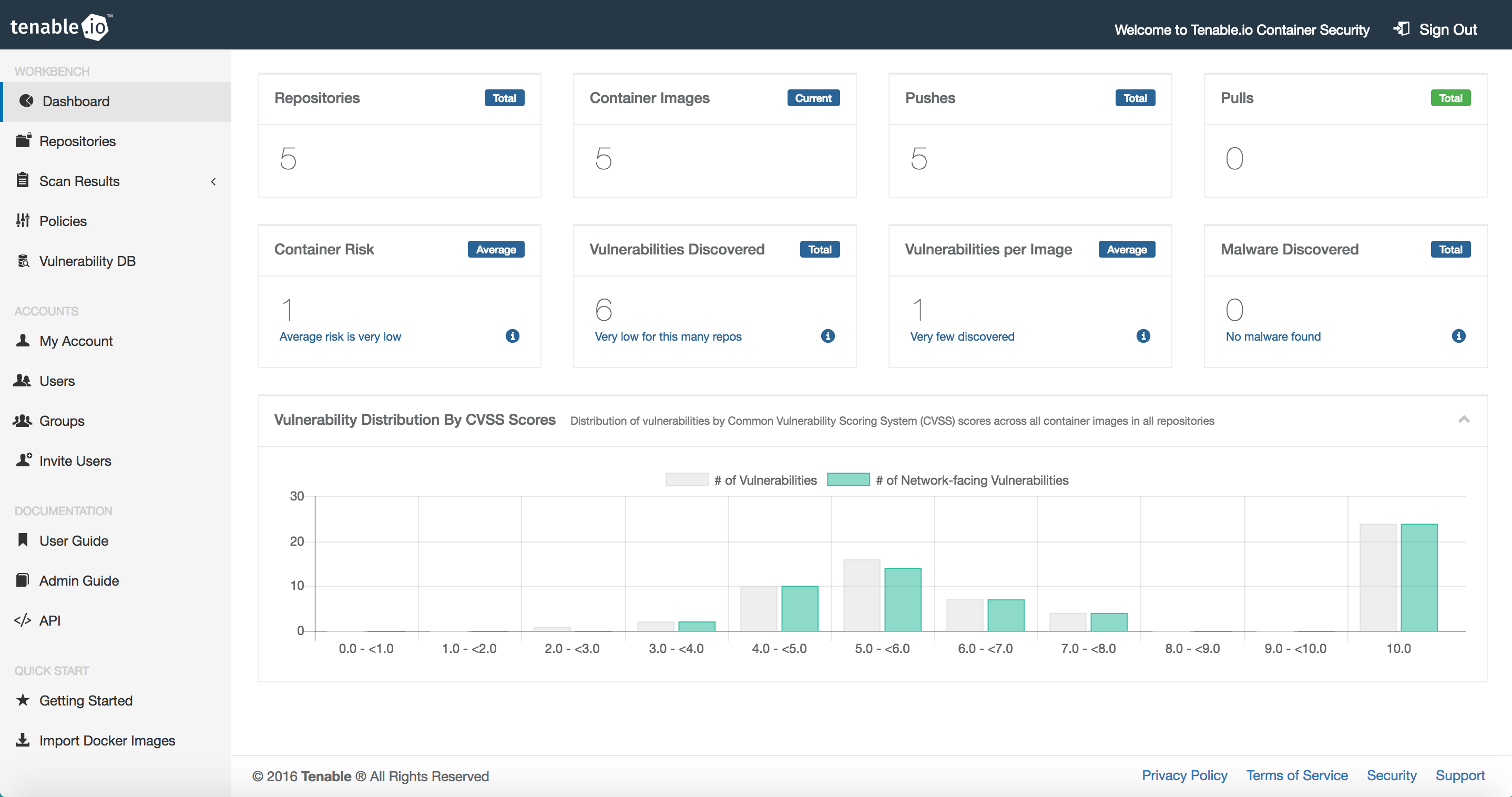
Tenable.io Container Security, based on our recent acquisition of FlawCheck, continuously assesses container images for vulnerabilities, malware and enterprise policy compliance. By bringing security into the container build process up-front through integration with CI/CD systems (continuous integration/continuous deployment), you can gain visibility into the hidden risks in containers and remediate them before they reach production – all without slowing innovation cycles. We are now conducting early customer engagements with Tenable.io Container Security and plan to release it in April.
Web application security for your custom apps
We are also delighted to introduce Tenable.io Web Application Scanning. This offering provides comprehensive vulnerability scanning for modern web applications. Its accurate vulnerability coverage minimizes false positives and negatives, ensuring security teams understand the true risks in their web applications. And it does so in an automated and affordable way so you can cover all of your web apps. A customer beta program begins in March; if you’d like to participate, please contact us.
Openness and integration
It’s more critical than ever to have one place for all vulnerability data, no matter where it comes from. Solutions that only accept and manage their own data are doing a disservice to customers who need complete visibility.
It’s more critical than ever to have one place for all vulnerability data, no matter where it comes from
That’s why Tenable.io includes pre-built integrations with complementary systems like password vault, patch management and mobile device management (MDM) solutions. We are partnering with a wide range of vendors, many of whom are highlighted on our Works with Tenable.io page. Tenable.io also offers a well-documented API and easy to use software development kit (SDK), to enable additional integrations that help your security program leverage the full value of vulnerability data.
Looking ahead: the TVM journey
The introduction of Tenable.io is a major step on the journey toward answering some of the toughest questions in security: How secure am I? Is my security posture improving? What are the vulnerabilities and threats I should focus on?
Addressing them requires moving beyond conventional VM to provide deeper context and insight – by capturing more types of data (on assets, vulnerabilities and threats) from more vendors (including other VM vendors) in more ways (including pre-deployment and in production). This is exactly what Tenable.io is designed to do.
Gartner predicts that a new market called Threat and Vulnerability Management (TVM) – part of a broader market of Security Operations, Analytics and Reporting (SOAR) solutions – will develop to meet these needs. Gartner notes that TVM will deliver improved vulnerability management via both enhanced workflow and better prioritization through the use of threat intelligence and business context.
Our vision for the future of VM will deliver on TVM and more. This is an ambitious goal, and one Tenable is uniquely positioned to achieve.
TVM will deliver improved vulnerability management via both enhanced workflow and better prioritization through the use of threat intelligence and business context
More information
We invite you to join us on the journey. To experience Tenable.io today, please register to try the product, or join us for a product introduction webcast on February 28 in the Americas, with subsequent dates in other regions.
You can also learn more in our Tenable.io Frequently Asked Questions, covering Nessus Cloud, SecurityCenter®, pricing/licensing and more.
- Announcements
- Cloud
- Tenable Vulnerability Management