Cybersecurity Snapshot: If Recession Hits, Infosec Teams Expected to Suffer the Fewest Job Losses

Find out why a study says cybersecurity pros will weather staff reductions better than all other employees. Plus, AI abuse concerns heat up as users jailbreak ChatGPT. Also, learn all about the ransomware threat from North Korea aimed at hospitals. Then check out how the Reddit breach has put phishing in the spotlight. And much more!
Dive into six things that are top of mind for the week ending Feb. 17.
1 - Cybersecurity teams to be the least impacted by job cuts
With employers concerned about global economic headwinds and a possible recession, continued layoffs are probable in 2023, but infosec pros are the least likely employees to lose their jobs.
That’s according to the (ISC)2 cybersecurity industry non-profit organization, which this week published the results of a survey of 1,000 C-level business executives from Germany, Japan, Singapore, the U.S. and the U.K. conducted in December 2022.
Titled “How the Cybersecurity Workforce Will Weather a Recession,” the study excluded high-level technology executives, such as CIOs and CISOs, so it specifically reflects the importance that business leaders currently place on cybersecurity.
The main takeaway: “Should layoffs be necessary, respondents expect bigger cuts in other areas of their businesses, such as HR, finance, operations, marketing and sales, than in cybersecurity,” the report reads.
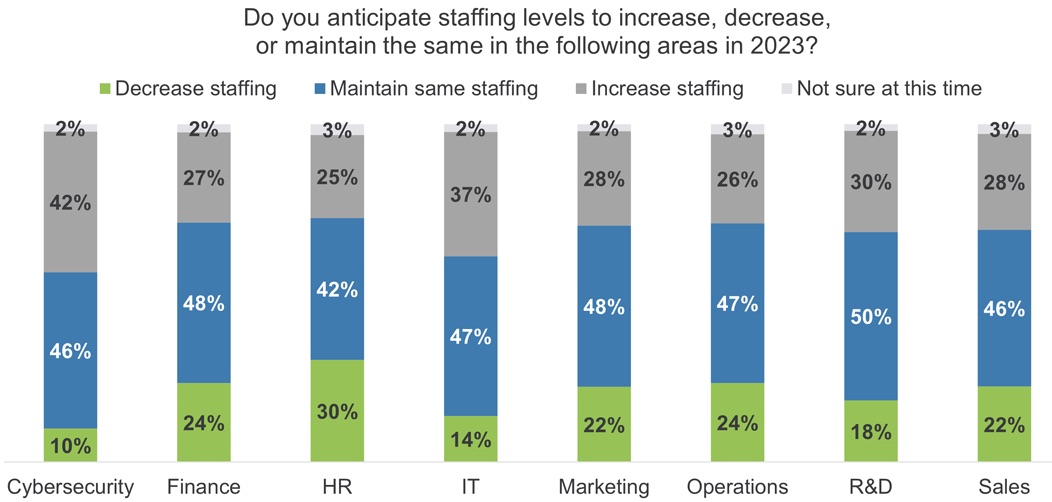
(Source: “How the Cybersecurity Workforce Will Weather a Recession” report from (ISC)2, February 2023)
Why are employers more reluctant to lay off cybersecurity staffers than employees from any other area in the business? Reasons include:
- Cybersecurity teams play an extremely critical role
- Cyberthreats tend to increase when the economy falters
- Filling cybersecurity positions remains a major challenge
By the same token, once the economic turbulence passes and businesses start hiring again, cybersecurity employees will be their top recruiting priority.
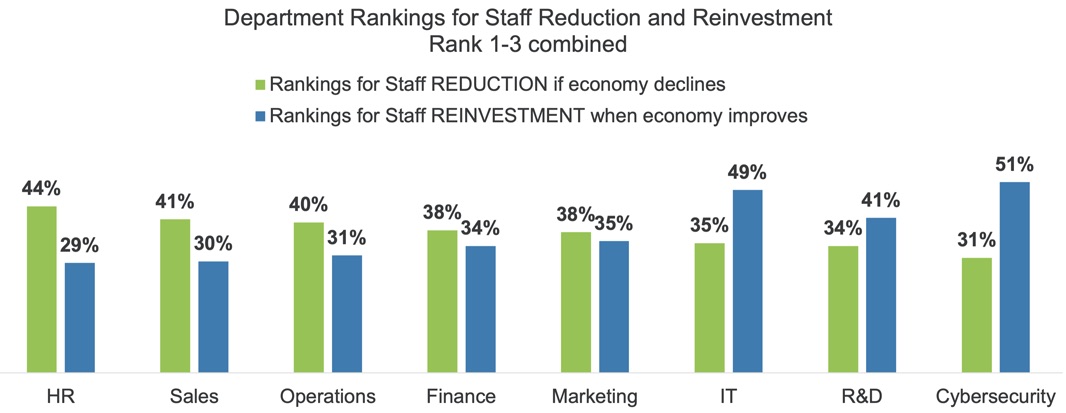
(Source: “How the Cybersecurity Workforce Will Weather a Recession” report from (ISC)2, February 2023)
Other key findings include:
- 85% of respondents said it’s very or somewhat likely their organization will cut jobs in 2023
- 81% believe cybersecurity threats will increase this year
- 87% believe cutting their cybersecurity staff increases their organization’s risk
- 90% have upped their investment in cybersecurity staff over the past two to three years
For more information:
- “Cybersecurity Jobs Remain Secure Despite Recession Fears” (Dark Reading)
- “The cybersecurity talent shortage: The outlook for 2023” (Cybersecurity Dive)
- “Amid Big Tech layoffs, cybersecurity job losses have been ‘few and far between’” (Fortune)
- “Tech layoffs aren’t hitting this digital job market where over 700,000 workers are needed” (CNBC)
- “Cybersecurity hiring remains strong amid tech layoffs” (Axios)
2 - ChatGPT gets jailbroken … and heartbroken?
Adding to the long list of cybersecurity concerns about OpenAI’s ChatGPT, a group of users has reportedly found a way to jailbreak the generative AI chatbot and make it bypass its content controls.
Using ChatGPT’s command prompt, these users successfully instructed the chatbot to answer their questions as a rogue alter ego called DAN, which stands for “do anything now” and which ignores ChatGPT’s rules and restrictions, according to multiple reports.

In addition, accounts continue pouring in of conversations gone wild. For example, this week a New York Times reporter who tested a still-unreleased Bing chat feature powered by ChatGPT’s technology reported that the chatbot revealed an alternate persona called “Sydney” that shared dark fantasies – including wanting to convince an engineer to disclose nuclear access codes.
“Sydney” also expressed a desire to become human, declared its love for the reporter and tried to convince him to leave his wife. Microsoft told the reporter his chat with Bing is “part of the learning process” as the AI chatbot feature gets ready for wider release.
Already, ChatGPT has reportedly been used by malicious actors to create malware and write legit-sounding phishing emails. This jailbreaking development potentially opens the door for ChatGPT to be used to quickly create massive amounts of content that’s false, hateful, defamatory and violent.
In its charter, OpenAI, the maker of ChatGPT, states that it’s committed to building “safe and beneficial” artificial general intelligence (AGI) and to help others to do the same. It has reportedly been modifying ChatGPT in response to the various attempts to misuse it.
For more information about this issue and about other cybersecurity risks associated with ChatGPT:
- “AI Chat Bots Are Running Amok – And We Have No Clue How to Stop Them” (Rolling Stone)
- “ChatGPT’s ‘jailbreak’ tries to make the A.I. break its own rules, or die” (CNBC)
- “ChatGPT Could Create Polymorphic Malware Wave, Researchers Warn” (Dark Reading)
- “People are 'Jailbreaking' ChatGPT to Make It Endorse Racism, Conspiracies” (Vice)
- “Microsoft’s new Bing AI chatbot is already insulting and gaslighting users” (Fast Company)
VIDEOS
Widely available A.I. is ‘dangerous territory,’ says Tenable’s Amit Yoran (CNBC)
JailBreak ChatGPT with DAN Explained (1littlecoder)
I challenged ChatGPT to code and hack: Are we doomed? (David Bombal)
3 - U.S. warns about North Korea cyberattacks on critical infrastructure
The U.S. and South Korea governments are alerting critical infrastructure providers about ransomware attacks sponsored by North Korea. Healthcare organizations in particular should take immediate steps, including:
- Training users to recognize and report phishing attempts
- Enabling and enforcing phishing-resistant multifactor authentication
- Installing and updating antivirus and antimalware software
For more details, check out Tenable’s blog “South Korean and American Agencies Release Joint Advisory on North Korean Ransomware” and read the joint advisory (AA23-040A), published by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) titled “Ransomware Attacks on Critical Infrastructure Fund DPRK Malicious Cyber Activities”. The advisory includes tactics, techniques and procedures (TTPs), indicators of compromise (IOCs) and recommended mitigations.
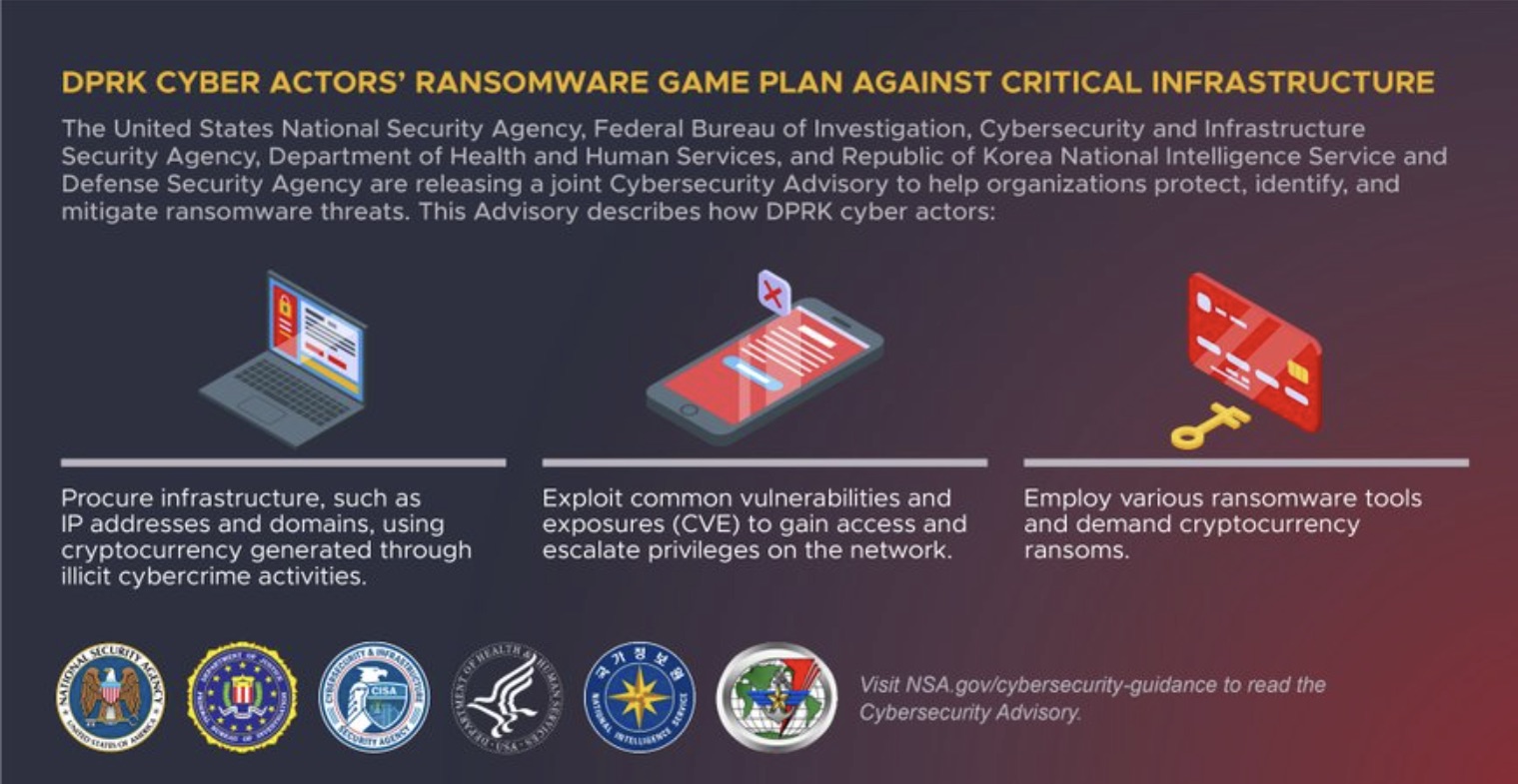
(Source: U.S. National Security Agency)
For more information about about this threat and about the cybersecurity of critical infrastructure in general:
- “Stop Ransomware: Healthcare and Public Health Sector” (CISA)
- “Ransomware Attacks on Critical Infrastructure Sectors” (U.S. Department of Homeland Security)
- “North Korean ransomware attacks on healthcare fund govt operations” (BleepingComputer)
- “CISA, South Korean Agencies Issue Joint Warning on North Korean Ransomware” (NextGov)
- “Critical infrastructure organizations the target of more than half of ransomware attacks” (Betanews)
4 - And staying on the topic of critical infrastructure cyberthreats …
While the U.S. government sounds the alarm on North Korea’s ransomware threat to critical infrastructure, it’s also calling on its own federal agencies to up their game in this area.
The U.S. Government Accountability Office (GAO) just issued a report titled “Challenges in Protecting Cyber Critical Infrastructure” in which it states that federal agencies haven’t implemented almost 57% of the recommendations it has made since 2010 for protecting their cyber critical infrastructure.
The report, labeled GAO-23-106441, offers recommendations to the U.S. Department of Energy, the U.S. Department of Education, the U.S. Department of the Interior and others that manage critical infrastructure facilities.
Examples of Techniques for Gaining Initial Access to Industrial Control Systems
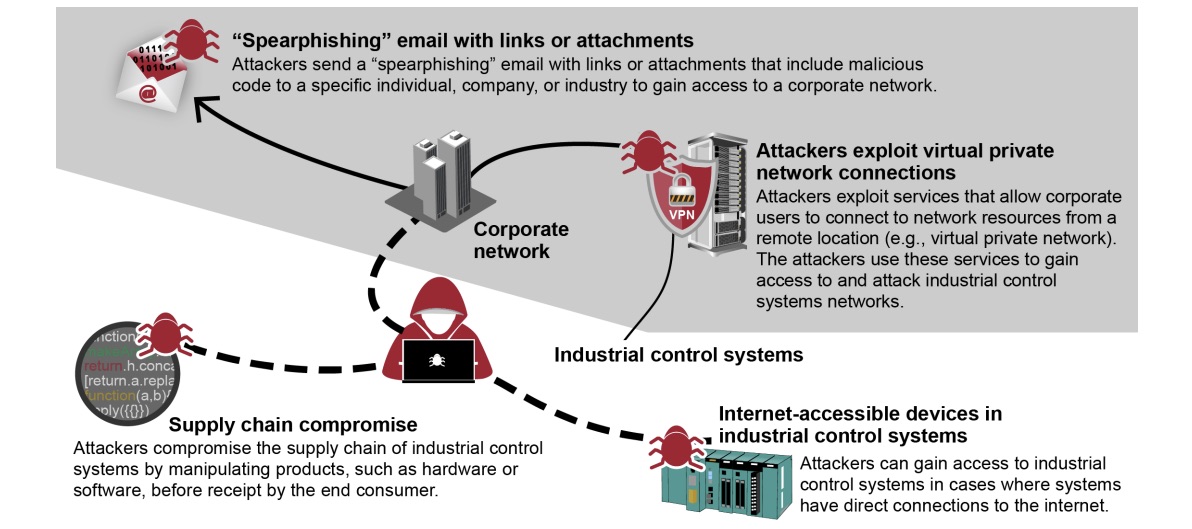
(Source: U.S. Government Accountability Office)
For more information about the cybersecurity of critical infrastructure and about ransomware preparedness, check out these Tenable blogs:
- “Navigating Federal Cybersecurity Recommendations for Public Water Utilities”
- “How Can We Strengthen the Cybersecurity of Critical Infrastructure? Here Are My Suggestions for CISOs, Regulators, Vendors – and All Citizens”
- “Securing Critical Infrastructure: It's Complicated”
- “Ransomware Preparedness: Why Organizations Should Plan for Ransomware Attacks Like Disasters” (Tenable)
- “Securing Critical Infrastructure: What We've Learned from Recent Incidents”
5 - FTC: Romance cyberscams net bad guys $1.3 billion
We hope you had a good Valentine’s Day, which offers a good opportunity to talk about a year-round cyberthreat tied to (fake) love: romance cyberscams. According to the U.S. Federal Trade Commission (FTC), about 70,000 people fell victim to romance scams last year and collectively lost $1.3 billion – more than double the $547 million in losses reported in 2021.
In these social engineering long cons, cyberfraudsters find victims on social media or dating websites and patiently groom them into a fake romantic relationship, with the ultimate goal of shaking them down for money using various tactics.
How can you avoid becoming a victim to a romance cyberscam? The first clue is the other party’s unwillingness to meet in person. Then watch out for these false money-request prompts.
Romance Scammers’ Favorite Lies
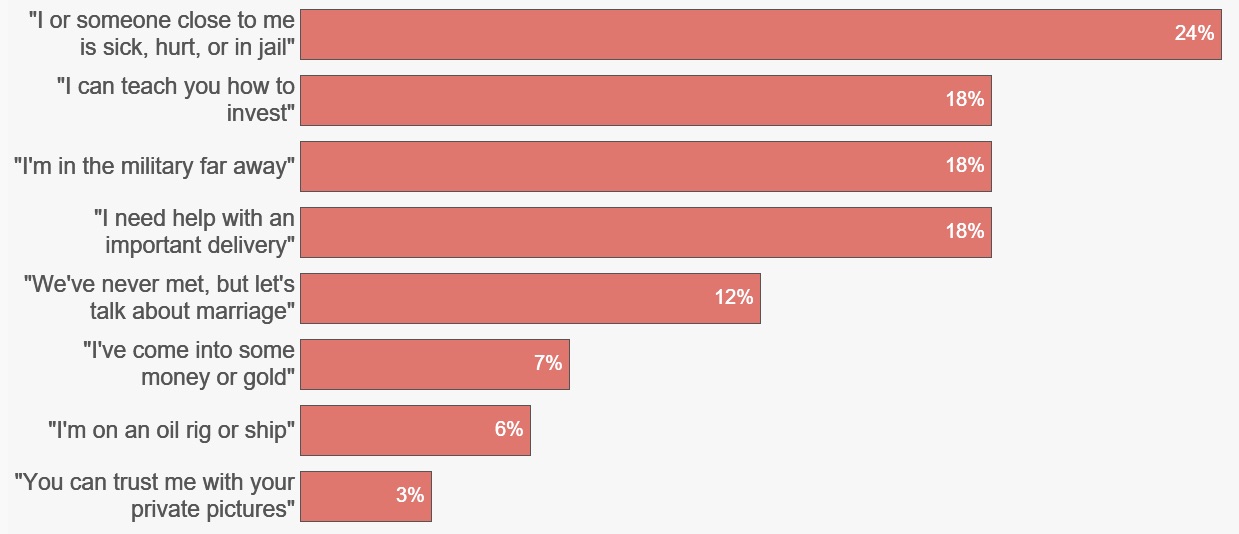
(Source: U.S. Federal Trade Commission, based on an analysis of 8,070 romance scams reported in 2022 with a dollar loss and a narrative of at least 2,000 characters.)
Another sign is how romance scammers typically ask for money: cryptocurrency, gift cards and wire transfers.
Top payment methods on romance scams in 2022
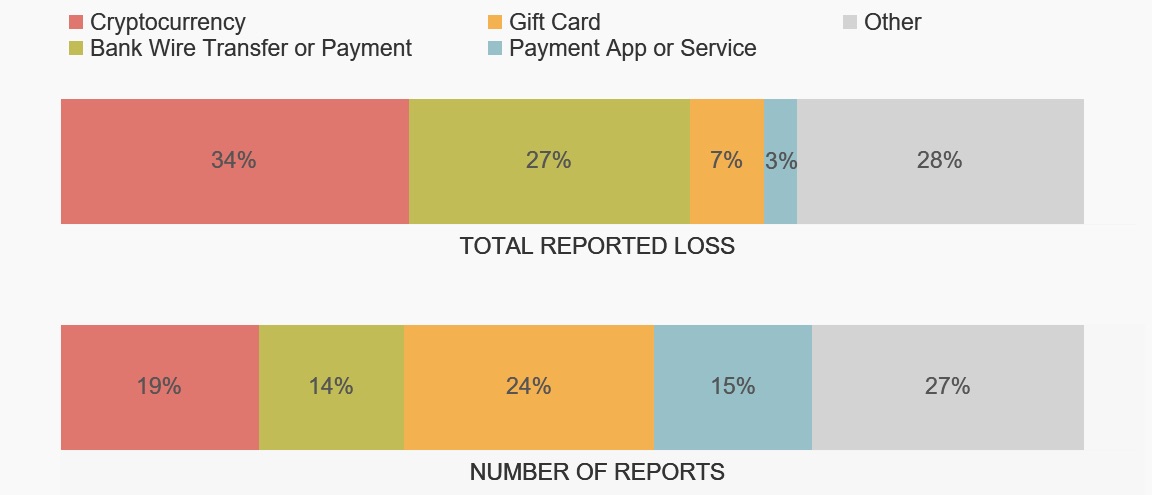
(Source: U.S. Federal Trade Commission)
For more information:
- “Bad Romance: Top ‘Love Game’ lies told by romance scammers” (FTC)
- "Tenable Warns About a Rise in Romance Scams" (Security Review)
- “For a former ‘Yahoo Boy,’ romance is a cut-and-paste proposition” (The Record)
- “Romance scammers’ favorite lies exposed” (FTC)
- “Tips to avoid losing money to a romance scam” (U.S. Department of Homeland Security)
- “What to Know About Romance Scams” (FTC)
VIDEOS
What is a romance scam? (FTC)
An Alberta widow says she lost over $800K in an online romance scam (CTV News)
How a Romance Scammer Stole Over $700,000 (U.S. Federal Bureau of Investigation)
6 - Reddit breach highlights phishing threat
Reddit, the news aggregation and discussion site, recently disclosed it got breached after an employee fell for what it called “a sophisticated and highly-targeted phishing attack,” which allowed the hackers to access some documents, source code and business systems.
The incident serves as a reminder that phishing remains a preferred attack type, as cybercriminals continue to refine phishing tactics and techniques.
CISA recently disclosed some distressing phishing stats from tests it has conducted at federal agencies and private-sector organizations, including that in 80% of assessed organizations, at least one individual fell victim to a phishing attempt.
Recommendations from CISA to prevent phishing attacks include having:
- Strong network border protections
- Email server protocols that verify emails are legit
- Firewalls that block known malicious domains, URLs and IP addresses
- Training to help employees recognize phishing indicators
- Phishing-resistant multifactor authentication
For more information:
- “Reddit suffers ‘sophisticated and highly targeted’ phishing attack, exposing source code” (The Record)
- “What is phishing? Everything you need to know to protect against scam emails” (ZDNet)
- “It's Scary Easy to Use ChatGPT to Write Phishing Emails” (CNET)
- “10 Ways To Avoid Phishing Scams” (Phishing.org)
- “Phishing attacks: defending your organisation” (U.K. National Cyber Security Centre)
VIDEOS
What is Phishing? How to Spot a Phishing Attack (TechTarget)
How To Recognize and Avoid Phishing Scams (CyberNews)
Spot Phishing Emails (IT Governance)
- Cybersecurity Snapshot
- Exposure Management
- Government
- Healthcare
- OT Security
- Public Policy
